A penetration test, or pentest, simulates a cyberattack to assess a network’s security to find and fix vulnerabilities before threat actors can exploit them.
Pentests are often performed by third parties, but as these outside tests can be expensive and become dated quickly, many organizations perform their own penetration tests with pentesting tools, using their own IT personnel for their red teams (attackers).
Many pentesters and ethical hackers use open source pentesting tools to probe a network‘s defenses, but for organizations with high security needs, there are also commercial pentest tools and services that can offer greater support and functionality, and some top open source tools offer pro and enterprise plans too. Here we’ll review seven of the best commercial pentesting tools, their benefits, drawbacks, and use cases.
Best Penetration Testing Tools & Software: Comparison Chart
Here is a head-to-head comparison of the best pentesting tools.
| Pentest tool | Best for | Integration with other tools | Vulnerability scanning/ assessment | Cross platform compatibility | Starting price |
|---|---|---|---|---|---|
| Fortra Cobalt Strike | Simulating a real cyberthreat | Yes | Yes | Yes | Start at $3,540 per user per year |
| Fortra Core Impact | Complex infrastructure penetration testing | Yes | Yes | Yes | $9,450 per user per year |
| Burp Suite Pro & Enterprise | Developers and DevSecOps professionals | Yes | Yes | Yes | Starts at $449 per user per year |
| Metasploit Pro | Vulnerability assessment and exploit development | Yes | Yes | Yes | $15,000 per year |
| Tenable Nessus | Network vulnerability scanning and assessment | Yes | Yes | Yes | $3,859.25 for 12 months |
| vPenTest | Managed service providers | Not available | |||
| Pentest-Tools.com | Visualization, reporting and analytics | Yes | Yes | Yes | $72 per month when billed annually |
Fortra Cobalt Strike – Best for Simulating a Real Cyberthreat
In 2012, Raphael Mudge — who also developed the Armitage GUI for Metasploit — developed Cobalt Strike, a commercial penetration testing tool primarily used as a threat emulation or post-exploitation tool to enhance adversary simulations and red team operations. Cobalt Strike allows attackers to mimic advanced threat actors and emulate their techniques, making it a popular tool among red teams and penetration testers for testing the security of organizations. Unfortunately, it’s also become a popular tool for hackers too. As a result, the tool is closely monitored and regulated, and its availability is restricted to licensed users or authorized organizations.

Also read: How Cobalt Strike Became a Favorite Tool of Hackers
Fortra Core Impact – Best for Complex Infrastructure Penetration Testing
Fortra owns the first two tools on our list, including Core Impact, a penetration testing tool that allows organizations to simulate real-world attacks on their network infrastructure and applications to identify vulnerabilities and weaknesses.
Featuring network testing, client-side testing, web application testing, remote exploitation, rapid penetration tests (RPTs), post-exploitation, and teaming capabilities, it enables security professionals to assess the security posture of their networks, identify potential vulnerabilities, and evaluate the effectiveness of their security controls. It allows users to customize and craft their own exploits, reflecting unique organizational requirements.

Burp Suite – Best for Developers & DevSecOps Professionals
Burp Suite is a top-rated software suite for attacking security testing developed by PortSwigger, available in both free and paid versions. Security professionals and penetration testers widely use it to identify and exploit vulnerabilities in applications.
Burp is a tremendous tool that can do advanced scans, but one of the most classic uses is traffic interception (e.g., HTTP requests). Burp Suite consists of several modules, including a proxy server, scanner, intruder, repeater, sequencer, and spider. Modules work together to perform various security testing tasks.

Also read: Getting Started with the Burp Suite: A Pentesting Tutorial
Metasploit – Best for Vulnerability Assessments & Exploit Development
Metasploit, developed by Rapid7, is a well-known exploitation framework that — like the free version of Burp — is also included in the Kali Linux open source pentesting distribution. Metasploit provides useful modules and scanners to exploit vulnerabilities. It allows security professionals and ethical hackers to assess a system’s security posture and replicate real-world attack scenarios to understand the potential risks and vulnerabilities.

Also read: Getting Started With the Metasploit Framework: A Pentesting Tutorial
Tenable Nessus – Best for Network Vulnerability Scanning & Assessments
Built for consultants, pentesters, developers, SMBs, and security practitioners, Tenable Nessus is a widely used vulnerability assessment tool. It offers a comprehensive vulnerability database, frequent updates, and a user-friendly interface.
Tenable Nessus can scan your infrastructure to identify security weaknesses, misconfigurations, and potential entry points for cyberattacks, reducing the risk of cyberattacks and data breaches.

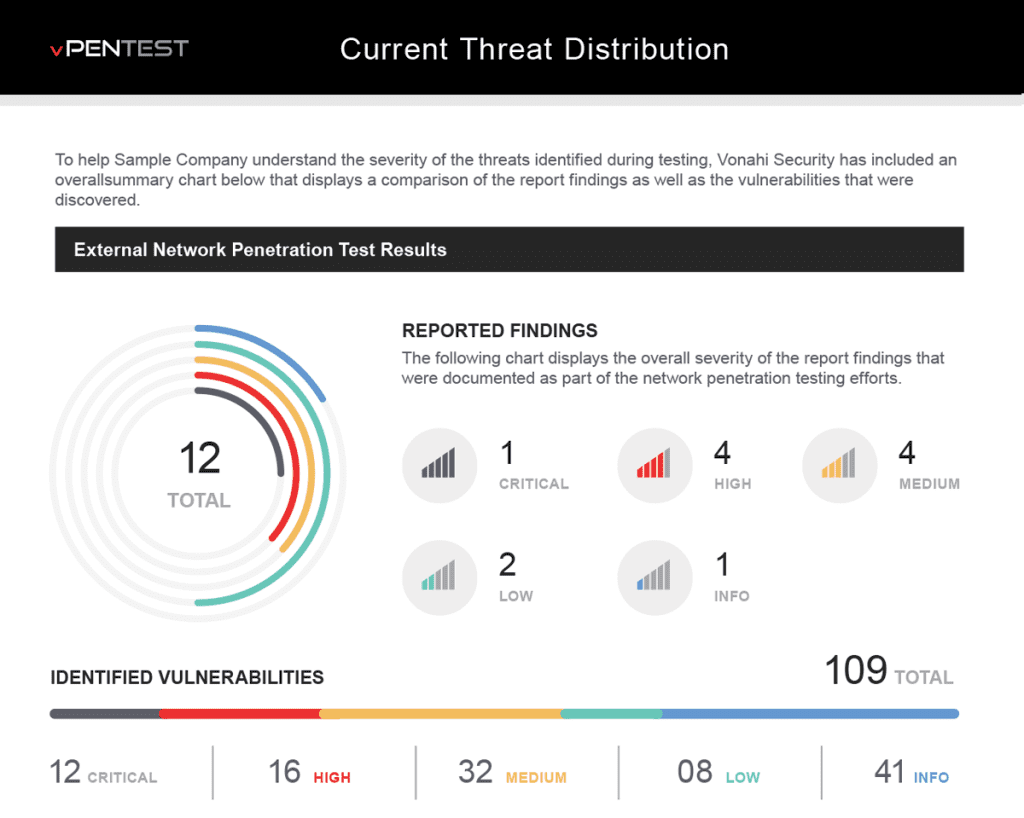
vPenTest – Best for Managed Service Providers
vPenTest, a product of Vonahi Security, is an automated network penetration testing tool designed for managed service providers (MSPs). It claims to combine the expertise of several highly competent penetration testers with the capabilities of numerous tools to perform a range of tasks, including host discovery, service enumeration, vulnerability analysis, exploitation, post-exploitation, privilege escalation, and lateral movement, as well as documentation and reporting.

Pentest-Tools.com – Best for Visualization, Reporting & Analytics
Pentest-Tools.com provides a variety of tools and resources for penetration testing and vulnerability assessment. It offers a collection of security tools, such as web application scanners and network scanners, which can be used by security professionals to identify vulnerabilities and test the security of their systems.

Key Penetration Testing Software Features
Here are some of the key features that buyers should look for in pentesting tools.
Vulnerability scanning
Pen testing tools often have databases of known vulnerabilities to identify potential weaknesses in an organization’s network, systems, or applications that could be exploited by attackers, making it easy for companies to tackle these loopholes before bad actors take advantage.
Also read:
- Penetration Testing vs Vulnerability Scanning: What’s the Difference?
- Best Vulnerability Scanning Tools
Exploit testing
Exploit testing capabilities enable you to simulate real-world cyberattacks. This involves attempting to exploit identified vulnerabilities to understand the potential impact and consequences of a successful attack.
Wireless network testing
With the increasing use of wireless networks, penetration testing software should have specific features to assess the security of wireless networks. This can include scanning for open ports, testing encryption strength, or attempting to gain unauthorized access through wireless access points.
Compliance and regulatory support
Penetration testing software should have features that enable organizations to align their testing with industry standards, regulations, and compliance requirements. This ensures that organizations can meet regulatory obligations and demonstrate due diligence in their security efforts.
Integration and collaboration
Many organizations have complex IT infrastructures and multiple security tools. Penetration testing software should have features that allow for seamless integration with existing security systems, such as SIEM platforms, CMDB, ITSM, and DevSecOps tools, to provide a holistic view of an organization’s security posture and to speed fixes.
Other capabilities to look for include:
- Exploit development: The ability to develop custom scripts and tools that leverage discovered vulnerabilities to gain access to a system or application.
- Password cracking: The ability to use brute force, dictionary, and hybrid attacks to crack passwords and gain access.
- Network mapping: The ability to map a network’s topology, revealing its devices, services, and open ports.
- Social engineering: The ability to use social engineering tactics, such as phishing and pretexting, to gain access to confidential information.
- Web application testing: The ability to test for vulnerabilities in web applications and web services.
- System hardening: The ability to secure a system by patching, updating, and implementing firewalls.
- Post-exploitation analysis: The ability to analyze a compromised system to identify and exploit further vulnerabilities.
- Malware analysis: The ability to analyze malicious software and develop countermeasures.
- Privilege Escalation: Exploiting vulnerabilities to gain higher-level privileges.
- Reporting and Documentation: Summarizing results and providing evidence of findings.
How to Select the Best Penetration Testing Tools and Software for Your Business
When shopping for a penetration testing tool, be aware that you will likely need several components to perform a complete penetration test. And some tools are more flexible than others. Some software solutions let users define custom rules according to a specific use case.
The right pentesting tool will depend on the type of pentesting you plan to perform. For example, if you are performing a network pentest, you may do fine with an open source network pentesting tool such as Nmap. If you are performing a web application pentest, you will need a web application pentesting tool such as Burp Suite.
Each type of pentest will require different tools to complete the task, so it is essential to identify the kind of pentest you plan to perform and choose the appropriate tools for the job.
- Understand your requirements: Identify your organization’s specific security goals and objectives and determine the scope of the penetration testing (for instance, network, web applications, mobile apps, and wireless networks).
- Assess your resources: Make sure any solution matches your existing tools and human expertise.
- Research and shortlist tools: We’ve helped get you started, but now you need to find the right tools for your environment.
- Evaluate tool features: Compare the features of shortlisted tools against your organization’s requirements.
- Consider the tool’s security and service: Updates, training and support, as well as the vendor’s reputation, also matter.
- Test and try: You can request a demo if a free trial is unavailable.
Review Methodology
We reviewed over 60 penetration testing tools using 28 individual data points across five key categories: price/value, core features, non-core features, admin ease of use & implementation, and support. We collected information about each tool’s features, pricing, and other relevant information from their respective websites, data sheets, whitepapers, and documentation. We then used the data to score the best penetration testing tools and software as follows:
- Pricing/value (20%)
- Core features (40%)
- Non-core features (5%)
- Admin ease of use & implementation (20%)
- Support (15%)
We at eSecurity Planet have your best interest in mind. We selected the top-rated tools after careful consideration, calculation, and extensive research to help you determine the best tools for your needs and use cases.
Bottom Line: Choosing a Pentesting Tool
Penetration testing is a critically important security practice and will reduce the likelihood and opportunities for a cyber attack. There are a few different ways to do it — pentesting services, security staffers with expertise, and even automated tools — but the most important thing is to get started.
Read next:
- How Much Does Penetration Testing Cost? 11 Pricing Factors
- Top Breach and Attack Simulation (BAS) Tools
This updates a February 2022 article by Julien Maury