Cloud security best practices help enterprises protect their cloud infrastructure by adhering to industry standards and utilizing cloud security solutions. Although these measures might not prevent every attack, these practices shore up your business defenses to protect your data. You can improve your cloud security posture by following the top tips and understanding the biggest cloud security issues, plus how to overcome them.
Here’s a free checklist to serve as your guide to the recommended cloud security best practices. Click the image to download the file, then customize your own list depending on your business needs.

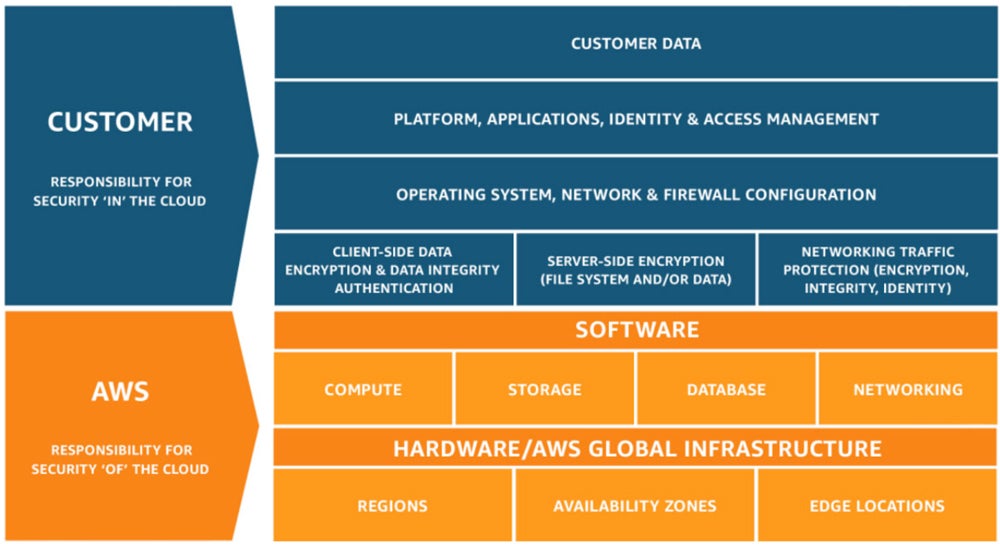
Understand Your Shared Responsibility Model
The shared responsibility model establishes security responsibilities to the cloud provider and the customer. The provider protects the cloud infrastructure, whereas the consumer protects data, applications, and configurations. In this framework, enterprises can efficiently manage cloud security and reduce risks by clearly defining responsibilities and adhering to detailed security policies.
Leading IaaS and PaaS providers provide documentation to define roles in various deployment situations. When evaluating cloud vendors, check the common security rules to minimize miscommunication and misconceptions, which may lead to lax security controls and events going unnoticed. As long as you do your part through implementing encryption and configuring connections and settings properly, your data will generally be secure.
Ask Your Cloud Provider Detailed Security Questions
Ask your public cloud vendors detailed questions about the security measures and processes they have in place to identify any holes or weaknesses in the vendor’s security processes. This practice assures regulatory compliance and checks that the vendor’s measures are in line with your organization’s unique security requirements.
It’s easy to assume that the leading vendors handle security properly, often through employing zero trust security, yet techniques and practices might differ greatly. To understand how a particular cloud provider compares, you should ask a wide range of questions, including:
- Location: Where do the provider’s servers reside geographically?
- Security protocol: What is the provider’s protocol for suspected security incidents?
- Restoration measures: What is the provider’s disaster recovery plan?
- Protection: What measures does the provider have to protect access components?
- Client support: What level of technical support is the provider willing to provide?
- Pentests: What are the results of the provider’s most recent penetration tests?
- Encryption: Does the provider encrypt data while in transit and at rest?
- Provider access: Which roles from the provider have access to my cloud data?
- Authentication: What authentication methods and tools does the provider support?
- Compliance: What compliance requirements does the provider support or adhere to?
What If Your Cloud Provider Doesn’t Have Effective Security?
If your cloud provider fails to provide enough security, your company risks data breaches, downtime, and compliance issues. Inadequate security can result in illegal access, data theft, and data loss. Poor disaster recovery and incident response lead to extended downtime and increased harm. Limited support impedes risk management, and failure to adhere to compliance standards can lead to regulatory penalties and legal concerns.
To address these concerns, consider taking the following actions:
- Hire third-party specialists: Evaluate the infrastructure and operations with external security professionals.
- Examine SLAs and contracts: Clearly define security, data protection, and incident response responsibilities.
- Improve your security: Use encryption, access limits, and monitoring to compensate for provider shortcomings.
- Backup vital data: Leverage an alternative cloud provider or on-premises infrastructure to avoid data loss and ensure business continuity.
- Consider other providers: If your present provider can’t meet your security and compliance requirements, look into alternatives.
Just getting started with cloud security for your business? Check out the top cloud security companies which details the cloud vendors’ top solutions, key features, and more.
Train Your Staff
Staff training entails educating employees about cybersecurity standards. Well-trained staff can assist businesses in safeguarding sensitive data and maintaining cloud service security against unauthorized access by hackers by successfully recognizing and responding to threats. Apply the following methods to manage your employee training programs:
- Emphasize the risks of shadow IT: Educate employees on the consequences of using unauthorized tools that could reveal potential flaws that could compromise security safeguards and threaten data integrity.
- Provide thorough cybersecurity awareness training: Cover topics such as spotting potential threats, setting strong passwords, recognizing social engineering attacks, and understanding risk management.
- Provide specialized training for security personnel: Ensure that your security personnel are up to date on emerging risks and effective mitigation measures in order to maintain strong security protocols.
- Encourage accountability through regular discussions: Establish security standards, address data privacy and password management, and promote open dialogue about the value of security regulations.
These methods can improve your security posture while lowering the risk of data breaches and cyber events. They also protect the company’s brand and maintain compliance with industry standards.
Establish & Enforce Cloud Security Policies
A cloud security policy is a set of written guidelines that specify who can use cloud services, how to use them, and what data can be stored in the cloud. It also outlines the security software and tools staff must use to safeguard data and applications. These rules guarantee consistent security measures throughout the company, reduce the risks associated with cloud adoption, and protect sensitive data from unwanted access or breaches.
To assist you in establishing effective cloud security policies, here’s a snippet of our template outlining the key sections of a cloud security policy. Access the full document, download a copy, and customize it by clicking the image below:

Make sure to tailor the sections of your policies based on your organization’s specific business rules and procedures.
Secure Your Endpoints
Endpoints, such as laptops, desktops, mobile devices, and tablets, serve as the gateway for users to engage with cloud-based apps and data. They have direct connections to the cloud, so it’s highly important to secure them to avoid unauthorized access, data breaches, and other cybersecurity concerns. Examine and improve your endpoint security procedures on a regular basis to successfully minimize risks and protect their cloud-based data.
To do this, implement a comprehensive defense-in-depth plan that covers firewalls, anti-malware, intrusion detection, and access control. Given the complexities of endpoint security, automated security tools such as endpoint detection and response (EDR) and endpoint protection platforms (EPP) may help boost your security. Additional controls to consider include patch management, endpoint encryption, VPNs, insider threat prevention, and more.
If you’re looking for additional measures to boost your security, explore the best patch management tools and solutions and see their differences, key features, and more.
Encrypt Data in Motion & at Rest
Encrypting data at rest entails safeguarding data kept on physical or digital storage devices, such as hard drives or servers, and rendering it unreadable to anyone who doesn’t have the right decryption key. You can utilize encryption features supplied by your cloud service provider or use third-party encryption solutions to encrypt data before it’s stored in the cloud.
Encrypting data in motion means protecting data as it travels over a network, such as when transmitting data between devices or accessing cloud services. Verify that data in transit is encrypted through the use of secure communication protocols such as secure sockets layer (SSL) or transport layer security (TLS). These protocols encrypt data during transmission to prevent interception by unauthorized parties.
Discover the best encryption software and tools’ advantages and key features that can provide you with enhanced data security.
Integrate Additional Cloud Security Tools
This best practice involves expanding cloud security procedures with additional technologies such as identity and access management (IAM), intrusion detection and prevention systems (IDPS), and cloud access security broker (CASB). Using these tools improves security layers, resulting in a stronger defense against potential attacks and weaknesses in cloud environments.
Identity & Access Management Solution
Having an IAM solution reduces the risk of unauthorized access in public cloud security. IAM systems create and maintain user identities and permissions, ensuring that only authorized users can access resources. Adopt comprehensive IAM techniques to improve security, protect sensitive data, and ensure regulatory compliance in cloud settings. Consider the IAM solutions below:
- JumpCloud: Rated as our best overall IAM solution, JumpCloud offers a full set of features for identity, access, and device management. The platform is free for the first 10 users and 10 devices. The full JumpCloud platform costs $15 per user per month.
- Okta Workforce Identity: Okta’s IAM solution is most suitable for large enterprises that manage security for their third-party vendors. Workforce IAM Options costs $1,500+ per annual contract. They also offer custom pricing per desired features.
- OneLogin: This solution is best for developers integrating IAM into their applications. OneLogin’s Professional plan, with MFA, identity lifecycle management, advanced directory and SSO features, costs $8+ per user per month. They offer a 30-day free trial.
Explore other best identity and access management solutions in our extensive review, covering their key features, pricing, and more.
Intrusion Detection & Prevention Systems
Intrusion detection and prevention systems (IDPS) are security tools that monitor, analyze, and respond to network traffic, improving network security independently or in conjunction with other tools. Major cloud providers provide their own IDPS and firewall services, which are augmented by cybersecurity options from their own marketplaces. Here are some of the top IDPS that you may check out:
- Atomic OSSEC: We recommend OSSEC for medium and large businesses, but for smaller teams, they also offer a free, open-source IDS. Atomic OSSEC has a 14-day free trial, and the solution costs $55 per endpoint or system in a year-long license.
- Trellix IPS: This security platform provides a wide range of functionalities designed for enterprise-level security. It offers extended security features like DDoS prevention, bot detection, and host quarantining. You may contact their sales team for a custom pricing.
- Check Point Quantum: Check Point’s IPS product works best for NGFW environments. Quantum also provides reporting features, vulnerability detection, policy configuration, and more. You may contact their sales team for custom pricing and free trial.
Assess the best intrusion detection and prevention systems including their unique functionalities to guarantee strong cloud security security measures for your business.
Cloud Access Security Broker & Cloud Security Solutions
CASB are purpose-built solutions for implementing cloud security standards ideal for firms that use several cloud services from many providers and can track unlawful app activity. Also consider utilizing other cloud tools like cloud-native application (CNAPP), workload protection platforms (CWPP) and cloud security posture management (CSPM) to protect cloud infrastructures and data. Check out some of our recommended cloud security solutions:
- Proofpoint’s CASB: This solution is best for businesses seeking a user- and DLP-focused solution. Key features include shadow IT activity detection and third-party SaaS apps management. Contact sales for a free live demo and custom quotes.
- Orca Security’s CWPP: Orca’s CWPP service is ideal if you’re looking for advanced cloud configuration capabilities. Additional features include vulnerability management and compliance monitoring. You may contact their sales for a custom quote.
- Crowdstrike’s CNAPP: Falcon Cloud Security includes CWP, CSPM, CIEM and container security in a single CNAPP offering. Their solution delivers advanced threat protection in cloud environments. Annual pricing costs $300+ per Falcon Go bundle.
- Palo Alto’s CSPM: Prisma Cloud is our top choice for a CSPM solution, offering a full feature set and functionalities for hybrid, multi-cloud, and cloud-native environments. Contact sales for custom pricing or request a free trial for 30 days.
Learn what other cloud security tools such as CSPM, CWPP, CIEM, and CNAPP offer, including their benefits, features, pricing, and more.
Double-Check Your Compliance Requirements
Before establishing a new cloud computing service, review your particular compliance requirements and make sure that a service provider will meet your data security needs. Staying compliant is a top cloud security priority. Governing bodies will hold your business responsible for any regulatory breaches, even if the security problem originated with the cloud provider. Here are some guidelines on how to check your compliance:
- Review industry rules: Ensure compliance with legislation governing the acquisition and protection of personally identifiable information (PII) in specific industries.
- Consider geographical regulations: Address any unique compliance requirements for organizations that operate or store data in specific geographic areas.
- Assess data security standards: To protect consumer privacy and prevent data breaches, double-check the data security standards and best practices.
- Seek legal advice: Consult with legal experts or compliance professionals to ensure a thorough grasp and adherence to all applicable compliance rules.
Check out the best third-party risk management (TPRM) tools that can provide you with comprehensive assessments and monitoring of third-party vendors’ compliance.
Conduct Pentesting, Vulnerability Scans, & Audits
Auditing, penetration testing, and vulnerability testing entail assessing protection measures to uncover flaws and assure compliance with industry standards. These practices assist you in proactively detecting and addressing vulnerabilities, strengthening defenses against cyber threats, and ensuring the integrity and security of their systems and data. Consider these recommended practices:
- Conduct penetration tests: Evaluate the efficiency of existing cloud security solutions. identify weaknesses that could jeopardize the security of data and apps in the cloud.
- Run vulnerability scans: Use cloud vulnerability scanners to detect misconfigurations and other issues, hence improving the security posture of the cloud environment.
- Perform regular security audits: Evaluate all security providers and controls to assess their capabilities. Ensure they adhere to the agreed-upon security terms and standards.
- Review access log audits: Check that only authorized users have access to sensitive data and cloud apps, hence increasing access control and data security safeguards.
Enable & Monitor Security Logs
Enable logging in your cloud services, then take it a step further by ingesting that data into a security information and event management (SIEM) system for centralized monitoring and response. Logging helps system administrators and security teams monitor user activity and detect unapproved modifications and activity, a process that would be impossible to accomplish manually. This allows for preventative measures and adjustments to improve security.
To manage your security logs, employ these strategies:
- Enable logging with centralized monitoring: Import logging data into a SIEM system for centralized monitoring to detect and respond to security problems effectively.
- Improve security visibility: Monitor user behavior and detect illegal changes and activity, offering insights that are tough to obtain manually.
- Facilitate incident response: Use detailed logs to provide a clear record of attacker activity for a speedy remediation and limiting damage in the event of a security breach.
- Track changes and misconfigurations: Use good logging to track changes that may lead to vulnerabilities and detect excessive access permissions.
- Utilize cloud provider tools: Import CloudTrail log files into an AWS CloudTrail Lake or third-party SIEM product for analysis to properly employ cloud provider tools.
Explore how security data lakes address SIEM limitations by integrating seamlessly with various data sources, including logs, events, and threat intelligence feeds.
Understand & Mitigate Misconfigurations
Addressing misconfigurations entails taking proactive steps to prevent errors in storage buckets, APIs, connections, open ports, permissions, and encryption. Default extensive rights in cloud services, such as AWS S3 buckets, may pose major security vulnerabilities if not appropriately restricted. Misconfigurations enable hostile actors to exploit vulnerabilities. Reduce misconfigurations by taking the following actions:
- Personally configure buckets: Manually adjust each bucket or group of buckets to ensure adequate security settings and prevent unwanted access.
- Collaborate with development teams: Work closely with dev teams to ensure that web cloud address configurations are correct and meet security standards.
- Avoid default access rights: Never use default access rights since they can grant excessive privileges and pose security issues.
- Define user access levels: Determine the necessary user access levels (view-only or editing) and configure each bucket accordingly.
- Implement the least privilege principle: Allow users the permissions they only need to complete their tasks to reduce the risk of data breaches.
What Are the Biggest Cloud Security Issues?
Some of the most common cloud security issues include misconfigurations, unnecessary or unauthorized access, cloud vendor solutions weakness, and employee errors. To reduce these issues as your business migrates to the cloud, rethink your network-centric idea of security and re-architect for the decentralized cloud. Here’s how some of the biggest cloud security issues occur and the key methods to address them.
Cloud Misconfigurations
Misconfigurations in cloud settings are a common source of security vulnerabilities. These mistakes can provide unwanted access to critical data, services, or applications. Human errors or oversight during the setup and administration of cloud resources could lead to misconfigurations.
How to Overcome this Issue
To address cloud misconfiguration issues, do the following:
- Automate detection: Set up tools to automatically identify configuration drift and departures from expected states.
- Monitor modifications and collaboration: Use version control systems for infrastructure code to track changes and collaborate.
- Integrate automated code analysis: Use automated code analysis tools in your CI/CD pipeline to detect errors early in the development process.
- Monitor configuration changes: Set up alerts to detect any illegal changes and respond quickly to any suspicious activities.
- Use security scanning tools: Use security scanning tools created for infrastructure as code (IaC) to detect and correct misconfigurations.
Unnecessary & Unauthorized Access
Allowing users or apps excessive or unwarranted access rights might lead to vulnerabilities in your cloud environment. Data breaches, data loss, and other security events can all result from unauthorized access.
How to Overcome this Issue
Use these methods to manage unnecessary access:
- Implement just-in-time (JIT) access provisioning: Give users access just when they need it and for the shortest possible time.
- Enforce least privilege: Grant minimal permissions by default. Limit who can access your critical resources.
- Regularly review and revoke access: Conduct periodic audits to identify and delete any superfluous access credentials.
- Use automatic access recertification: Set up automated mechanisms to validate and recertify access privileges on a regular basis.
- Limit lateral movement by segmenting your network: Partition the network to restrict unauthorized access across various portions and prevent attacker lateral movement.
Cloud Vendor Weaknesses
Although cloud service providers provide strong security protections, they’re not immune to threats. Attackers often use cloud provider flaws to get access to consumer data or services. These flaws might include software defects, permission issues or infrastructural flaws.
How to Overcome this Issue
Apply these solutions to tackle cloud vendor weakness issues:
- Assess security capabilities: Evaluate and compare vendors’ security offerings and capabilities. Make sure it suits your business’ security requirements.
- Implement a multi-cloud or hybrid strategy: Avoid vendor lock-in by considering a multi-cloud or hybrid cloud approach.
- Create a backup strategy: Reduce the risk of vendor outages or interruptions by developing a backup plan.
- Monitor vendor security updates: Stay updated about vendor security updates and fixes so you can address the vulnerabilities quickly.
- Check your vendor contracts: Regularly review and update cloud vendor contracts and service level agreements (SLAs) and ensure that they match security expectations.
Employee Errors
Employee errors pose big threats to cloud security because they can unintentionally expose sensitive data or fall victim to phishing attacks. To reduce the chance of such accidents and improve overall security posture, employees must undergo comprehensive training and be made more aware of the potential dangers.
How to Overcome this Issue
Try these methods for dealing with employee error issues:
- Maintain extensive cybersecurity training: Provide extensive and collaborative training to help staff understand cybersecurity best practices and security response.
- Establish accountability and reporting: Create an accountable culture and encourage employees to swiftly report security occurrences or concerns.
- Implement secure password restrictions: Enforce password restrictions that balance usability with security.
- Use RBAC and least privilege principles: Restrict access to sensitive data and systems using role-based access control tools.
- Conduct phishing simulations: Educate personnel on how to identify and respond to phishing attempts.
Frequently Asked Questions (FAQs)
What Are the Key Elements of a Strong Cloud Security Strategy?
A strong cloud security strategy includes data encryption to protect sensitive information, IAM to effectively manage access, and security monitoring for threat detection. It should also include audits for compliance adherence, data backup for resilience, employee training to increase awareness, vendor risk management for third-party oversight, and patch management to address vulnerabilities quickly.
How Can You Make Cloud Environments More Secure?
To improve cloud security, follow the industry acknowledged best practices. To successfully address possible threats, develop robust access controls, encrypt data, update systems on a regular basis, conduct security assessments, enforce strong authentication, monitor for abnormalities, educate users, and establish clear incident response protocols.
What Are the Cloud Security Standards?
Cloud security standards are the foundation for safeguarding data, digital assets, and intellectual property against hostile assaults and security concerns in cloud environments. It also includes federal, international, and municipal standards such as ISO, PCI DSS, HIPAA, and GDPR, which have special requirements for cloud systems.
Bottom Line: Implement Strong Cloud Security Practices
Cloud security is a shared responsibility, and you can confidently navigate the cloud landscape by equipping yourself with knowledge of the best practices and most effective security strategies. Your adoption of a strong cloud security practice, combined with your cloud security provider’s maximum security measures, can keep your cloud environment secure. However, when your existing cloud security methods fall short, seek additional layers of security support.
Integrate your cloud security solutions with the top secure access service edge (SASE) providers to enhance your network security, visibility, and threat detection in cloud environments.




