A cloud security assessment is a process of analyzing an organization’s cloud infrastructure to identify and mitigate security issues. It also includes detecting vulnerabilities, assessing network exploitation, developing preventative strategies, and establishing proper security levels and governance. To conduct a thorough security assessment, you must first understand your cloud environment, prepare properly, and adhere to key best practices.
Why Do You Need a Cloud Security Assessment?
Assessing your cloud security posture guarantees that the organization correctly configures networks and assets, ensuring they’re secure and free of any current threats. The comprehensive evaluation detects flaws in the organization’s architecture and makes precise recommendations to strengthen defenses and boost future capabilities. Conduct a cloud security assessment if your business needs to:
- Minimize risks: Use a strong cloud-based testing strategies to methodically discover, analyze, and manage any cloud dangers.
- Limit accidental misconfiguration: Implement the specific configuration modifications advised in the assessment. Limit the attack surface as you migrate to the cloud.
- Prevent missed notifications: Enhance your ability to detect and respond to compromises, ensuring that minor errors in your cloud won’t result in major breaches.
- Improve resilience: Follow the assessment team’s recommendations to help your firm recover faster and more efficiently from cloud breaches.
- Boost speed: Perform efficient cloud security testing with parallel scans across several locations, lowering the time for security tests as your cloud infrastructure scales.
- Detect past compromise: Identify deviations from the usual in your cloud configuration that may indicate previous breaches, even if this is not a full compromise evaluation.
- Optimize account management efficiency: Streamline identity architectures to reduce the time your company spends on account and privilege management.
- Ensure compliance: Create an even balance of compliance and security to protect your company from penalties and other adverse effects.
- Enhance financial resilience: Implement proactive strategies that result in significant cost reductions for your company’s cloud operations.
- Scale solutions: Use scalable solutions, either in-house or from trustworthy vendors, to keep up with your company’s cloud growth and objectives.
- Maintain quality: Produce accurate and comprehensible data that clearly shows your company’s cloud security posture.
Understanding the Basics of Cloud Security Assessment
These core aspects of a cloud security assessment should cover the security evaluation process, identity and access, network security, data storage security, incident response, platform security, and workload protection. You should understand the fundamental cloud security elements for a thorough examination of your organization’s cloud infrastructure. This aids in identifying and mitigating any security threats, resulting in a secure cloud environment. Here are some of the basics:
- Comprehensive security evaluation: Conduct interviews and analyze data to evaluate the security measures in place for cloud infrastructure, including existing policies, controls, and potential gaps.
- Identity and access control: Review identity and access control methods, such as user roles, account settings, and key management policies, to verify that only authorized users can access sensitive cloud resources.
- Network defense mechanisms: Examine firewall setups and network segmentation to look for vulnerabilities. Proper segmentation and firewall configurations help to reduce unauthorized access and data breaches.
- Data storage protection: Assess the security of your cloud storage solution or its alternatives, including object storage, block storage, and data snapshots, to prevent unauthorized access and data loss.
- Incident response protocols: Analyze policies and procedures for responding to cloud security incidents. Effective protocols should ensure prompt and efficient response and recovery from breaches.
- Platform services: Check the security settings of advanced cloud services from specific providers to ensure that database services, machine learning platforms, and other specialized services are configured securely.
- Workload protection: Explore the security protocols for virtual servers, hosted containers, functions, and serverless applications. Address every specific requirement of each workload to maintain overall cloud workload security.
Preparing for a Cloud Security Assessment
To prepare for a cloud security assessment, begin by evaluating your existing infrastructure and security measures. This could help you easily define your objectives. Allocate resources and set a dedicated period for assessment. Lastly, evaluate your budget to set limits and see which solutions suit your business. These procedures guarantee a thorough and effective assessment process.

Analyze Existing Infrastructure
Consider your IT stack and evaluate the cloud services in use. Assess the performance and delivery of your security controls. Use suitable cloud assessment tools to thoroughly understand the elements that influence security.
Assess Current Security Measures
Begin by analyzing your current defenses to determine and record the security mechanisms in place in your cloud environment. Next, identify gaps or weaknesses in your current security system to determine which areas require improvement.
Identify & Define Future Security Objectives
Determine the anticipated state of your cloud infrastructure based on your current and future requirements. Establish the security procedures and controls required to attain this future state, ensuring they align with your company objectives.
Allocate Resources
Set aside the required resources to focus on the assessment without jeopardizing your other activities and operations. Dedicate a period to prioritize the assessment so that it receives the required time and focus.
Plan Assessment Duration
Allow 10-15% of your time to map your existing environment, 65-70% to evaluate the current environment, and 10-15% to plan for the future state. Prepare to adapt your timetable based on evaluation results to guarantee thoroughness.
Evaluate Financial Implications
Understand the cost dynamics and budget carefully by choosing evaluation tools that offer good value for money within your budget. Ensure that your resource and security requirements budget align with your financial capacity. Conduct a cost-benefit analysis of the security tools and services. Then, confirm that the solutions you choose are within your budget while still meeting your security requirements.
Cloud Security Assessment Checklist
Use a cloud security assessment checklist to systematically evaluate your cloud security posture and ensure comprehensive protection of your cloud environment. To help you create a checklist for your own security assessment, here’s a snippet of our customizable template. Click the image below to download, make your own copy, and modify it as needed. Then, refer to the section below to understand how to execute the tasks included in the checklist.

Review Existing Policies & Procedures
Implement the methods listed below.
- Assess access control and authentication: Evaluate policies for restricting user access and authentication techniques, such as multi-factor authentication (MFA).
- Examine data protection and encryption: Confirm that rules include data encryption at rest and in transit, as well as data protection procedures.
- Check incident response and disaster recovery: Check that the processes for dealing with security events and recovering from disasters are in place.
- Evaluate auditing and logging: Ensure that policies incorporate logging and auditing techniques for monitoring and recording actions.
- Inspect monitoring and reporting: Verify the rules, including regular monitoring and reporting of security events.
- Ensure regulation compliance: Confirm that policies adhere to relevant industry regulations and standards.
Control Access
Use the following approaches to manage access:
- Limit access to authorized personnel: Make sure that access is confined to only authorized persons.
- Implement authentication: Check that all accounts have activated two-factor authentication or MFA.
- Enforce strong password policies: Maintain that every company user meets strong password standards.
- Perform regular account reviews: Ensure that the admin examines user accounts and deactivates inactive, unauthorized accounts.
- Manage temporary access: Review the protocols for granting and terminating temporary access.
- Implement role-based access controls: Limit access to sensitive data based on employment role.
- Monitor third-party access: Examine the controls and restrictions in place for third-party vendor access.
Secure the Network
Check your network security by doing the following:
- Deploy and configure firewalls: Assess the installation and configuration of firewalls that defend your cloud environment.
- Encrypt data in transit: Use encryption tools to ensure security and prevent unauthorized access to data while it travels between locations.
- Use intrusion detection tools: Confirm the deployment of IDPS to monitor network traffic for suspicious behavior and prevent unwanted access.
- Secure remote access: Employ VPNs to encrypt communications, ensuring secure and private remote access to your network.
- Implement network segmentation strategies: Isolate critical data to lower the risk of illegal access and mitigate potential damage.
Manage Directory Services
To manage directory services, make sure you’ve followed these practices:
- Administer user access and permissions: Ensure that directory services control user access and permissions.
- Update directory services: Schedule regular intervals to review and modify your directory services.
- Restrict access to sensitive data: Verify that your privilege controls limit access to confidential information and systems.
Prevent Data Loss & Ensure Backup
Adopt the following measures:
- Classify sensitive data: Determine and categorize sensitive data to ensure it gets the necessary level of protection and meets regulatory standards.
- Encrypt data at rest: Encrypt sensitive data saved on devices or servers to prevent unauthorized access and preserve data integrity.
- Create a backup policy: Develop a comprehensive backup strategy for speedy and successful data restoration during a disaster or data loss.
- Secure backup storage: Store backups securely offsite. Utilize encryption and physical security measures to prevent unauthorized access and data breaches.
Enhance Security Operations
Apply the listed tasks below:
- Monitor and look into security alerts: Ensure that you regularly monitor and examine security alerts to detect and handle potential risks.
- Report and escalate events: Make sure that you quickly report and appropriately escalate security incidents to allow a fast and successful resolution.
- Respond and remediate incidents: Create a clear methodology for responding to and remediating security incidents to reduce damage and restore normal operations.
Verify Data Encryption Methods
Ensure strong encryption and data protection by carrying out the following actions:
- Secure data at rest: Use industry-standard techniques to encrypt data saved on devices, preventing unauthorized access.
- Safeguard data in transit: Encrypt data as it travels across networks to prevent eavesdropping and unwanted access.
- Manage encryption keys: Establish a comprehensive procedure for managing encryption keys. Confirm that they’re secure and available only to authorized users.
Monitor Cloud Security Status
Follow these procedures:
- Monitor security events and logs: Constantly monitor security events and logs to rapidly detect and respond to potential incidents.
- Conduct compliance audits: Perform audits periodically to ensure that you meet the industry and regulatory standards, simultaneously upholding strong security measures.
- Update security controls: Assess and revise security controls frequently to keep up with the changing threat landscape and improve protective measures.
How to Conduct Cloud Security Assessment in 10 Steps
After creating a cloud security assessment checklist, you can now begin the assessment by setting boundaries, identifying requirements, and defining responsibility divisions. Evaluate potential risks and security measures, choose testing techniques, and run environmental tests. To guarantee effective security, record and report results, develop remediation procedures, review and improve plans, and continue monitoring and evaluations.
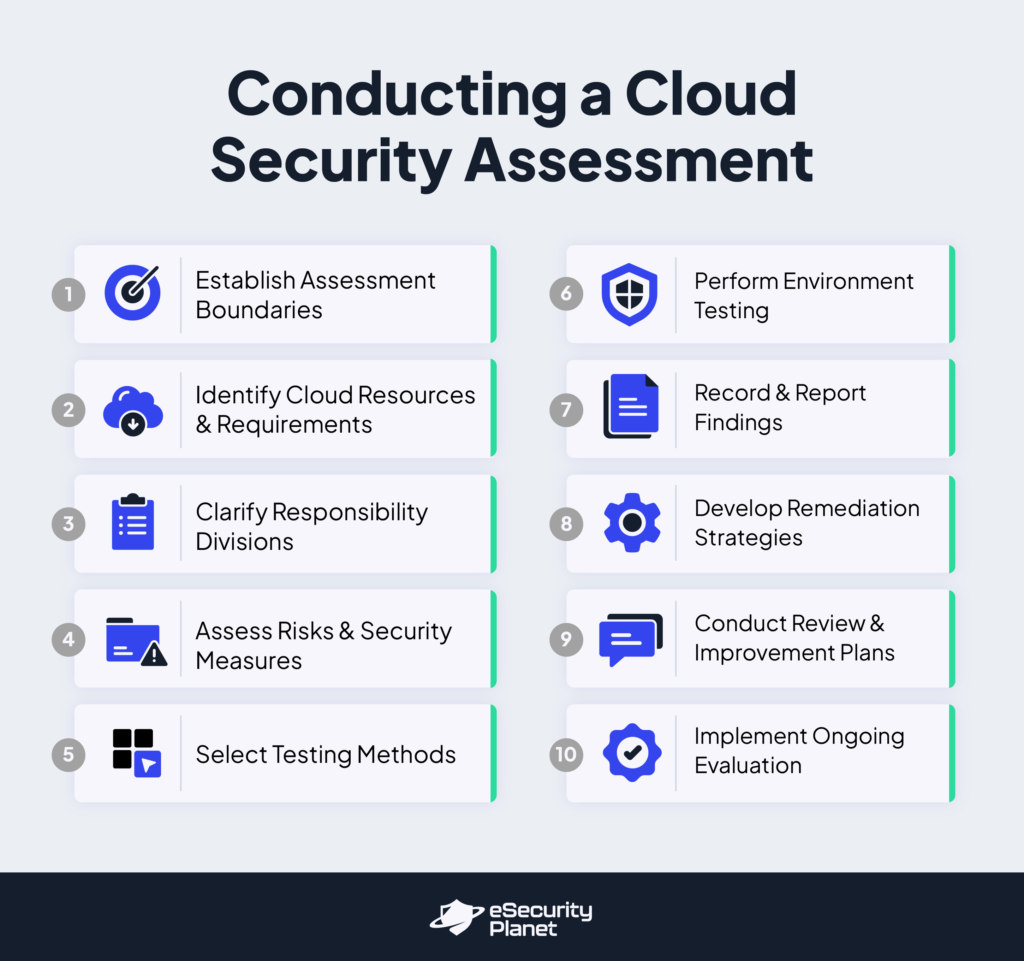
Establish Assessment Boundaries
Define the scope by specifying the cloud assets, apps, and data that will be analyzed. Set specific security goals connected with your organization’s strategy, and use frameworks such as OWASP SAMM or AWS CIS to ensure full coverage. Set boundaries and align with legal requirements and industry standards.
Identify Cloud Resources & Requirements
List all cloud assets, including data and configurations. Examine these assets for vulnerabilities and collect information about setups, network architecture, and access controls. Determine security requirements using compliance frameworks and corporate policies to ensure your cloud infrastructure is secure and compliant.
Clarify Responsibility Divisions
Engage with your cloud provider to better understand their shared responsibility model. To avoid gaps, define security roles for both providers and organizations. Create internal responsibility for cloud security testing and ways to ensure compliance with security policies and duties.
Assess Risks & Security Measures
Evaluate the risks associated with each asset and vulnerability, prioritizing them according to their impact. Examine existing security mechanisms to determine their efficacy. Create a risk-scoring system and threat models to help guide your evaluation, focusing on cloud-specific hazards and tailored testing efforts.
Select Testing Methods
Choose relevant security testing methods, such as:
- Vulnerability assessment: Uses automated tools to recognize known problems.
- Penetration testing: Involves simulating assaults to identify exploitable flaws.
- Source code analysis: Checks the code for security issues.
- Dynamic analysis: Identifies problems during actual use.
- Configuration analysis: Discovers configuration issues.
Perform Environment Testing
Conduct vulnerability assessments and penetration tests to identify potential threats and weaknesses. Use several approaches:
- Black box: Tests without any prior information about the surroundings.
- Gray box: Uses limited knowledge to simulate insider threats.
- White box: Evaluate with full information to identify specific vulnerabilities.
Record & Report Findings
Document all vulnerabilities, misconfigurations, and potential exploits encountered during testing. Provide concrete remedial recommendations and executive summaries to ensure stakeholders understand the results, risks, and business effects.
Develop Remediation Strategies
Create a priority-based plan to address identified vulnerabilities. Include suggestions for enhancing access controls, conducting additional testing, and revising security plans. Collaborate with development teams to make fixes and ensure their effectiveness through retesting.
Conduct Review & Improvement Plans
Perform a post-testing evaluation to identify the lessons learned and opportunities for improvement. Update your cloud security plan to include new technologies, risks, and best practices. Use the information gathered to improve future assessments and overall security posture.
Implement Ongoing Evaluation
Treat cloud security assessments as a continuous procedure. Keep up with evolving threats by reviewing and updating your assessment processes periodically. Employ continuous monitoring, such as intrusion detection systems and threat intelligence, to ensure the cloud environment’s security and resilience.
Cloud Security Assessment Best Practices & Recommendations
The recommended practices for cloud security assessments include examining documentation, conducting interviews, and completing both automated and manual tests. Create specific recommendations based on the findings, collaborate on your findings, and use cloud security services. Likewise, automate and integrate security testing processes to improve efficiency and effectiveness in implementing strong cloud security measures.

Review Existing Documentation & Conduct Stakeholder Interviews
Begin by analyzing current documentation and conducting interviews with key stakeholders to better understand the client’s business objectives, cloud architecture, and anticipated changes. This guarantees that the assessment is tailored to their individual requirements and future revisions.
Perform Automated & Manual Testing
Use automated tools to search for misconfigurations and irregularities in the cloud environment. Combine this with manual testing to look for potential attack vectors. Combining these methodologies enables a thorough review, revealing both technical defects and security vulnerabilities that automated tools may overlook, resulting in a more comprehensive evaluation of the cloud’s security posture.
Develop Tailored Recommendations
Analyze vulnerabilities and issues discovered during testing to create tailored suggestions. Present them to other security teams. Ensure that they address specific risks and are consistent with the client’s demands and security goals.
Collaborate on Findings & Recommendations
Review the findings and recommendations with internal stakeholders, providing full explanations and answering any concerns. This collaborative approach ensures a comprehensive grasp of the issues and recommendations, facilitating the effective implementation of the offered actions and solutions. Engage in open communication to establish alignment and resolve any concerns or misconceptions.
Utilize Cloud Security Services
Use specialized cloud security services to improve your security. Perform incident response to analyze breaches and implement response strategies. Execute compromise assessments to identify any current or previous breaches. Simulate red team/blue team exercises to test and develop defenses with controlled, focused attacks. This assures overall security and preparedness for prospective threats.
Automate & Integrate Security Testing
Automate vulnerability scanning, code analysis, and security inspections to ensure uniform coverage and timely response. Integrate these technologies into CI/CD pipelines to detect vulnerabilities early on. This process allows for immediate correction and ensures strong security throughout the development lifecycle.
For a stronger cloud protection approach, integrate this security assessment-specific best practices with the overall cloud security best practices.
Frequently Asked Questions (FAQs)
What Is a Cloud Security Checklist?
A cloud security checklist can help you review and prepare for cloud security assessments. Multiple teams collaborate to develop or audit security rules, secure data, verify compliance, and preserve customer trust. This tool gives a road map for secure cloud access and assesses the efficiency of current security measures.
What Are the 4 Types of Cloud Security Controls?
There are four main types of cloud security controls. Deterrent controls seek to deter attackers by indicating the consequences of destructive behavior. Preventive controls increase defenses by implementing measures such as MFA and secure coding techniques. Detective controls use techniques such as intrusion detection systems to discover and respond to threats. Corrective controls limit harm by restarting systems and isolating infected servers.
What Is Included in a Cloud Security Assessment?
A cloud security assessment may include evaluating data encryption for transit and rest, implementing strong access controls, using multi-factor authentication, and configuring logging and monitoring. It also includes applying security patches, developing an incident response plan, ensuring compliance, establishing data backup and recovery strategies, assessing vendor security, and providing employee security training.
Bottom Line: Assess Your Cloud Security Posture Now
A cloud security assessment is fundamental for overall cloud security but must be maintained, monitored, and updated regularly. Use the available technologies to expedite assessments and incorporate them into your overall cloud security strategy. This method improves the protection of your cloud environments by ensuring that security measures adapt to emerging threats and changes in your cloud architecture.
After cloud security assessment comes cloud security management. Manage and maintain your cloud infrastructure by exploring our guide covering the cloud security management types, strategies, risks, and best practices.




