Vulnerability management improves the security posture of all IT systems by locating vulnerabilities, implementing security controls to fix or protect those vulnerabilities, and then testing the fixes to verify vulnerability resolution.
Patch management is the subset of vulnerability management that applies to third-party vendors and updates third-party systems using vendor-issued patches.
Despite the close relationship between vulnerability and patch management, confusion exists in the marketplace because some marketing tactics blur the definitions and product names to make better matches for a product’s capabilities. This article will provide an overview of the differences between patch management and vulnerability management, and some guidance for getting started on these critical cybersecurity practices.
Table of contents:
- Key Differences: Patch Management vs Vulnerability Management
- What Is Patch Management?
- What Is Vulnerability Management?
- Should Vulnerability and Patch Management Be Used Together?
- How to Pick a Patch Management or Vulnerability Management Solution
- Bottom Line: Make Investments in Patch and Vulnerability Management
Key Differences: Patch Management vs Vulnerability Management
Patch management is a component of good vulnerability management that focuses on known vulnerabilities in 3rd party vendor systems. Third-party vendor systems include Operating Systems (OS), firmware (software installed on hardware), and applications.
Patch management should be considered a minimum capability for any organization, although it can be very difficult to keep up with patches in sprawling environments. Even consumers and less-technical employees understand patch management to some degree since Microsoft (Windows 10+), Apple (iOS, macOS), and Google (Android, Chrome, etc.) push out automatic patches on a regular basis.
Vulnerability management extends beyond known 3rd-party vulnerabilities to include a broader range of issues, including incorrect installations, configuration errors, security gaps, use of obsolete protocols, architecture issues, and other mistakes. Legacy technologies with known vulnerabilities also fall under vulnerability management and, whether formally acknowledged or not, organizations accept the inherent risk of the vulnerable technologies by continuing to use them.
Many vulnerabilities, such as legacy tech, cannot be fixed using patches. Instead, vulnerability management creates, implements, and maintains compensating controls to protect known vulnerabilities. Virtual patching is a form of compensating controls that use Intrusion Prevention System (IPS) capabilities to shield vulnerabilities, but other technologies can also be deployed such as changing firewall rules, adding network segmentation, and whitelisting. Vulnerability management uses periodic, proactive testing to locate new vulnerabilities and continuously tracks older vulnerabilities.
| Key Differences: Patch and Vulnerability Management | ||
|---|---|---|
| Category | Patch Management | Vulnerability Management |
| Scope | 3rd Party Vendor operating systems, software, firmware | All IT systems, configurations, connections, and security controls |
| Frequency | Tends to be monthly, matching Microsoft’s patching schedule | Could be continuous, but should be at least quarterly (or annually for the smallest organizations) |
| Discovery | Primarily through vendor announcements | Primarily through testing and scans |
| Remediation | Download and apply vendor-created patches | Develop fixes of configuration corrections, compensating controls, and additional layers of security |
| Record Keeping & Reporting | Monthly patches applied, devices with failed patches, time to patch | Current prioritized list of vulnerabilities, compensating control status, vulnerability and penetration scan results |
| Required by Compliance? | Yes | Often required |
What Is Patch Management?
Patch management seeks to maintain IT equipment in optimal condition and add features when available through the acquisition, testing, and application of third-party software updates (aka: patches). Patch management provides the process to prioritize, test, and apply patches for optimal IT condition and minimal operations disruption.
Organizations need to ensure that their patch management process includes all of their systems and not just the common Windows and macOS laptops and desktops. Multiple patch management solutions may be required to cover linux servers, network equipment, installed software, and a full range of devices without operating systems belonging to the internet of things (IoT), medical technology (medtech), industrial control systems (ICS), operations technology (OT), or industrial IoT (IIoT).
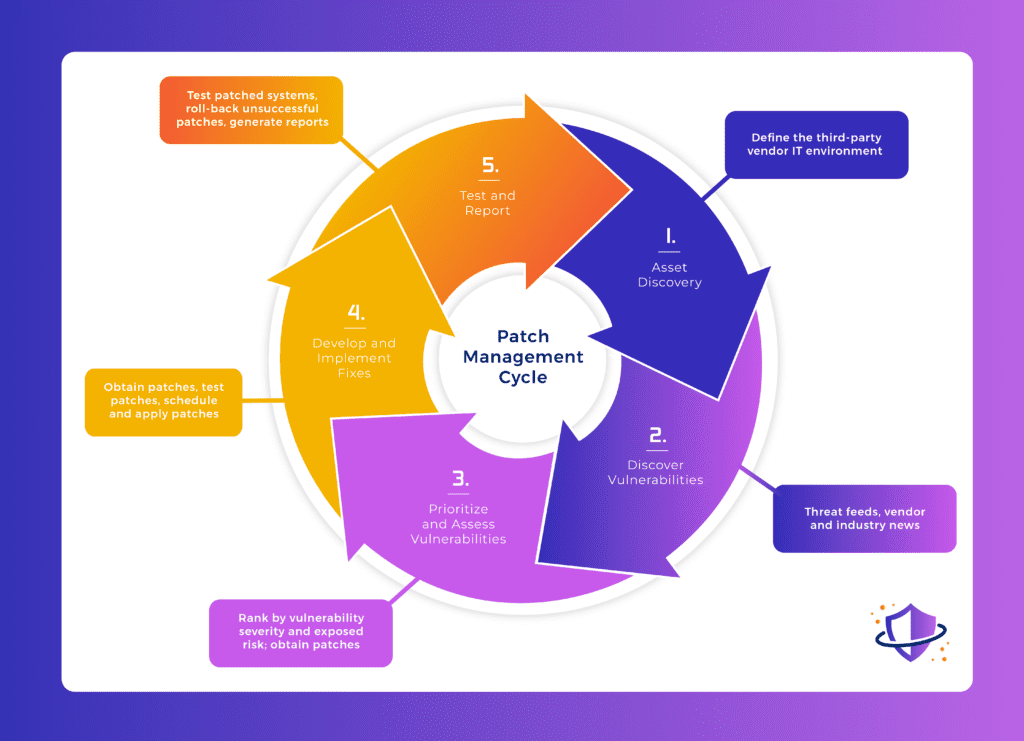
Primary Steps for Patch Management
- Define the IT Environment Through Asset discovery or IT Asset Management (ITAM) to determine endpoints, servers, containers, network equipment, internet of things (IoT), software and other systems to monitor for updates
- Discovery of potential vulnerabilities and available patches through
- Threat feeds
- Vendor emails
- Vendor websites
- Industry websites
- Prioritize and Assess Vulnerabilities
- Prioritize patches based upon severity and the risk to the organization
- Monitor Vendors for the availability of patches to fix vulnerabilities (if no patch is available, engage vulnerability management processes)
- Develop and Implement Fixes
- Acquire patches for updates from legitimate and verified sources
- Test patches and apply test patches
- Assess potential disruptions to operations and notify affected stakeholders in the event of significant disruptions
- Apply patches and monitor for issues
- Test and Report
- Test patched systems to verify proper application of patches
- Roll-back patches in the event of unacceptable disruption, treat as unfixable vulnerability until better patches are released
- Generate reports for internal use and for compliance
See our in-depth guides to Patch Management steps, policies and tools:
- Patch Management Best Practices & Steps
- Patch Management Policy: Steps, Benefits and a Free Template
- Best Patch Management Software & Tools for 2023
- 10 of the Best Patch Management Service Providers
What Is Vulnerability Management?
Similar to patch management, vulnerability management seeks to maintain optimal status for IT equipment, but also extends the principle to all IT systems including network connections, security control systems, and configurations. Vulnerability management requires testing to verify IT system status and to detect configurations errors, security gaps, and other unexpected issues.

Primary Steps for Vulnerability Management
- Define the IT Environment through
- Asset discovery to determine endpoints, servers, containers, network equipment, internet of things (IoT), software and other systems to test and monitor
- Mapping and diagramming network connections, cybersecurity controls, and other systems to test and check
- Discovery of potential vulnerabilities through
- Vulnerability testing and vulnerability scanning (networks, endpoints, cloud systems, containers, applications, etc.)
- Penetration testing
- Threat feeds
- Vendor emails
- Vendor websites
- Industry websites
- Prioritize and Assess Vulnerabilities
- Rank vulnerabilities based upon severity and the risk to the organization
- Which vulnerabilities have patches available
- If no patch is available, which can be corrected with fixes (simple or complex)
- If no patch or fix is available, what compensating controls can be implemented to reduce the risk
- Develop and Implement fixes
- Determine the fix required such as patches, configuration corrections, or compensating controls
- If a fix requires operational disruption, notify affected stakeholders, and schedule downtime
- Implement the fix
- Test and Report
- Test fixes to ensure patches, corrections, or controls were properly installed, no unintended vulnerabilities were created, and the fix works as expected
- Rollback fixes that cause unacceptable operations disruption and go back to development of the fix to try again
- Generate reports for both internal and compliance purposes
For more information on Vulnerability Management consider reading:
- What Is a Vulnerability Assessment? Types, Steps & Benefits
- Penetration Testing vs. Vulnerability Testing: An Important Difference
- 7 Steps of the Vulnerability Assessment Process Explained
- The 8 Best Vulnerability Scanner Tools for 2023
- 12 Top Vulnerability Management Tools for 2023
- Vulnerability Management as a Service (VMaaS): Ultimate Guide
Should Vulnerability and Patch Management Be Used Together?
Many organizations struggle with patch management, so the idea of broadening the requirement to include vulnerability management can be intimidating. However, many vulnerabilities can be easily detected and fixed as long as the organization finds the vulnerability before an attacker can.
Bring-your-own-device (BYOD) adoption helps to illustrate the need for combined use. Consider two laptops, one a corporate device used by a remote worker and the other a consultant’s personal laptop. Both may have an OS vulnerability actively under exploitation, but the patch management tool will only fix the corporate device. The organization will need to use a compensating control, such as network access control (NAC) to detect the unpatched consultant’s laptop and quarantine the device until it is patched.
How to Pick a Patch Management or Vulnerability Management Solution
Patch management tends to be the bare minimum implementation of vulnerability management that an IT team can deploy and still be considered competent. However, just because it needs to be done doesn’t mean all of the pressure and tasks must fall onto an IT or security team.
Automated tools for patch management enable an IT team to let the tool handle the easy updates so the IT team can focus on any problems. Many smaller companies outsource both regular and more difficult patching to managed IT service providers (MSPs).
Organizations looking to improve capabilities to encompass vulnerability management need to carefully evaluate the tools and services under consideration. Many scanning tools, including some labeling themselves as vulnerability management tools, tend to focus primarily on detecting and remediating the unpatched workstations and laptops. While critical, a good vulnerability management solution needs to go further.
Vulnerability management should perform more comprehensive scans of systems, detect misconfigurations, incorporate penetration tests, and other proactive techniques. Some organizations outsource to MSPs, but others prefer to use managed IT security service providers (MSSPs) for their vulnerability management to have a stronger security focus.
Whether outsourcing, selecting a tool, or using inhouse labor, the solution should match the needs. If the service provider or tool only covers Windows and macOS endpoints, the organization will need to find another solution to ensure Linux servers, routers, IoT, and cloud-hosted Kubernetes clusters will be covered.
Organizations need to know the full extent of their needs and the true capabilities of their tools and services to understand what tasks remain unfulfilled. A vulnerability scanning tool or vulnerability management tool that cannot scan for security gaps, open ports, configuration errors, and other non-patching issues will need to be complemented by in-house expertise or consultants that can locate those issues using red teams, penetration tests, and more sophisticated vulnerability scans.
Bottom Line: Make Investments in Patch and Vulnerability Management
Organizations of all sizes should implement the most robust patching or vulnerability management solution their resources allow at the earliest opportunity. Undetected or ignored vulnerabilities will eventually become the target of the increasing volume of cybersecurity attacks. Automated tools and services provide critical help and cost savings by reducing the burden on IT and security teams to manage the easy, repetitive updates. Further investment in expertise to thoroughly test systems and create solutions for the more complex and difficult vulnerabilities will pay off in reduced risk, decreased losses from operations downtime, and less damage from successful attacks.




