Encryption uses mathematical algorithms to transform and encode data so only authorized parties can access it.
A solid understanding of encryption is important, as it safeguards everything from financial transactions to private communications. As cyberattacks become more sophisticated, encryption remains one of the most effective ways to protect sensitive data from breaches and unauthorized access.
This guide breaks down the core principles of encryption, its major types, and commonly used algorithms so you can better understand how data is secured and why encryption is vital in modern technologies.
What Is Encryption?
Encryption protects data by converting it into an unreadable format that can only be decoded with the right key. It ensures that sensitive data remains secure, whether stored on a device or transmitted over a network, preventing unauthorized access. Encryption is a fundamental part of data protection, and it is used in everything from online banking to secure messaging.
How Does Encryption Work?
Data is scrambled into ciphertext during encryption, protecting sensitive information from unauthorized access. This ciphertext can only be converted to its original, readable plaintext format using a specific decryption key.
Encryption transforms data into an unreadable format by applying an algorithm, which determines how the data is altered. Without the corresponding decryption key, the encrypted data remains locked, even if intercepted by an unauthorized user.
Types of Encryption
There are two main types of encryption, each designed to address different security needs. The key difference between them is how encryption and decryption keys are used, which impacts their speed, security, and practical applications.
Encryption Algorithms
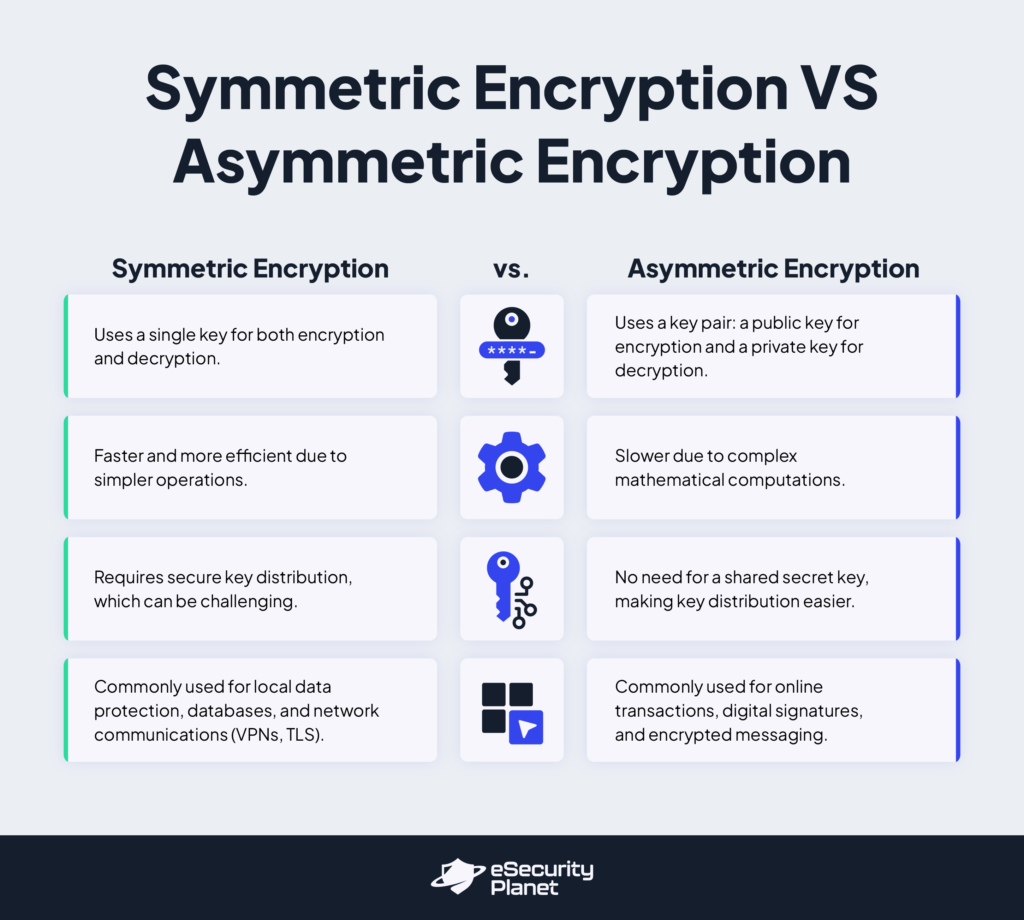
- Symmetric Encryption: This uses a single key for both encryption and decryption. Since it uses simpler operations, it is more efficient and faster than other methods. However, secure key distribution presents a significant challenge. Symmetric encryption is commonly used for protecting locally stored data, databases, and network communications, such as virtual private networks (VPNs) and transport layer security (TLS).
- Asymmetric Encryption: This type relies on a pair of keys — a public key for encryption and a private key for decryption. The public key can be shared freely, allowing anyone to encrypt messages while only the private key owner can decrypt it. This removes the need for a shared secret key but operates more slowly due to complex mathematical computations. Asymmetric encryption is typically used for securing online transactions, digital signatures, and encrypted messages.
Encryption algorithms use mathematical and computational processes to transform data into an unreadable format. These algorithms are constantly tested for weaknesses; those found vulnerable will be replaced.
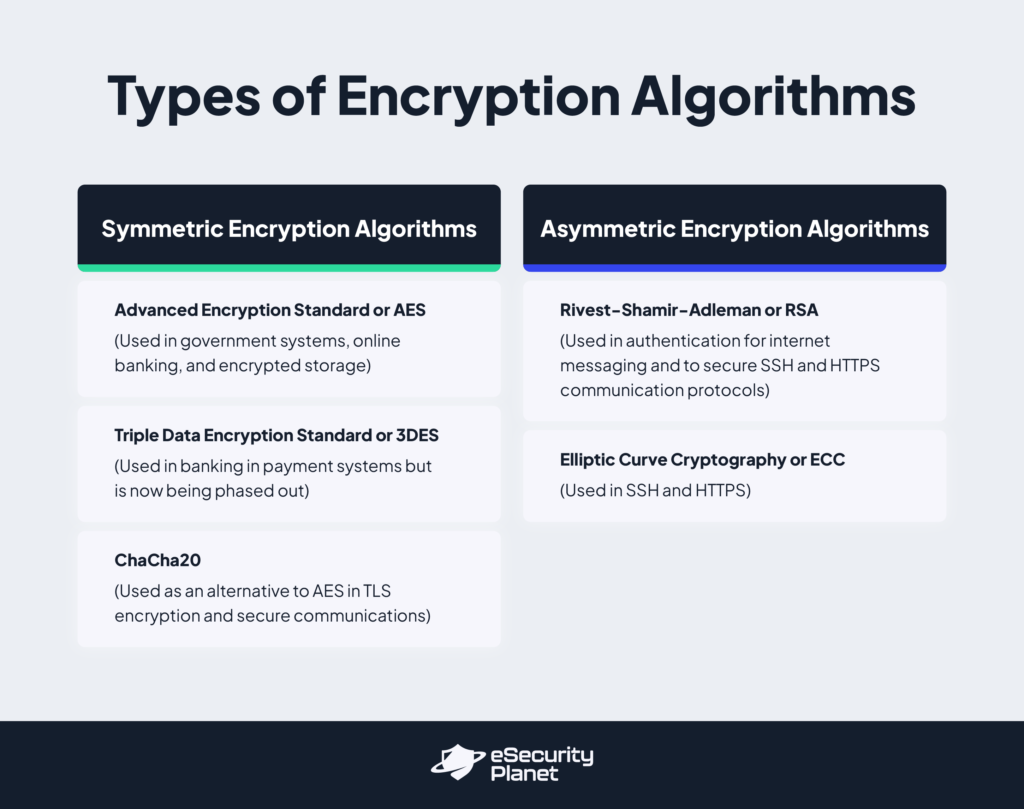
Symmetric Encryption Algorithms
- Advanced Encryption Standard or AES Encryption: A secure and fast encryption algorithm that protects data by scrambling it into fixed-sized blocks (128-bit) using key sixes of 128, 192, or 256 bits. AES is widely used in government systems, online banking, and encrypted storage because it offers robust security with high-speed performance.
- Triple Data Encryption or 3DES Encryption: An older encryption method that applies the DES algorithm three times to improve security. It was commonly used in banking and payment systems but is now being phased out because it is slower and less secure than newer options, like AES.
- ChaCha20: A modern encryption algorithm designed for speed, even on mobile devices and low-power hardware. It delivers reliable defense and resistance to cryptographic attacks, making it a widely used alternative to AES in TLS encryption and secure communications.
Asymmetric Encryption Algorithms
- Rivest-Shamir-Adleman or RSA Encryption: A widely used method that relies on the difficulty of factoring large numbers into their prime components, making it highly resistant to attacks. RSA requires extremely long key lengths to remain secure and is, therefore, slower than newer alternatives. It is often used to authenticate internet messaging and secure communication protocols, such as SSH and HTTPS.
- Elliptic Curve Cryptography or ECC Encryption: A newer encryption algorithm that provides enhanced security with shorter key lengths than RSA. Because it needs less processing power, ECC is ideal for mobile apps, cryptocurrency transactions, and internet messaging.
Advantages of Encryption
Encryption protects data in IT environments, offering three key benefits: compliance, confidentiality, and integrity.
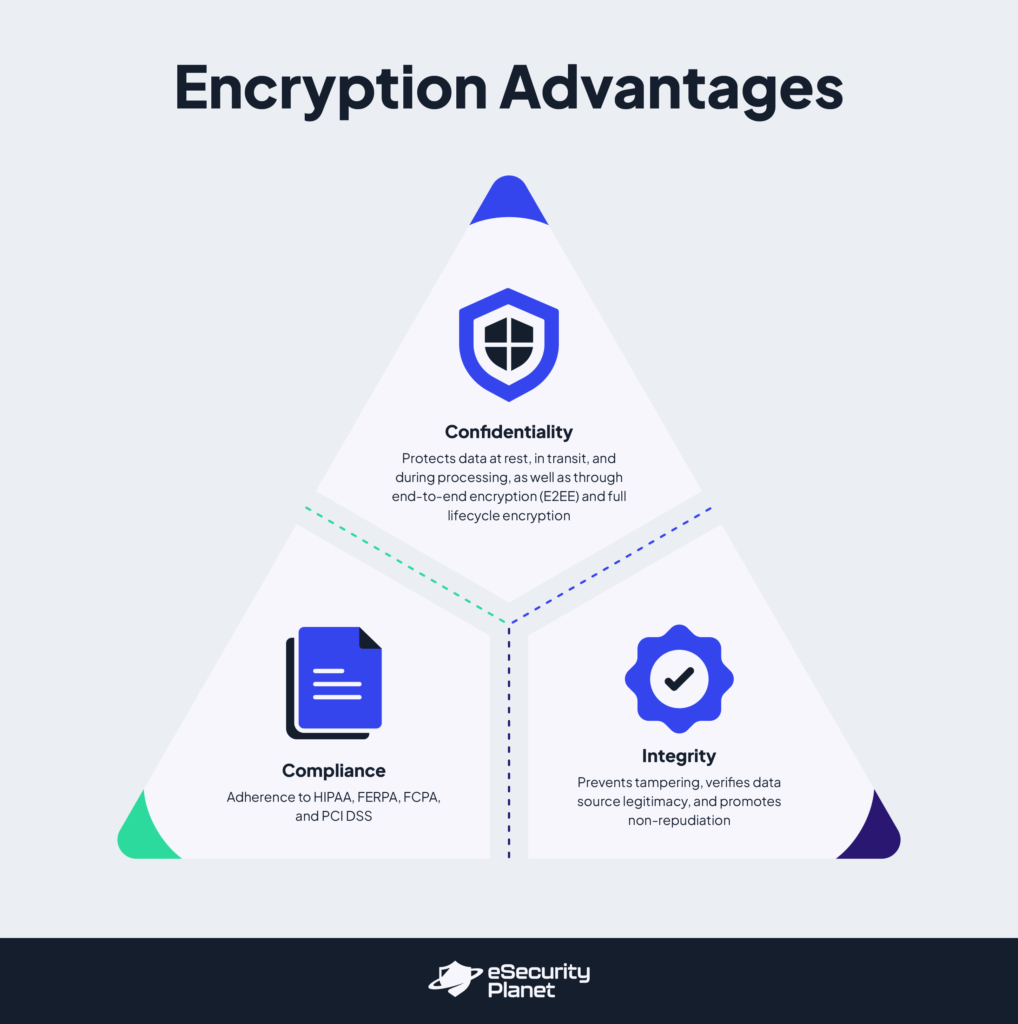
Compliance
Many regulatory standards mandate encryption to safeguard sensitive data at rest and in transit. Organizations must implement appropriate encryption solutions to comply with these regulations so data remains protected at all times. Examples of these standards include:
- Health Insurance Portability and Accountability Act (HIPAA): Requires encryption to protect patients’ health information.
- Family Educational Rights and Privacy Act (FERPA): Mandates encryption or equivalent security measures for private student records.
- Fair Credit Practices Act (FCPA) and Payment Card Industry Data Security Standard (PCI DSS): Both order secure storage and transmission of financial and personal data.
Confidentiality
Encryption helps prevent data breaches, even in cases of cyberattacks, lost devices, or intercepted communications by making data unreadable to cyber criminals and unauthorized users. It upholds confidentiality at various stages of data storage, transfer, and use:
- Encryption Across Data States: Protects data stored in local devices or cloud repositories, transmitted between systems, or during processing to stop any unauthorized access at any stage.
- End-to-End Encryption (E2EE): Keeps data encrypted from sender to recipient. This way, only the intended recipient can decrypt the data, avoiding interception or unauthorized access.
- Full Lifecycle Encryption: Secures data across all phases of its existence, from creation to deletion, minimizing exposure risks.
Integrity
Encryption not only protects data but also safeguards its authenticity and accuracy. By maintaining data integrity, encryption fosters trust in digital communications and transactions. Secure transmission protocols use encryption to:
- Prevent tampering and unapproved modifications during transit: For example, TLS encryption protects transmitted data from being altered by attackers.
- Verify the legitimacy of data sources: HTTPS encryption, for instance, ensures a website’s identity is authenticated to avoid impersonation.
- Ensure senders cannot deny their role in transmission, promoting non-repudiation: Encrypted communication logs present verifiable proof of message origin and delivery.
Challenges of Encryption
Encryption is indispensable in data protection, which is a key component of cybersecurity. However, it introduces potential challenges that organizations must overcome to improve overall security posture.
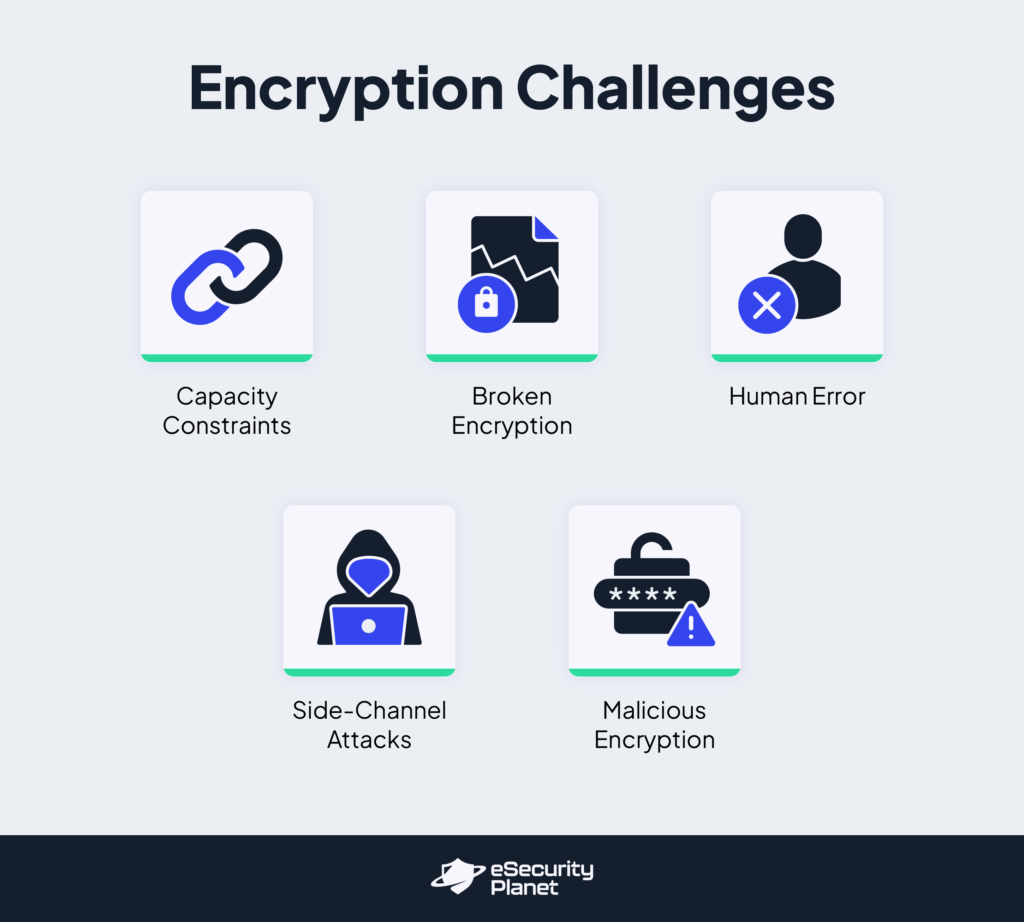
Capacity Constraints
Securing data with encryption takes processing power, which can be challenging for resource-limited devices like IoT and mobile devices. These devices are built to be efficient, so full encryption might be impractical.
Mobile phones and tablets also have to balance speed and battery life, which limits encryption options. Similarly, servers with limited resources might run slower if equipped with extensive encryption.
Organizations can mitigate these issues by restricting sensitive access to these types of devices and adopting lightweight cryptography to reduce computational demands. Zero trust architecture also helps ensure that even resource-limited devices undergo strict access controls before processing sensitive data.
Broken Encryption
Encryption can fail due to outdated algorithms, brute-force attacks, and government-mandated backdoors.
- Outdated Algorithms: Encryption weakens over time. Organizations should replace vulnerable algorithms, such as upgrading from 3DES to AES.
- Brute-Force Attacks: Weak passwords and short key lengths increase risk. While modern encryption is secure, quantum computing could accelerate decryption. Implementing multi-factor authentication (MFA) and quantum-resistant cryptography can mitigate this threat.
- Government Backdoors: Some governments mandate encryption backdoors, which attackers could exploit. Layered encryption methods help reduce exposure.
Human Error
The effectiveness of encryption depends on proper implementation. Weak passwords, lost keys, and mismanagement can lead to breaches. Some users choose easily guessable passwords; lost keys can make data irretrievable.
Organizations must enforce strong password policies, train employees on secure key management, and use centralized encryption controls to reduce these risks. Identity and access management (IAM) tools help reinforce role-based access, while data loss prevention (DLP) software prevents unauthorized key exposure.
Side-Channel Attacks
Even when encryption algorithms are reliable, attackers can extract sensitive information by analyzing physical or behavioral patterns during encryption. Power consumption, electromagnetic emissions, and timing variations can reveal cryptographic keys or data.
Mitigating these attacks requires hardware-based security measures, such as shielding against electromagnetic leaks and power analysis countermeasures in cryptographic hardware. Organizations can also use next-generation firewalls (NGFWs) and secure web gateways (SWGs) to inspect encrypted traffic and block malicious communications.
Malicious Encryption
Threat actors use encryption to hide threats and disrupt operations. They may launch ransomware attacks, which lock data until a ransom is paid, or encrypted command and control (C2) traffic to evade detection.
Network monitoring solutions, endpoint detection and response (EDR) tools, and policies restricting unauthorized encryption software can help overcome malicious encryption. Antivirus software can help identify and contain ransomware before it spreads. In addition, disaster recovery strategies empower organizations to restore encrypted data without paying ransom.
Frequently Asked Questions (FAQs) About Encryption
What Does Encrypting a File or Email Do?
Encrypting a file or email scrambles the message, which can only be deciphered with a decryption key. Therefore, if the file or email is intercepted, the contents remain private and secure, accessible only to those with the correct key.
Why Is Encryption Important?
Encryption is important because it safeguards sensitive information from unauthorized access, keeping it unreadable to anyone without the correct key and preventing data breaches. Without it, confidential information would be exposed to cybercriminals, leading to identity theft, financial fraud, and corporate espionage.
What Type of Data Should Be Encrypted?
Sensitive data should be encrypted, including personally identifiable information (PII) like financial data, health records, and biometrics. Encryption is also a must for securing data at rest, like in databases and on storage devices, as well as data in transit, such as emails and communications sent over networks. Protecting intellectual property and any confidential business information is also recommended.
Bottom Line: Stop Ignoring and Start Adopting Encryption
Encryption isn’t just for big corporations. It’s a practical way for any organization to keep sensitive data out of the wrong hands. Without it, stolen data could cause financial losses, reputational damage, and legal trouble.
While encryption has challenges, security tools can help streamline encryption management and enhance data protection. Understanding encryption — how it works, its real-world uses, and its challenges — helps organizations bolster their defenses against growing cyber threats.
Elevate your data security strategy by pairing encryption with extended detection and response (XDR) and privileged access management (PAM) tools. Read our guides on the top XDR and PAM solutions to find the right fit for your organization.
Liz Ticong updated this article in February 2025.




