A firewall audit is a procedure for reviewing and reconfiguring firewalls as needed so they still suit your organization’s security goals. Over time, business network needs, traffic patterns, and application access change. Auditing your firewall is one of the most important steps to ensuring it’s still equipped to protect the perimeter of your business’ network. Your business can either do the audit yourself or hire a firewall specialist vendor to perform one.
How Does a Firewall Audit Work?
A firewall audit is a thorough procedure that requires your IT and security teams to look closely at your firewall documentation and change management processes. Audits raise questions about firewall functionality, as well as force teams to get granular about who’s in charge of firewall rules. They lay a foundation for continuous network security updates and improvements.
To successfully execute an audit, first determine your audit’s objectives and collect the data your team needs. Then, review your firewall rules and whether they’re still a good fit for your security infrastructure and overall network security. Your teams should also know who’s responsible for the request and upkeep of each rule. A good firewall audit should end with a clearly scheduled audit in the future, as well as testing processes so you know if the firewall actually works.
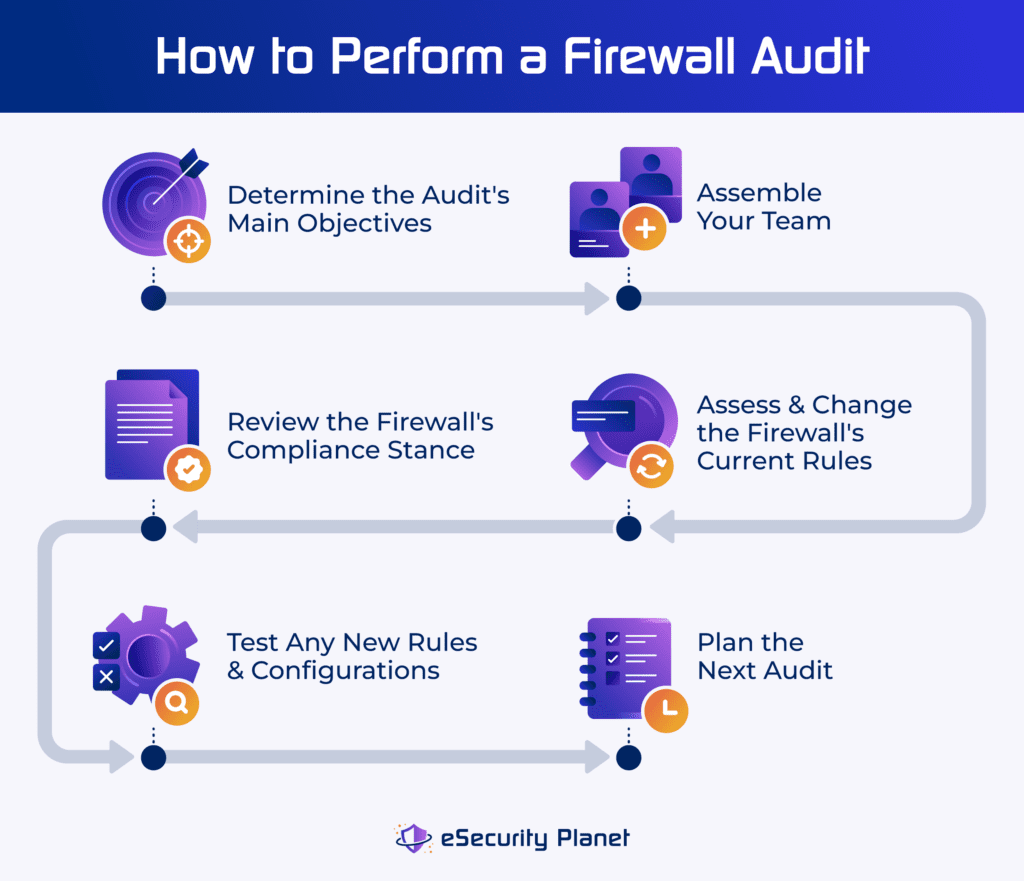
11 Steps to Perform a Firewall Audit
Your security, IT, or networking teams can use the following steps as guidelines to complete your audit, or to find a vendor who will perform the audit for you.
1. Know Your Audit Plan & Objectives
Sit down with your IT, security, or networking teams and ask, What exactly are we trying to accomplish with this audit? Then, develop a list and make it succinct. Maybe you’re trying to weed out some irrelevant rules, or your business’s executives want to know exactly what the firewall is filtering. Audits often have multiple purposes, so it’ll likely be a combination of items.
Create ordered steps to follow during the audit — they may be similar to our list here. Make sure every team member knows their job and when to perform it. This includes setting credentials and role-based access controls for the appropriate employees so they can view and configure the right technology.
Your team may want to use a specific software to track the list of objectives and steps, or you may just use a Google or Word document and share it with relevant stakeholders. Whichever you choose, make sure it’s easy to access and understand.
2. Gather All Relevant Data
Pull all necessary information before you start the actual audit. Pre-audit data should include:
- Logs: Firewall logs contain data about protocols and IP addresses and are useful for seeing what’s actually happening on the network.
- A list of rules: Have all your firewall rules in front of you so you can decide which are still useful and which no longer are.
- Everyone’s responsibilities: Find out who’s available during an audit (for example, know whether the head of IT will be on PTO during the potential audit timeline).
By organizing this information in advance, you’ll be less likely to run into a snag halfway through the audit because you’re missing data or guidelines for team members. A shared folder is a good location to store multiple sources of data.
3. Determine Change Management Procedures
It’s possible your team already has a change management process or solution, but make sure it’s clearly defined and documented. Additionally, confirm whether the owners of that process have shared any relevant documentation with new team members, and ensure that everyone knows how to submit a change request or access the documentation.
Also consider whether a change management software tool would be helpful for your team. Small businesses and large enterprises alike benefit from the organization of firewall changes, and those changes shouldn’t happen randomly. While change management tools take initial time to learn, they can save time long-term by simplifying requests and approvals, especially when adding or removing firewall rules.
4. Check the Firewall Hardware & Operating System
After you’ve prepared all the documentation and know everyone’s roles, one of the early steps in a firewall audit process is a hardware and firmware check. Look at the hardware to see whether it fits your company’s standards and security requirements. For example, some legacy networking hardware might have hardcoded default credentials — these can’t be changed from their factory settings. Those networking appliances should be replaced as soon as possible.
Check firmware, too. Is the OS up to date on all patches? Complete any necessary security upgrades and make sure the hardware is updated to the latest version. Also, check your firewall vendors’ security bulletins for recent vulnerabilities, since firewall appliances and security gateways often have back doors and other exploitable weaknesses.
While next-generation firewalls (NGFW) are higher-security products than more simple firewalls, they shouldn’t be exempt from initial checks and patches. NGFWs also need regular updates and management to properly protect networks. Run vulnerability scans on your NGFWs, too.
5. Perform a Risk Assessment
Assess your firewall hardware and software for all risks. This includes digital risks, like unpatched firmware, and physical risks, like a server room that doesn’t require keyholder access. A risk assessment includes categorizing each risk, so your teams know which to prioritize.
Don’t forget regulatory compliance, either. Consider purchasing software that helps your security team remain compliant with any relevant industry standards, like HIPAA, SOX, and PCI-DSS. Some regulations may require specific firewall configurations or data protection mechanisms.
Vulnerability scanning products that support firewalls are also helpful — they’ll flag back doors and weaknesses in your hardware and configurations. If you’re a large enterprise, a penetration testing service could provide massive long-term benefits. These services comb through your infrastructure, including firewalls, in detail to find vulnerabilities. Hiring a pentester is especially useful for first-time firewall audits.
6. Review Firewall Rules & Determine Best Practices
Firewall rules are the tools that tell firewalls how to behave, managing which traffic they should accept and discard. Rules specify certain ports, protocols, and traffic so firewalls know exactly which IP addresses to allow through and which traffic to allow to leave the network.
Sometimes firewall rules become irrelevant over time. Your business might need to allow an IP address or set of addresses that was previously blocked. Additionally, rules developed over a period of time by different admins can become redundant. During a firewall audit, check for repetitive rules or ones that no longer fit your business’s security objectives. Then delete those, ensuring no gaps are left in the firewall.
Involve the change management process heavily here. How does your business want to request and approve firewall rule changes? Who’s allowed to request, who’s responsible for those approvals, and who takes over responsibility for approvals if an admin leaves the company? These are all questions to answer during an audit.
7. Review Logs to Find Ongoing Patterns
Firewall logs collect packet and transmission data, storing that information for admins to review. Log files can reveal traffic patterns over time, which is a helpful resource for teams as they decide which rules work well, which don’t, and which new ones need to be created.
For example, if a study of log files during a firewall audit reveals that traffic has come from a certain IP address to a certain port at a strange time of day, research that further. If the traffic source is malicious, admins can create a rule blocking that IP address on the port.
8. Review Blocklists & Allowlists
Blocklists (or blacklists) and allowlists specify IP addresses that are forbidden or permitted to connect to an organization’s network. These may fall under your team’s firewall rules, but they’re important enough to mention on their own. Blocklists and allowlists improve granularity of firewall rules. Some highly protected networks might even use an allowlist for the entire network — only traffic from a few specific IP addresses can pass through the firewall at all.
The IT team may have certain websites that they know contain malware downloads or just have unsafe connections. When they put the IP addresses from those sites on a blocklist, no one who’s connected to the company network can access the sites. While blocklists don’t cover every threat, they’re a good way to eliminate known ones right off the bat.
9. Look at Overall Security Compliance
We briefly touched on compliance when talking about risk assessments, but overall compliance is bigger — this includes all your business’s security policies. First, check to see if the policies are up to date. They should also be clearly documented and easy to find for all relevant stakeholders. Once your teams have determined that policies are updated and documented, check that the firewall’s configuration is in line with the organization’s overall policy.
Maybe the security policy requires that the firewall software implements multi-factor authentication, or maybe only a certain number of people are permitted to access the server room where firewalls are installed on-premises. You’ll want to be able to provide a thorough report to the executive team, proving that the firewall configuration matches policies, if you’re asked.
10. Update All Roles & Admin Permissions
This goes hand in hand with the previous point, but update every role and its related access controls, including administrative roles. It’s possible that an employee who left the company two years ago still has active credentials for the firewall management console; those should be immediately deactivated. Additionally, remove or add any keycards to the physical server room or office where the firewall hardware resides.
Consider implementing the rule of least privilege for your firewall’s configuration. A least privilege access strategy mandates that access is only given to those who explicitly need it to perform their jobs properly. Least privilege access can apply to all enterprise systems, not just firewalls, for improved security. If you decide to implement this strategy, reduce employee system access to those who need it and adjust all other credentials or permissions accordingly.
11. Test New Configurations & Schedule the Next Audit
As soon as you’ve completed the initial firewall audit, prepare for the next one by testing the current configuration and scheduling a sequential audit. Don’t just assume that any new configurations work — your networking, IT, and security teams should be regularly testing the firewall rules and the hardware and software’s overall operations. The post-audit testing period is also an appropriate time to hire a pentesting service.
Planning the next audit in advance makes it more likely to happen on schedule. Additionally, give your team members assignments so they know exactly what roles they’ll have in the next audit, as well as a timeline for completing those steps.
Free Firewall Audit Checklist
Use the following list in order as a short-form set of steps that you can present to any business leader and use to guide your audit process.

By following this list or a similar one, your teams will be better prepared to plan and execute firewall audits in the future. You’ll also be able to add any extra steps that your team ran into during the audit process; that’s a normal occurrence during any audit process.
Top 3 Firewall Audit Providers
If you’re looking for a firewall auditing tool, consider Tufin, SolarWinds SEM, and AlgoSec as potential solutions. They’re three of the top firewall auditing products in the security market, and they offer features like compliance auditing, firewall rule compliance, and network scanning.
Tufin
Tufin is a firewall auditing tool that’s intended to help teams become and stay compliant with regulations like HIPAA, PCI-DSS, and GDPR. Tufin also generates audit reports that can be automated if needed. It sends alerts to security teams when one of their configurations doesn’t meet a specified organization security policy. Tufin offers three plans — SecureTrack+, SecureChange+, and Enterprise; contact its sales team for a custom quote.
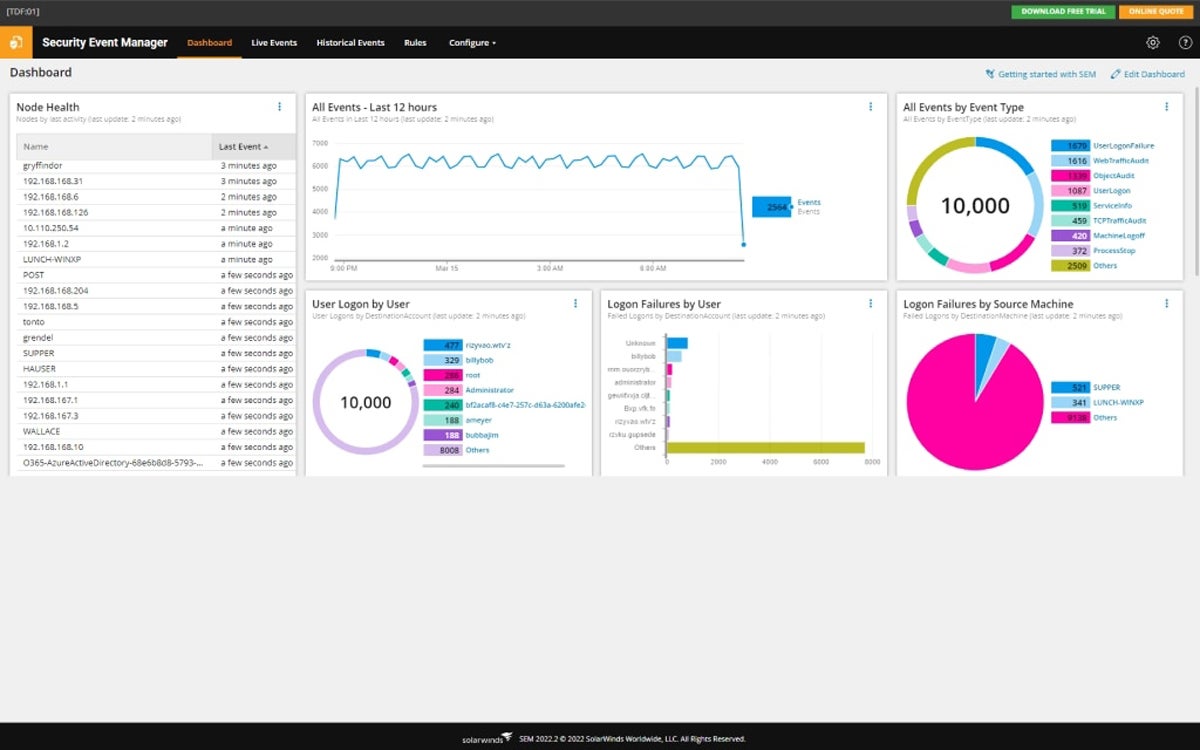
SolarWinds SEM
SolarWinds Security Event Manager (SEM) is a comprehensive tool for managing business cybersecurity. Teams can use SEM to develop audit reports, centralize log and event data from multiple network sources, and receive real-time alerts. A SolarWinds SEM subscription license starts at $2,992, and a perpetual license starts at $6,168, but for a custom quote based on your business’s specific environment, contact the sales team.
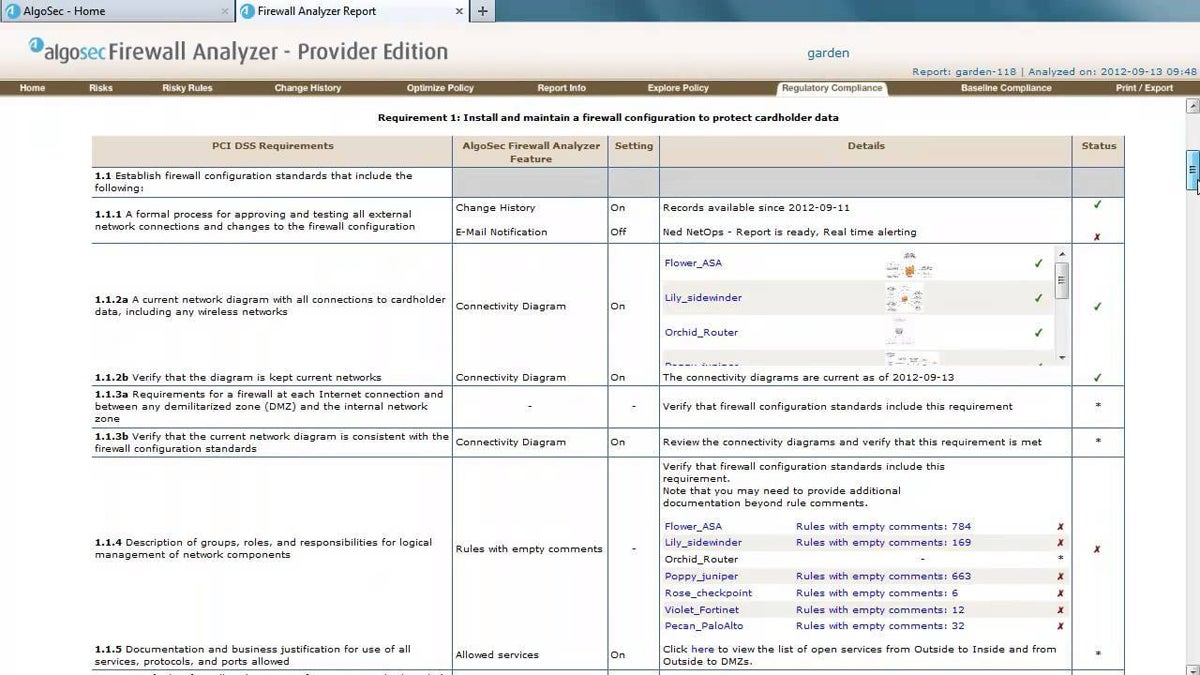
AlgoSec
AlgoSec is a firewall auditing and compliance tool that allows security teams to generate reports based on compliance standards like PCI, SOX, and HIPAA. AlgoSec checks all changes to firewall rules to make sure they’re consistent with industry compliance. It also documents the change approval process for rules. For custom pricing, contact AlgoSec’s sales team or request a quote; you can also buy through one of its partners.
Frequently Asked Questions (FAQs)
What Is Firewall Compliance?
Firewall compliance can refer to either organizational compliance, meaning the firewall meets your business’s security policies, or regulatory compliance, meaning it meets industry or government standards.
Many businesses will have to consider both. The way a firewall is configured, including its rules, should align with your organization’s security goals, since those goals are company-specific and most suited to your individual business needs (assuming they’re logical and well-developed).
What Is a Firewall Assessment?
A firewall assessment is a broad evaluation of your firewall’s hardware, like appliances, and its software, like the operating system that manages it. A thorough assessment should also cover any firewall rules and access controls. An assessment is similar to an audit, but the connotation of an audit is typically more thorough. However, they’ll involve some of the same steps.
What Do You Audit in Your Firewalls?
Audit all firewalls’ hardware, operating systems, other management software, rules, and any additional configurations. Every part of the firewall should be reviewed so your business knows if it works and if its rules are still serving the network and organization well.
Bottom Line: Perform Firewall Audits Consistently
Doing an initial audit is the biggest step, but your IT, networking, or security teams should schedule sequential audits over the coming years. Consistent audits save teams time in the long run because they know exactly where to find documentation and other configuration resources. By preparing sufficiently for an audit, creating thorough and clear documentation, and testing audit success afterwards, you’ll improve your IT infrastructure’s overall security.
To learn more about firewalls, read about the common types of firewalls next, including unified threat management products, database firewalls, and web application firewalls.




