Kaspersky is one of the most popular endpoint security solutions. Despite its good track record in malware defense, it’s set to be banned in the United States on September 29, 2024. With operations halted and upgrades discontinued, consumers must consider alternative options to continue protecting their network and cloud-based devices from cyber attacks. To help you look for replacements, I’ve compiled some of the best Kaspersky alternatives available.
Here are the six best alternatives to Kaspersky:
- CrowdStrike Falcon: Best overall for security, optimization, and support
- Microsoft Defender: Best platform for ease of use and administration
- ESET PROTECT: Best choice for additional endpoint protection features
- Bitdefender GravityZone: Best for core features, cost, and transparency
- SentinelOne Singularity: Best option for a unified management console
- Sophos Intercept X: Best for multi-stage threat detection and defense
Top Kaspersky Alternatives Comparison
The table below outlines major endpoint security solution capabilities such as behavioral analytics and threat detection. This also contains MITRE protection and detection scores, operating system support, free trial period, and the lowest business plan pricing.
| Behavioral Analytics | ML/AI Threat Detection | MITRE score (2023) | OS Support | Free Trial | Lowest Business Plan Cost | |
|---|---|---|---|---|---|---|
| CrowdStrike Falcon | ✔️ | ✔️ | Detection: 100% Protection: 13/13 | Windows, macOS, Linux, Chrome, iOS, Android | 15 days | $8.25 per month per device |
| Microsoft Defender | ✔️ | ✔️ | Detection: 100% Protection: 13/13 | Windows, macOS, Linux, Android, iOS | 30 days | Contact sales |
| ESET PROTECT | ✔️ | ✔️ | Detection: 77.62% Protection: 10/13 | Windows, macOS, Linux, Chrome, iOS, Android | 30 days | $4.50+ per month per device |
| Bitdefender GravityZone | ✔️ | ✔️ | Detection: 91.61% Protection: 12/13 | Windows, macOS, Linux, Chrome, iOS, Android | 30 days | $1.75 per month per device |
| SentinelOne Singularity | ✔️ | ✔️ | Detection: 88.11% Protection: 13/13 | Windows, macOS, Linux | 30 days | $5+ per month per device |
| Sophos Intercept X | ✔️ | ✔️ | Detection: 98.6% Protection: 11/13 | Windows, macOS, Linux, Chrome, iOS, Android | 30 days | Contact sales |
Note: Pricing is based on an annual subscription of endpoint security solutions unless otherwise noted.
After reviewing some of the top Kaspersky alternatives, I identified CrowdStrike Falcon as the strongest option due to its extensive security features. Bitdefender GravityZone and ESET Endpoint also stand out for their broad core features and system optimization capabilities. Continue reading to see how I assessed and analyzed these options, or skip ahead to how I evaluated the solutions.

CrowdStrike Falcon – Best Overall for Security, Optimization & Support
Overall Reviewer Score
4.5/5
Core features
4.6/5
Advanced features
4.5/5
System optimization and security
4.8/5
Ease of use and administration
4.2/5
Pricing and transparency
4/5
Customer support
4.8/5
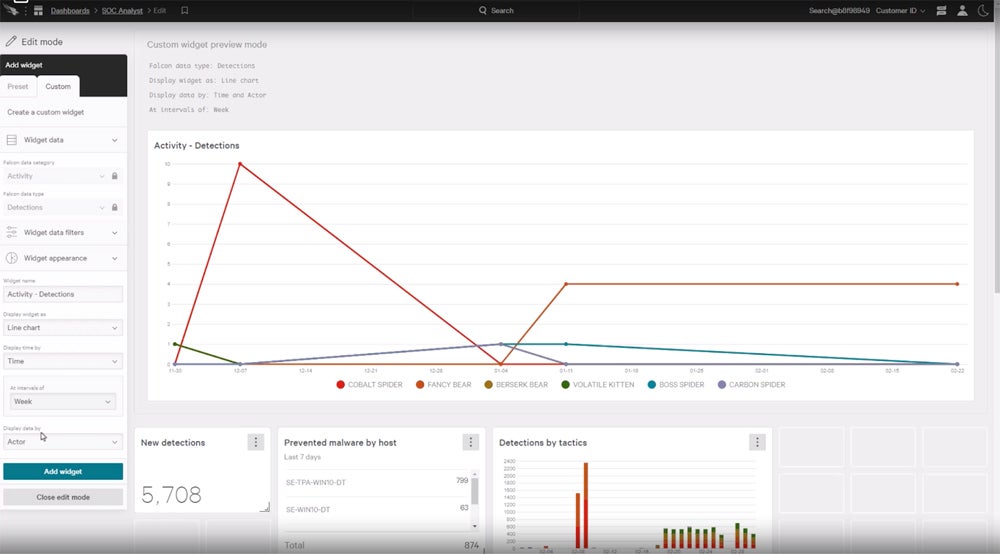
CrowdStrike Falcon is a cloud-based endpoint protection solution specializing in security, system optimization, and customer support. It provides 24-hour protection against all forms of attacks using a single lightweight agent. The platform has a uniform console and an open, extendable environment for simple integration. It also offers global customer service via phone, email, tech alert subscription, and a dedicated technical help webpage.
Pros
Cons
- Falcon Go for Small Business: $59.99 per device per year
- Falcon Pro for Small Business: $99.99 per device per year
- Falcon Enterprise: $184.99 per device per year
- Contact for quotes: Falcon Elite and Falcon Complete MDR available
- Free trial: 15 days
- Free demo: Available
- Next-generation antivirus: Protects your organization 24/7 by anticipating and responding to emerging threats, including known and undiscovered malware, even when offline.
- USB device control: Easily monitors and manages all USB devices, guaranteeing the safe and responsible use of any device connected to your endpoints, including USBs, cameras, and printers.
- Detection and response: Prevents breaches with AI-powered protection, detection, and response, supported by world-class adversary intelligence to handle all forms of threats, including malware.
- Identity protection: Quickly detects unusual user activity and lateral actions by potential threat actors. Provides real-time visibility for rapid identification and response to potential breaches.
- Add-on features: Offers Falcon Data Protection for unified security, Falcon Next-Gen SIEM for a comprehensive SOC platform, and Falcon for Mobile to safeguard iOS and Android devices.
CrowdStrike’s cloud-based solution includes a comprehensive set of fundamental endpoint security features. However, Bitdefender GravityZone outperforms it in terms of feature set and flexibility, with cloud and on-premises deployment options available.

Microsoft Defender for Endpoint – Best for Ease of Use & Administration
Overall Reviewer Score
4.4/5
Core features
4.6/5
Advanced features
4.7/5
System optimization and security
4.6/5
Ease of use and administration
4.9/5
Pricing and transparency
3.2/5
Customer support
3.3/5
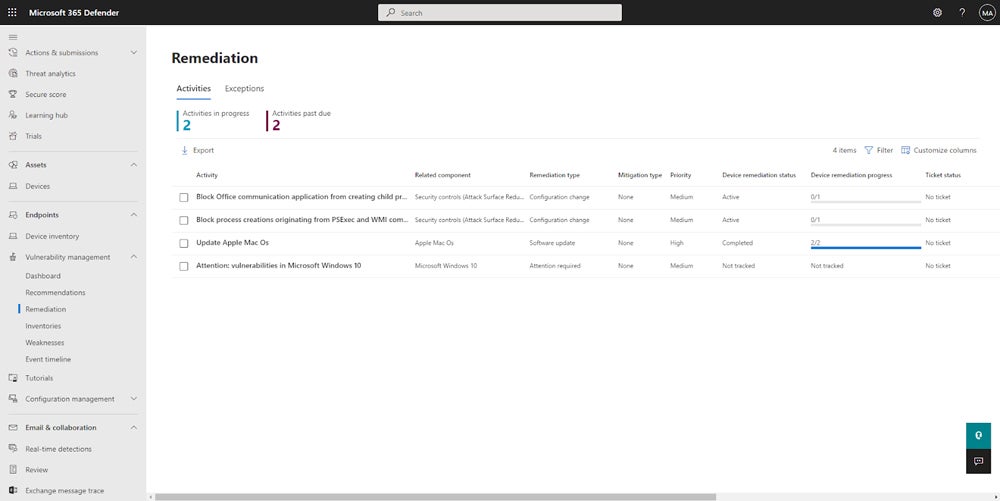
Microsoft Defender for Endpoint is a cloud-native platform simplifying security administration through intuitive controls and actionable analytics. It streamlines onboarding with out-of-the-box policies and provides AI-powered security across various devices, including Windows, macOS, Linux, Android, iOS, and IoT. Its Unified Security Operations platform integrates XDR and SIEM to provide full coverage.
Pros
Cons
- Contact for quote: Custom pricing available
- Free trial: 30 days
- Free demo: Available
- Ransomware protection: Prevents ransomware attacks by limiting lateral movement and remote encryption on all devices, disrupting threats in a decentralized manner.
- Copilot: Utilizes the built-in generative AI to quickly investigate and respond to events, prioritize alerts, and improve skills.
- Auto-deployed deception: Generates and scales deception tactics, providing cyberattackers with early-stage, high-fidelity signals to identify threats.
- Flexible business controls: Uses granular controls such as settings, rules, access, threat detection, and automated workflows to balance security and productivity.
- Simplified endpoint management: Enables security and IT teams to collaborate easily and avoid miscommunication, misconfigurations, and security breaches.
Microsoft scores high in security evaluations, demonstrating good competitive performance. However, if you want a solution with higher independent security testing ratings, CrowdStrike Falcon is a good option.

ESET PROTECT– Best for Additional Endpoint Protection Features
Overall Reviewer Score
4.3/5
Core features
4.7/5
Advanced features
4.8/5
System optimization and security
3.3/5
Ease of use and administration
4.8/5
Pricing and transparency
4.2/5
Customer support
3.6/5
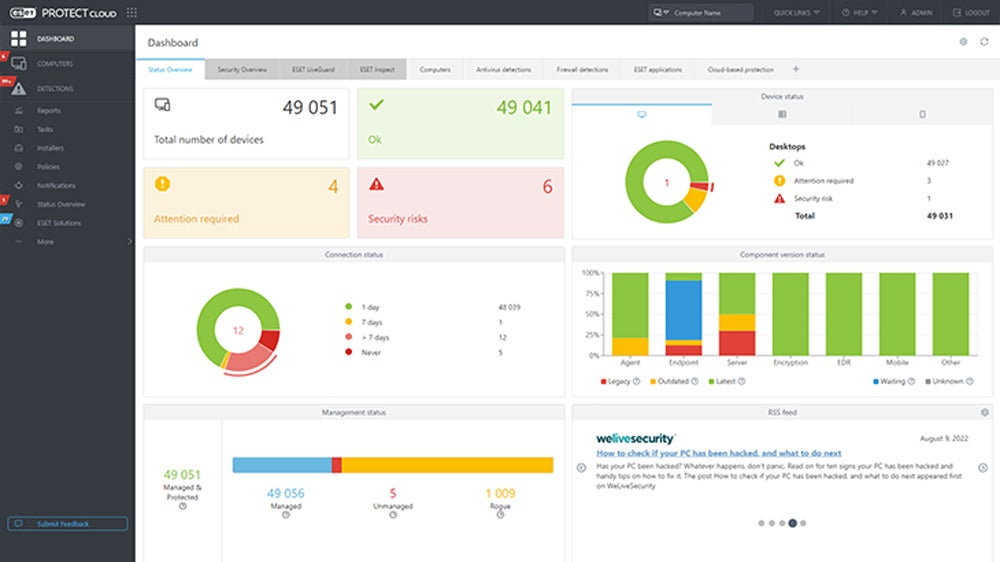
ESET PROTECT is a comprehensive endpoint security solution with a cloud-delivered XDR platform for breach prevention, increased visibility, and effective remediation. ESET PROTECT Complete protects Microsoft 365 email and OneDrive from spam, phishing, and malware. It also provides mobile threat detection, cloud app protection, multi-factor authentication, and endpoint encryption.
Pros
Cons
- ESET PROTECT Advanced: $275+ per year for 5 devices
- Contact for quote: Enterprise, Elite, and MDR Ultimate available
- Free trial: 30 days
- Free demo: Available
- Single-click management: Allows quicker management by executing operations such as defining exclusions, submitting files for analysis, and initial scans.
- Advanced reports: Includes over 170 built-in reports and allows you to create custom reports from over 1,000 data points for deeper insights.
- Custom notifications: Uses predefined or custom notifications with a comprehensive editor to create personalized alerts.
- Easy deployment: Installs pre-configured live installers that automatically connect endpoints to the relevant instance and valid subscription for a simple setup.
- Modern endpoint protection tools: Offers next-generation antivirus, network attack protection, device control, and anti-phishing capabilities for complete endpoint security.
ESET PROTECT is straightforward, with pricing and included features visible on their website. However, Bitdefender GravityZone if you need more transparent pricing details and potentially more affordable rates.

Bitdefender GravityZone – Best for Core Features, Cost & Transparency
Overall Reviewer Score
4.2/5
Core features
4.8/5
Advanced features
4.7/5
System optimization and security
3.4/5
Ease of use and administration
4.1/5
Pricing and transparency
4.5/5
Customer support
3.5/5
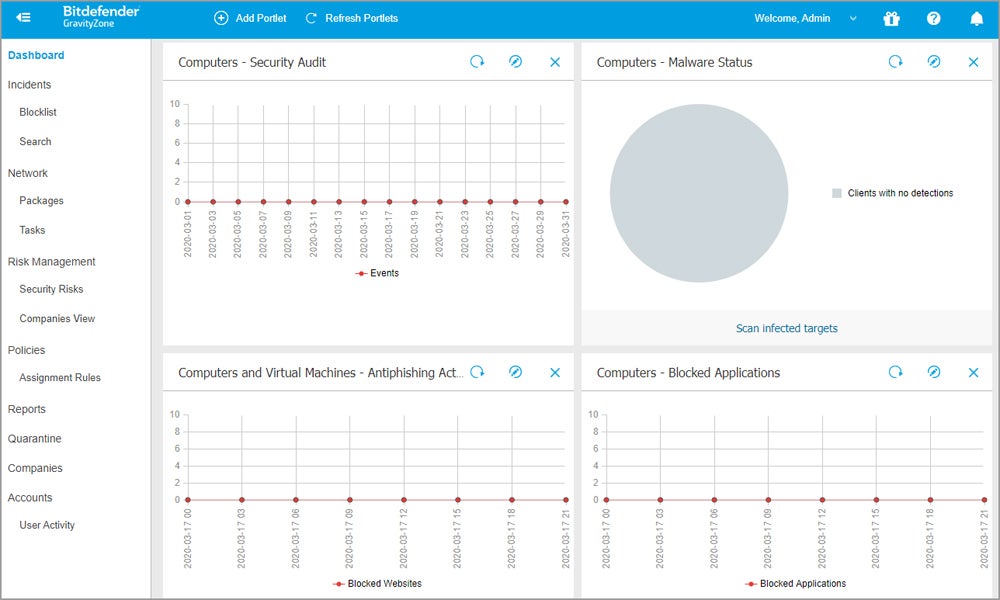
Bitdefender GravityZone is a unified platform that protects the entire enterprise through a single integrated management console. It provides comprehensive protection by monitoring web traffic and blocking harmful websites, files, scripts, and phishing attacks. GravityZone detects threats using advanced machine learning, behavioral analysis, and continuous monitoring and takes quick action, such as process termination, quarantine, and reversal of malicious changes.
Pros
Cons
- Small Business Security: $104.99 per year for 5 devices
- Business Security: $129.49 per year for 5 devices
- Business Security Premium: $286.99 per year for 5 devices
- Free trial: 30 days
- Free demo: Available
- Ransomware prevention and mitigation: Uses detection and remediation technologies to protect data against ransomware. It detects unusual encryption attempts, prevents them, and restores backup files.
- Network attack defense: Employs multiple security layers to monitor incoming, outgoing, and lateral traffic to defend against network-based attacks such as brute force, port scans, and password stealers.
- Web/content control and filtering: Scans web traffic to prevent harmful websites, files, and phishing attacks. It also limits access to specific apps and web categories according to predefined restrictions.
- Risk management: Identifies and prioritizes risky human behavior and software configuration issues. It takes a risk-based strategy to reduce exposure and harden the endpoint surface area.
- Central management: Manages all security components from a single integrated console, making it simple to track, manage, and automate cybersecurity events without extra servers or IT professionals.
Bitdefender offers strong endpoint protection features, however, some customers have reported that it can be resource-intensive. If you prefer a solution with lower system impact, try ESET PROTECT, which provides robust security with minimal demand on system resources.

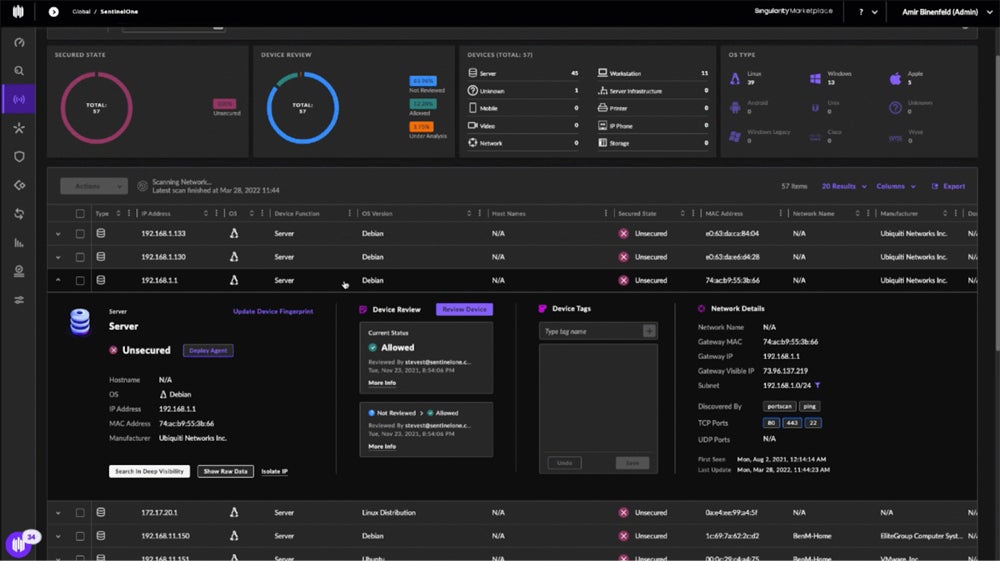
SentinelOne Singularity – Best for Unified Management Console
Overall Reviewer Score
4.2/5
Core features
4.5/5
Advanced features
4.4/5
System optimization and security
4.1/5
Ease of use and administration
4/5
Pricing and transparency
2.9/5
Customer support
4.7/5
SentinelOne Singularity is an enterprise cybersecurity platform integrating prevention, detection, and response across your security landscape. It combines EPP and EDR in a single agent, simplifying management through centralized policy administration. The platform employs static and behavioral AI for rapid threat response, offering visibility, analytics, and automation to safeguard against both known and new cyber threats.
Pros
Cons
- Singularity Core: $69.99 per endpoint per year
- Singularity Control: $79.99 per endpoint per year
- Singularity Complete: $159.99 per endpoint per year
- Singularity Commercial: $209.99 per endpoint per year
- Contact for quote: Singularity Enterprise available
- Free trial: 30 days
- Free demo: Available
- Storyline: Automates continuous OS and Kubernetes workloads monitoring for faster hypothesis testing and root cause analysis.
- One-click remediation and rollback: Facilitates threat mitigation and prevention across multiple devices using a single code base, removing the need for manual scripting.
- Hunter’s Toolkit: Stores previous EDR data for up to three years, allowing for effective threat hunting utilizing MITRE ATT&CK® methods and customized network isolation.
- Vigilance 24/7 service: Provides 24/7 managed detection and response (MDR) by elite analysts. They handle daily operations and escalate threats only when necessary.
- Automated threat resolution: Automatically reverses unauthorized modifications, simplifying threat response and eliminating the need for onerous human scripting.
SentinelOne Singularity provides easier management with its unified platform. However, some users have reported that it’s resource-heavy. If you prefer a solution with a lower impact on system performance, try ESET.

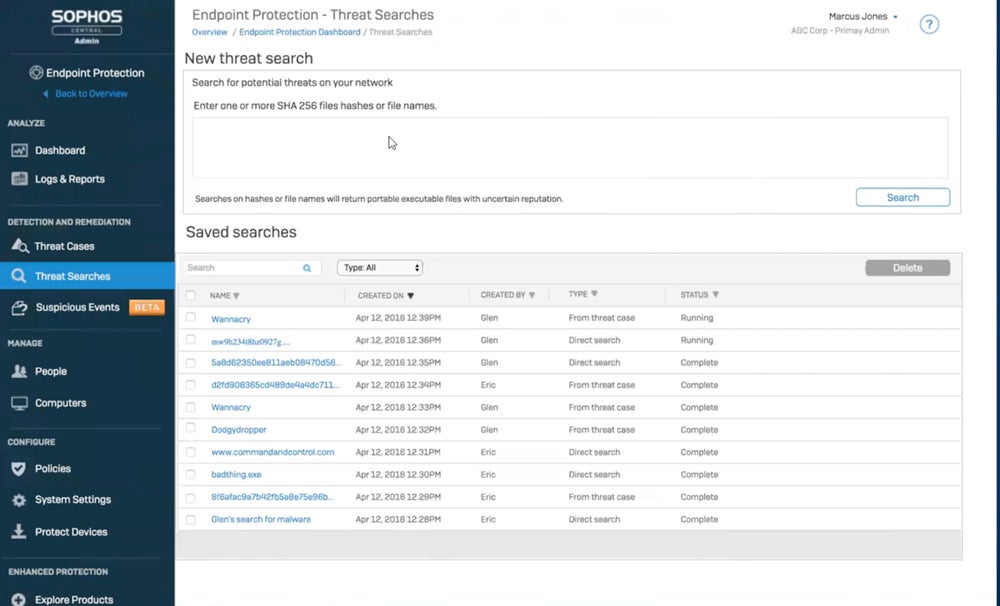
Sophos Intercept X – Best for Multi-Stage Threat Detection & Defense
Overall Reviewer Score
4/5
Core features
4.4/5
Advanced features
4.5/5
System optimization and security
3.9/5
Ease of use and administration
4.2//5
Pricing and transparency
2.4/5
Customer support
4.1/5
Sophos Intercept X provides strong endpoint security through cloud-based and on-premise solutions. It uses powerful anti-ransomware, exploit prevention, and deep learning analysis to detect and block attacks before they occur. Sophos Endpoint offers comprehensive protection, including AI-driven protection and real-time encryption rollback. Sophos Intercept X employs prevention-first approaches to reduce security incidents and increase response efficiency.
Pros
Cons
- Contact for quote: Endpoint Advanced, Advanced with XDR, and Advanced with MDR Complete available
- Free trial: 30 days
- Free demo: Available
- Adaptive attack protection: Improves defenses against active attacks by decreasing the attack surface and limiting threats.
- Critical attack warning: Alerts administrators with detailed notifications on hostile activity across endpoints, allowing for a timely response.
- Sophos Central: Provides a cloud platform for managing Sophos products that includes default strong settings and optional granular controls.
- Account health check: Detects and resolves security misconfigurations with a single click to maintain a secure posture.
- Device encryption: Encrypts the entire disk for Windows and macOS, with safe key management and user self-recovery.
Sophos lacks accurate pricing information, making it difficult to estimate costs beforehand. For more transparent and clear pricing arrangements, consider Bitdefender GravityZone or SentinelOne Singularity.
5 Key Features of Kaspersky Alternatives
A reliable endpoint security solution should at least include key features such as behavioral analytics, endpoint visibility, attack isolation, quarantined file recovery, and machine-learning threat detection. If you’re looking for an alternative to Kaspersky, make sure the solution has these capabilities for strong protection and effective threat management.
Behavioral Analytics
Behavioral analytics is the process of monitoring and analyzing endpoint actions using machine learning and artificial intelligence to find deviations from usual trends. This aids in detecting potential insider threats by identifying strange actions, hence increasing overall security by addressing threats before they escalate.
Endpoint Visibility
Endpoint visibility is the capacity to view, monitor, and manage all devices in an IT system through management software. It entails identifying, tracking, and controlling devices such as laptops, desktops, cellphones, and IoT devices, ensuring complete control over connected devices, data, and application access.
Attack Isolation
The attack isolation feature entails rapidly detecting malicious actions, isolating impacted areas, and preventing the threat from spreading to other portions of the network or associated systems. This separates several software instances so that each instance only sees and affects itself. By segregating questionable files, this avoids sophisticated breaches that hide ransomware and other malware within them.
Quarantined Files Recovery
This feature enables you to remove, restore, or download files from quarantine on the same computer. It allows secure file handling and seamless recovery following Portable Security detection, resulting in a regulated threat management procedure.
Machine Learning Threat Detection
Threat detection powered by ML and AI uses algorithms to examine data and rapidly discover new, complex threats. Learning from previous instances improves accuracy and speed in spotting threats. Both supervised and unsupervised methods, such as anomaly detection, aid in detecting unexpected patterns and play an important role in fraud detection and system monitoring.
How I Evaluated Alternatives to Kaspersky
To evaluate the best endpoint security alternatives to Kaspersky, I created a product score rubric that included six vital criteria. Each criterion was weighted based on importance and then assessed based on my list of subcriteria, including the availability of a feature or service. I determined the top solutions and the ultimate winner based on their overall ratings. Finally, I identified their top use cases based on the criterion at which they excelled.
Evaluation Criteria
I prioritized evaluating core features for essential capabilities, followed by advanced features for further functionality. Next, I evaluated system optimization and security, usability, and administration. Finally, I looked into pricing transparency and customer support to ensure total value and service quality.
- Core features (25%): This category analyzed behavioral analytics, endpoint visibility, automated incident response, attack isolation, quarantined file recovery, zero-day protection, machine learning, sandboxing, automatic blocking, web protection, and cross-platform support.
- Criterion winner: Bitdefender GravityZone
- Advanced features (20%): I assessed additional capabilities such as scalability for various user sizes, cloud or on-premises management, zero-trust network access (ZTNA), threat removal tools, ransomware protection, unified endpoint services, automatic backups, and more.
- Criterion winner: ESET PROTECT
- System optimization and security (20%): I evaluated each tool while considering auto-system optimization, MITRE detection and protection scores, MITRE missing steps, AV-Test Malware Protection, and AV-Test Performance ratings. This evaluates how network tools effectively maximize system performance while preserving robust security.
- Criterion winner: CrowdStrike Falcon
- Ease of use and administration (15%): I reviewed integration, deployment, and ease of use ratings from different platforms like Gartner and Capterra. I also considered a single management console, automatic onboarding, updated documentation, and background operation features.
- Criterion winner: Microsoft Defender for Endpoint
- Pricing and transparency (10%): To assess overall cost-effectiveness and clarity, I looked at free trials, the lowest endpoint and AV plan fees, free versions/add-ons, transparent pricing details, and discount offerings.
- Criterion winner: Bitdefender GravityZone
- Customer support (10%): To analyze the quality and accessibility of customer service, I looked at live chat, phone, and email assistance, live demos/training, and Gartner and Capterra user reviews.
- Criterion winner: CrowdStrike Falcon
Frequently Asked Questions (FAQs)
Why Did U.S. Ban Kaspersky?
On September 29, 2024, the United States expanded its Kaspersky ban also to cover renewals, resales, and updates. The action, which was motivated by national security concerns, seeks to prevent possible Russian spying via Kaspersky’s antivirus software, which officials say might assist hacking or illicit data collection on Americans.
What If I Have Already Subscribed to Kaspersky Products?
If you already use Kaspersky products in the United States, you’ll unlikely face legal consequences simply for having them. However, consider switching to an alternative. Kaspersky products purchased within the last 30 days may also be returned for a refund. Kaspersky has turned off auto-renewal, so your product will work until your subscription expires.
What Is the Best Security to Put on Your Device?
Endpoint protection software, antivirus programs, and password management solutions are all vital tools for optimal device security. You may also consider using firewalls and advanced endpoint detection and response (EDR) and prevention (EPP) systems to ensure comprehensive protection against various threats.
Bottom Line: Find the Best Kaspersky Alternative
While Kaspersky provides great endpoint security, current prohibitions require you to look for alternative solutions. Fortunately, there are plenty of solid solutions available. Focus on aspects that are critical to your business and discuss your requirements with vendors. Enterprise demands vary, so before committing, thoroughly analyze features using free trials to guarantee the greatest fit for your company’s needs.
If you’re looking for more options for endpoint security tools, explore our comprehensive guide of the top endpoint detection and response (EDR) solutions, covering their key features, pros, cons, pricing, and more.
Paul Shread contributed to this article.