A DMZ network, or a demilitarized zone, is a subnetwork in an enterprise networking environment that contains public-facing resources — such as web servers for company websites — in order to isolate them from an enterprise’s private local area network (LAN).
Also referred to as a perimeter network or screened subnet, a DMZ network acts as an additional layer of network security, isolating itself and its contents from the parts of the enterprise network where more sensitive and private resources are more securely kept. While users can interact with public networks and whatever resources are provided in the DMZ, DMZ perimeter security keeps the organization’s private network private and secure from outside users.
A Comprehensive Guide to DMZ Networks
- What Is the Purpose of a DMZ Network?
- How DMZ Networks Work
- 5 Benefits to DMZ in Networking
- 4 DMZ Networking Examples
- DMZ Network Best Practices
- Bottom Line: DMZ Networks
What Is the Purpose of a DMZ Network?
The purpose of a DMZ network is to balance reasonable access to resources with effective isolation and security measures.
For companies that offer digital products and services, chances are they want some of their resources to be available for customers, while other data and systems need to remain hidden from external users. An effective way to make sure users can only access the resources they need is to isolate them in a new subnetwork or network segment with its own access, security, and operational rules.
DMZ networks typically contain external-facing resources such as DNS, email, proxy and web servers.
DMZ networks are also helpful for separating out third-party servers, routers, and other technologies and platforms that don’t have as many manageable security features and controls built in. By isolating these less secure assets in a single location, network administrators can easily monitor and identify anomalous network traffic before it breaches the main network.
DMZ networks are primarily used to manage outside user access and give network administrators more network security and monitoring support. However, when your DMZ network includes a proxy server, administrators also have the option to filter all internal internet usage through the DMZ. This approach requires employees to use public networks according to their organization’s rules while also giving network security professionals additional visibility into internet usage across the organization.
Also read: Network Protection: How to Secure a Network
How DMZ Networks Work
DMZ networks work through isolation, but first, through network segmentation. Network administrators that want to create a DMZ need to first determine which parts of their network should be available for outside users. They can also use this time to identify any network components that operate with lesser security controls that put the rest of the network at risk.
These are the kinds of servers and resources you’ll often find on a DMZ network:
- VoIP servers
- Proxy servers
- Web servers
- Email servers
- DNS servers
- FTP servers
- Third-party routers and servers
- Other external services, resources, and servers
Now, these resources need to be isolated from the rest of the enterprise network and placed on a DMZ subnetwork. The DMZ should be set up with at least one gateway device (typically a firewall) that will filter external network packets through to the DMZ and monitor for unusual traffic or activity. In many cases, a dual firewall layout is implemented for a second round of network packet filtering before the LAN (see image below).
Many DMZs and the firewalls that protect them include advanced security features and tools, such as network access control (NAC) technology and proxy servers for optimized traffic monitoring. These and many other network security solutions are ramped up specifically on the DMZ, making it so network administrators can often detect unusual behavior before unauthorized users try to move past the DMZ to access the LAN.
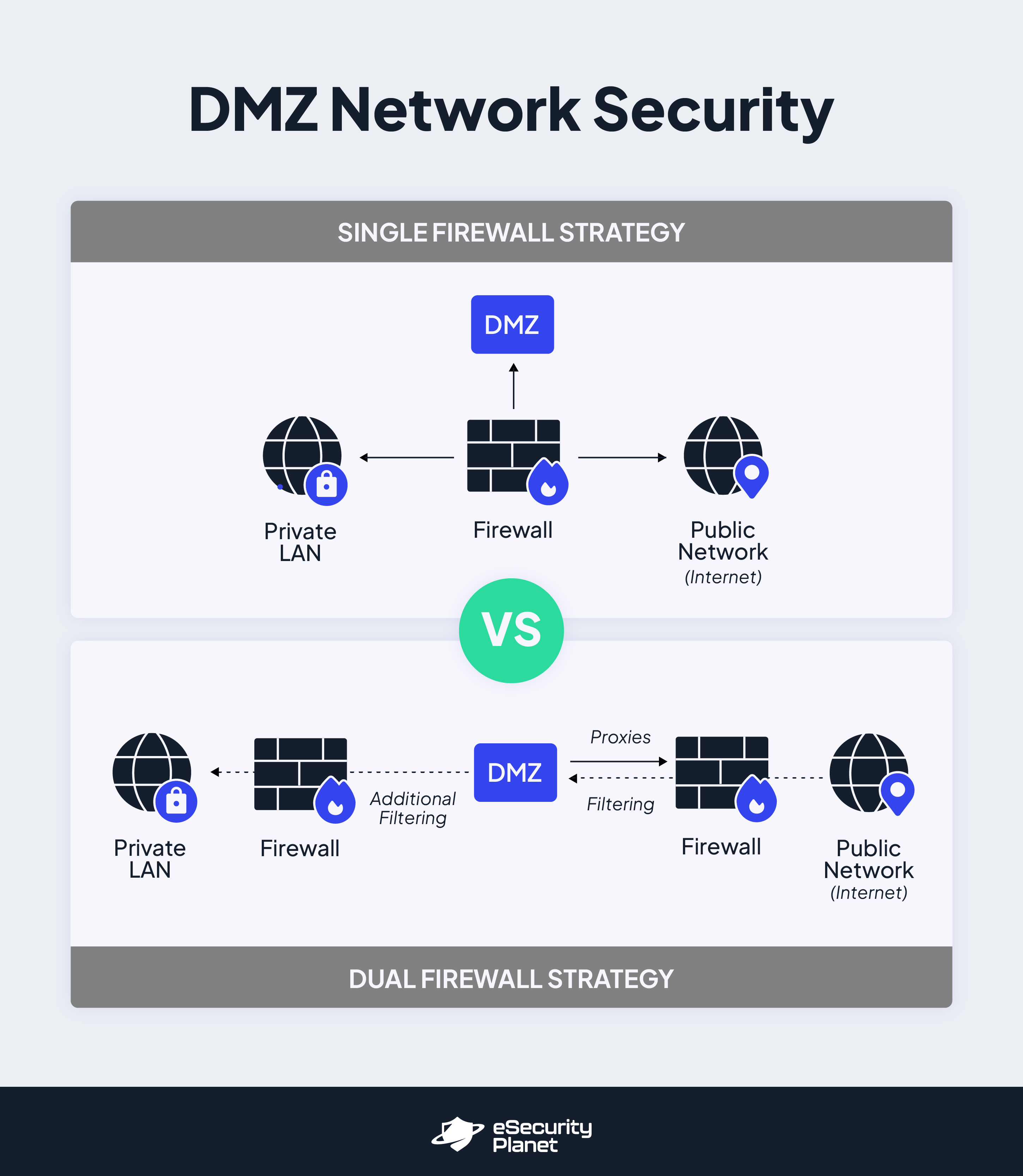
DMZ Architecture
There are two main layout options to choose from when developing a DMZ subnetwork: a single firewall layout and a dual firewall layout.
With a single firewall layout, the firewall sits in the middle of the private LAN, the DMZ, and the public network; no users can travel directly from one of these networks to another without first passing through the centralized firewall, which filters and monitors all traffic. This model is much easier to implement, but it is generally considered less secure since only one firewall needs to be compromised for a successful cyberattack to breach the LAN.
In a dual firewall layout, two different firewalls are used for tiered network packet filtering. The front-end firewall sits between public networks and the DMZ to filter and manage traffic before it enters the DMZ. If a user attempts to move from the DMZ to the LAN, a back-end firewall sits between these two networks to further filter and authorize traffic. The dual firewall setup is generally considered more secure, but it’s also harder to manage.
See the top next-generation firewalls (NGFWs)
5 Benefits to DMZ in Networking
DMZ networks provide the isolation necessary to protect the main network from public-facing threats, but they also create an environment where focused security tools can be used to monitor and protect vulnerable DMZ resources. These are some of the benefits you can expect from the implementation of a DMZ model:
Isolation adds an additional layer of protection
DMZ development requires network administrators to segment their networks so potentially unsecure and public-facing resources are identified and isolated from everything else. This isolation is particularly valuable when organizations need to work with resources or servers that have fewer native security controls, such as FTP servers.
These kinds of servers and modern technologies like the Internet of Things (IoT) and operational technology (OT) are important to overall network operations but can be detrimental to everything else on the network if breached. When these kinds of resources are isolated in a dedicated environment like a DMZ, even successful security breaches aren’t likely to reach the LAN.
Avoids common network performance lags
Especially for resources that your customers will regularly be accessing, high speeds and performance are key to the user experience. DMZs are designed in a way that optimizes network performance because they separate frequently used and high-workload resources, like web servers, from the rest of the internal network. With that separation, network admins are able to optimize the DMZ for high traffic volumes without affecting internal network resource allocation.
Focused security tools and notifications
DMZ isolation can offer great support for internal network security, but DMZ networks themselves are also ideal environments for security tools. Most DMZs incorporate multi-functional firewall technology as well as network access control, proxy servers, information security policies, network monitoring, vulnerability management, and other features to protect the environment and alert network administrators when something’s amiss.
Learn about the 34 Most Common Types of Network Security Protections
Compatibility with proxy servers
If your organization implements network access control tools and specific rules on its DMZ network, you can require all internal traffic moving toward the internet to follow specific rules and visit only approved IP addresses. This is because DMZ networks are compatible with proxy servers that make this kind of traffic steering possible.
Proxy servers are also helpful for monitoring types and quantities of traffic. Proxies on DMZs are particularly helpful for healthcare organizations and other industries in which compliance management and data security are crucial operating factors to consider.
See the top secure web gateways
Improved visibility for network administrators
Network administrators have a lot of network features, functions, users, devices, and applications to manage at all times. Especially on networks with limited network security personnel, it can quickly become overwhelming to monitor and address all network security issues. It’s even more difficult if your network uses tools that have limited security features and require more hands-on monitoring than everything else.
With a DMZ in place, network administrators are able to divide up different types of network resources into the main network and the DMZ subnetwork. This division makes the more problematic security configurations readily apparent in the DMZ network.
Because admins manage both environments, they still have as much control over these resources as they did before. Now, they simply have a more efficient way to monitor vulnerable network assets and services.
4 DMZ Networking Examples
A DMZ can help any organization with a main network and web-facing assets, but here are a few specific use cases where a DMZ can help.
Data-driven user experience on a company website
Whether you’re running an e-commerce business or are a healthcare provider, you likely have a customer-facing website that enables users to make purchases and complete other actions with company data and systems. This website requires a web server running on your network.
Unless the network is segmented, unauthorized users could potentially move from the website and data they’re supposed to access into the rest of the private network. With a DMZ, the web server and other customer materials are isolated from a company’s private assets, making it so users cannot easily move laterally from the web server to the internal network.
See the Top Microsegmentation Software
Hybrid cloud environments
Let’s say your company has been operating for multiple decades and has some of its most important assets and applications on-premises. However, many other applications and services you now use are hosted in the cloud.
In this hybrid cloud environment, you have resources on-premises that need to interact with your cloud assets, but at the same time, you don’t want both aspects of your network to have full, unbridled access to each other. In this scenario, a DMZ network can be set up between the cloud environment and the on-premises network to audit and filter traffic moving between the two.
See the top cloud security companies
Production and manufacturing device security
Manufacturers and critical infrastructure industries are increasingly investing in newer technologies like IoT and OT devices, which open up businesses to new operational use cases — and new security vulnerabilities. Most of these kinds of tools are designed to store and transmit a lot of data but don’t necessarily have many security features in place, due to the speed and capacity required of these tools. When an IoT or OT device operates on the same networking plane as other assets, then, it opens all of them up to greater security risk.
DMZs can isolate these kinds of devices from the rest of the network, making them accessible internally and externally while upholding firewall filtering rules to limit any lateral movement if a breach occurs.
DMZ hosts for home computer networks
Home computer networks are much smaller but still contain personally identifiable information (PII) and other features for which you’ll want to limit access to known users. Unfortunately, home networks tend to be easy to hack due to limited security investments on the part of the owner.
A DMZ host is an easy thing to set up with existing technologies in your home, such as a gaming console. The selected host device sits outside of the firewall and acts as a filter for all incoming traffic, giving the rest of your devices and your internal network more protection from unauthorized outside users. For this use case, it’s important to select a DMZ host device that contains minimal sensitive data and private information, as it will be outside of the firewall’s protection.
DMZ Network Best Practices
Setting up a DMZ network can be a great security addition if it’s configured correctly. Consider these best practices and tips during your implementation process for better outcomes:
Label all networks and network segments
As obvious as it may sound, you need to clearly label each part of your network so it’s clear what’s operating where, how, and why. This will save time during initial setup, make ongoing reconfigurations easier, and also create usable documentation if your network security team changes over time.
Clearly define and enforce isolation rules
Your DMZ is only as effective as the filtering rules and policies you set up. It’s important to research every feature of your network and be able to justify why something does or does not need to go into the DMZ; similarly, it’s important to program your firewalls and any other security tools you set up on the DMZ to reflect and enforce your security policies for all device and traffic types.
Also read: Fine-tuning Firewall Rules: 10 Best Practices
Use a dual firewall strategy for added protection
A dual firewall setup is harder to manage than a single firewall, but it’s also more effective at filtering out malicious traffic. If you plan to implement a dual firewall architecture, consider working with a different provider for each firewall to diversify your security setup and make it more difficult to take down all infrastructure in an attack.
Choose the right kinds of firewalls
Not all firewalls are created equal and not all firewalls work for the same scenarios. Because you’re trying to filter traffic at a very granular level that’s driven by applications and individual users, a proxy firewall or application-level gateway is typically the best option for your DMZ.
Also read: Types of Firewalls Explained
Incorporate zero trust best practices
DMZs work best in cooperation with zero trust network access (ZTNA). With ZTNA solutions, traffic is denied unless it explicitly passes your predefined user access control policies. Combined with DMZ isolation, it’s a great way to stop unauthorized access to the LAN.
Don’t forget vulnerability management
Vulnerability management tools, like vulnerability scanners and vulnerability assessments, are incredibly helpful assets for regularly monitoring network traffic in a DMZ. But don’t just invest in vulnerability management solutions; also take the time to develop a vulnerability management policy and process that makes sense for your organization.
Monitor and audit DMZ performance over time
Be sure to invest in tools and personnel for DMZ traffic monitoring, as it may require more constant and vigilant oversight than the rest of the network. As new tools, applications, and users are brought onto your enterprise network, frequently evaluate whether or not they should be moved to the DMZ and what changes will be necessary if that move happens.
See the Top Network Detection & Response (NDR) Solutions
Bottom Line: DMZ Networks
Some people now consider DMZ networks outdated or ill-fitting for the modern enterprise network, especially since many networks have moved past technologies like internal web servers in favor of cloud computing and cloud-hosted networks. There are also several newer networking and security options, such as SD-WAN, containerization, virtualization, SASE, and ZTNA, which seem to offer more comprehensive security support for modern cloud environments than DMZ’s form of perimeter security.
However, DMZ still proves useful in many cases, especially when hardware or on-premises networks need to be part of a secure and integrated environment with access management rules. When a DMZ network is implemented in the right scenarios, your business can more easily isolate unsecure devices, operate hybrid networks with appropriately-integrated legacy components, and streamline the network monitoring process for network administrators.
Further reading:




