Setting up a firewall is the first step in securing your network. A successful firewall setup and deployment requires careful design, implementation, and maintenance to effectively improve your network integrity and data security. Before performing a firewall configuration, consider factors such as security requirements, network architecture, and interoperability; avoid typical firewall setup errors; and follow the best practices below.
8 Considerations Before Setting Up a Firewall
Some factors to consider before you configure a firewall include creating detailed requirements and a proof of concept. Take note of your security requirements, physical environment, and component interoperability. Assess your network design, management protocols, and your future needs to ensure an effective protection without bottlenecks while also aligning with company goals and security standards for a secure network strategy.
Be sure you have the following before getting started:
- Clearly-defined requirements: Understand the organization’s requirements, such as the type of firewall, performance requirements, compliance requirements, and minimum specifications. Check if the chosen solution is consistent with the organization’s goals and infrastructure.
- Proof of concept: Execute a proof of concept or environment simulation once you identify the potential firewall products to select the best-fit solution for the organization’s specific requirements. Verify that the chosen firewall can meet your security standards and functions.
- Firewall architecture design and environment: Finalize your architecture, harden configurations, identify location and dependencies, and define policy rules. Evaluate the network firewalls’ physical placement, security, space, power, cooling, and network requirements.
- Security needs and capabilities: Determine which types of firewall, such as packet filtering, stateful inspection, or application firewalls, are most suited to their traffic requirements. Consider your other security measures like intrusion detection, VPNs, and content filtering.
- Component interoperability: Verify the compatibility with your current network infrastructure, including hardware and software. Evaluate the interoperability with your logging systems, as well as prospective network upgrades. Confirm that all components integrate seamlessly.
- Network requirements: Understand your network’s capacity, maximum simultaneous connections, latency requirements, and future traffic demands. Consider load balancing, failover mechanisms, and your preference for hardware-based or software-based firewalls.
- Management: Evaluate the firewall’s remote management protocols, adherence to organizational regulations, and remote management access limits. Utilize centralized management capabilities across numerous devices, as well as future scalability.
- Future Needs: Assess if the chosen firewall solution can meet your organization’s predicted demands, such as IPv6 migration, anticipated bandwidth requirements, and compliance with new regulations. Ensure that your firewall investment is effective and scalable over time.
8 Steps to Set Up a Firewall
To set up a firewall, configure the tool by creating rules, network zones, and policies. Activate logging and alerts, and perform extensive testing and auditing. Finally, deploy the firewall and perform regular monitoring and maintenance to provide an ideal security posture and effective network protection.
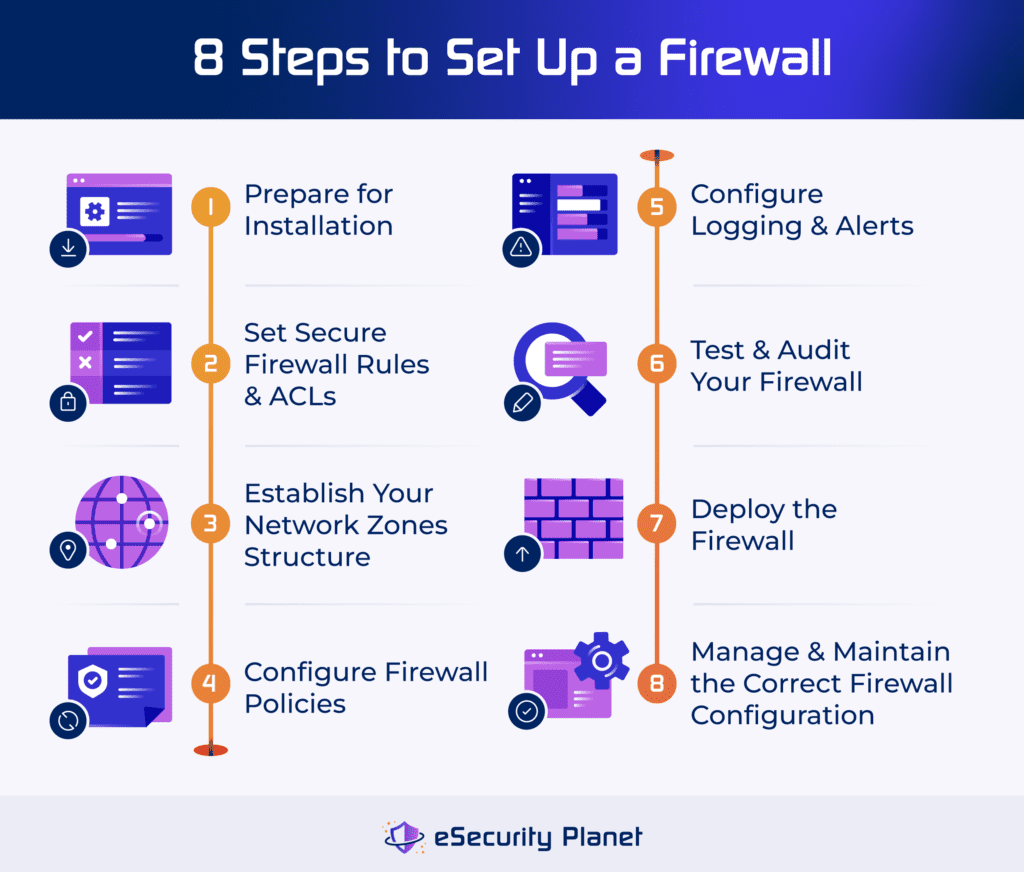
1. Prepare for Installation
The first stage in setting up a firewall is to prepare for installation after evaluating the type of firewall you need via the risk assessment listed above. Gather the necessary equipment, evaluate the network layout, and become familiar with the firewall documentation.
Physically install the firewall and ensure appropriate connections. Install hardware, operating systems, and software, apply fixes, and harden the firewall to reduce vulnerabilities. Only the administrator should have the authority to control the firewall, deactivate superfluous services, and secure the physical environment. Synchronize firewall clocks with other systems to improve log analysis.
2. Set Secure Firewall Rules & ACLs
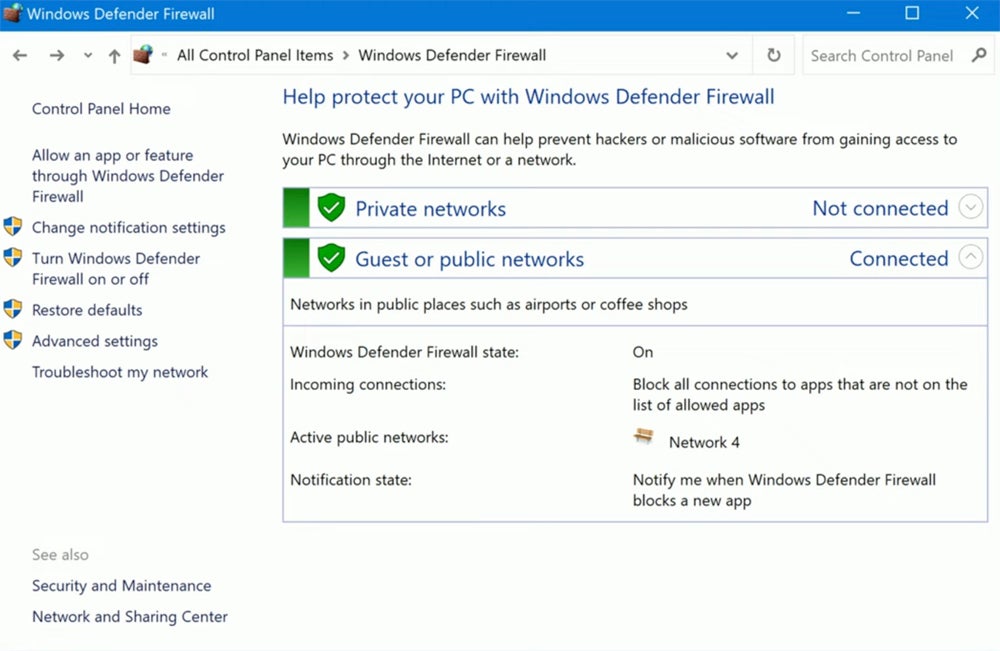
To prevent unwanted access and ensure effective traffic management, secure your firewall through updating firmware to resolve vulnerabilities and adopting proper configurations prior to installing firewalls in production. Disabling default accounts and changing passwords improve security, as does requiring strong passwords for administrator accounts.
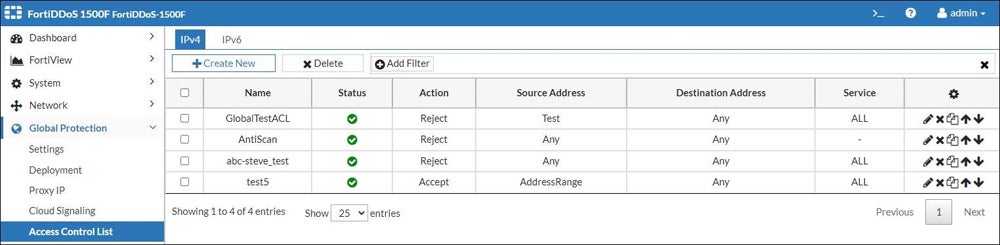
The Simple Network Management Protocol (SNMP) should be disabled or set securely. Firewall rules, defined by access control lists (ACLs), control traffic based on IP addresses, port numbers, and protocols. To maximize security, thoroughly test configurations, including advanced features such as web category filtering and intrusion prevention, prior to deployment.
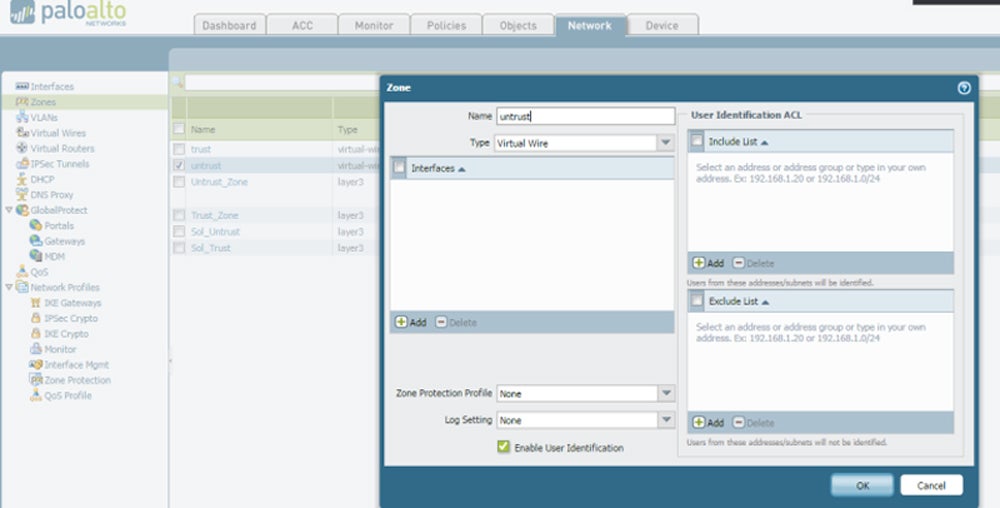
3. Establish Your Network Zones Structure
Establishing your network zone structure involves determining the sections of your network, known as network zones, that hold high-value assets and data and surrounding them with firewalls to regulate access and assure security. This technique complies with PCI-DSS rules and ensures strong security.
Carefully distribute resources to each zone, balancing security requirements with administrative complexity. Consider establishing a demilitarized zone for important servers to enable comprehensive traffic monitoring. Remember to create an IP address structure that efficiently connects firewall interfaces to their corresponding zones, hence improving network organization and security.
4. Configure Firewall Policies
Configuring policies is one of the most essential phases in effectively securing a network through firewalls. Firewall policies set network access conditions, including authorized ports, approved IP addresses, and security zones for network segmentation. Testing in a controlled environment confirms that the firewall performs as expected, blocking unwanted traffic based on ACL configurations.
Once tested, the firewall is ready for production, with a backup configuration safely preserved. Consider hiring a security specialist to check your configurations for maximum data protection. Tailor firewall capabilities such as network segmentation and application controls to specific network zones while sticking to formal policies to avoid implementation complications.
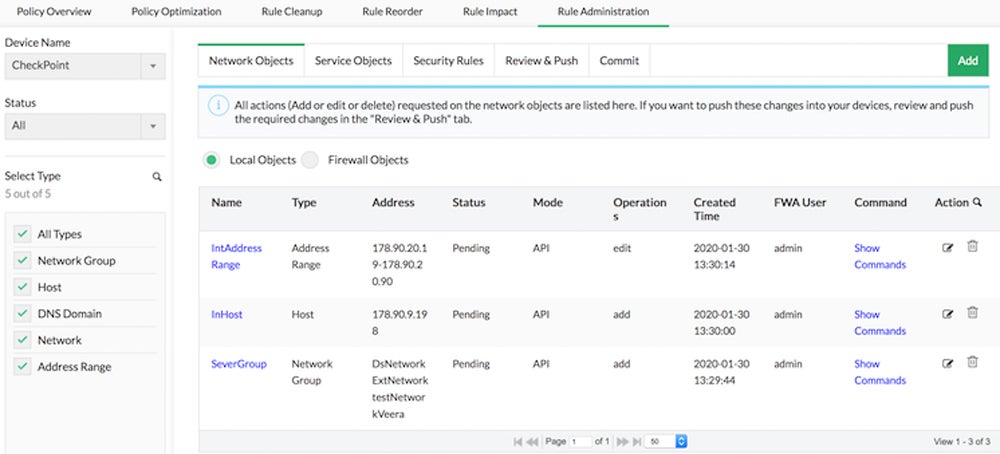
Need help in creating a firewall policy document? Check out our guide on firewall policy steps and download our free template.
5. Configure Logging & Alerts
Recording and monitoring firewall activity makes sure that security risks or operational concerns are detected in a timely manner. Logging captures critical information for failure prevention, recovery, and incident response. Determine what to log and how long to keep logs based on network requirements and resource limits.
Send logs to both local and centralized storage for complete monitoring. Create administrative accounts with read-only access to logs for auditing. Configure real-time notifications for critical events such as firewall rule updates or system status changes to provide a timely reaction to possible threats or operational difficulties. Customize logging and alert settings to meet your individual network needs and security priorities.
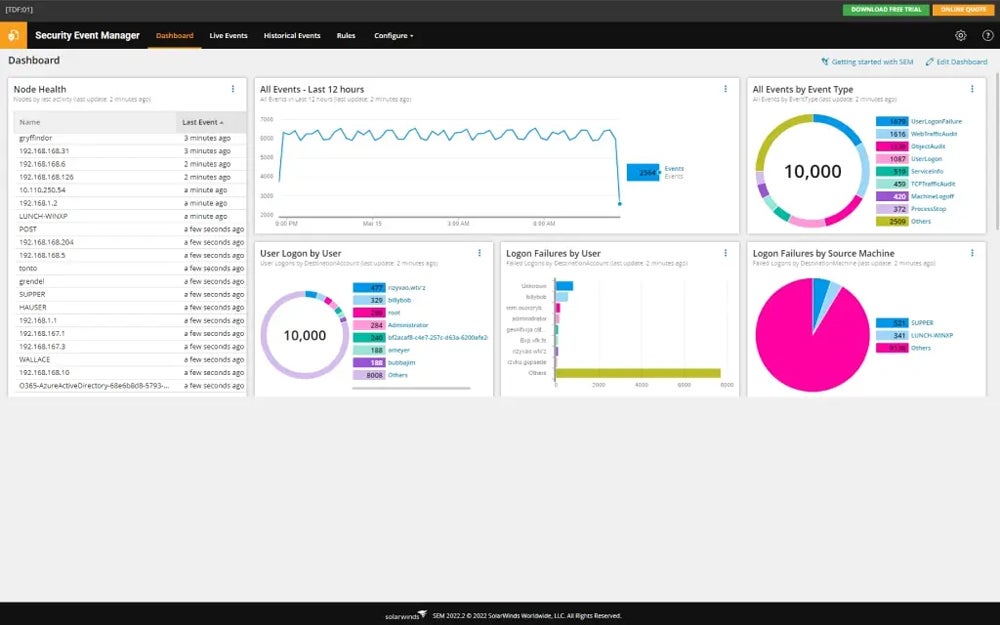
6. Test & Audit Your Firewall
Prior to deployment, conduct penetration testing and vulnerability scanning to find holes and improve defenses. Following deployment, plan regular audits to check firewall logs, verify ACLs and rules, and assure compliance. Changes should be documented and audit information stored for regulatory reporting purposes.
Implement procedures for updating firewall firmware and extensively testing additional features such as VPN and antimalware functionality. To accurately analyze firewall performance and effectiveness, ensure that the test network closely resembles production environments. Regular updates and thorough testing ensure a safe network environment.
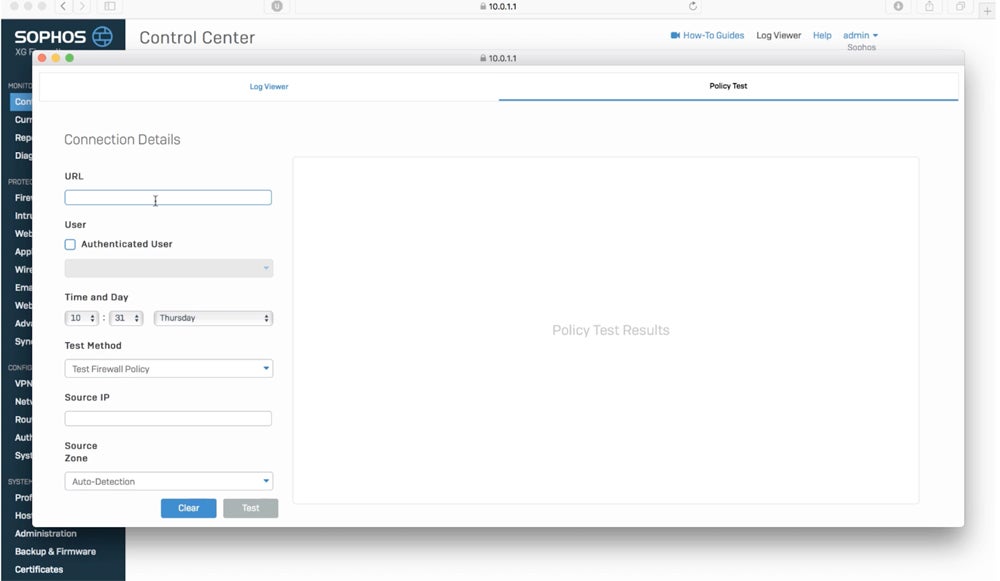
7. Deploy the Firewall
Deploying a firewall means transitioning from testing to actual operations while adhering to organizational regulations. Notify the users who were affected and coordinate any necessary equipment upgrades. Integrate the firewall’s security policy with the entire organizational policy and manage configuration changes as they occur. Consider a staged rollout or pilot program to fix difficulties before full implementation.
Integrating the firewall into the network entails more than just insertion; it also needs routing integration and possible switch reconfiguration. If you use failover mechanisms, set up network switches accordingly. Careful design and coordination guarantee that the firewall integrates seamlessly and operates effectively within the network infrastructure.
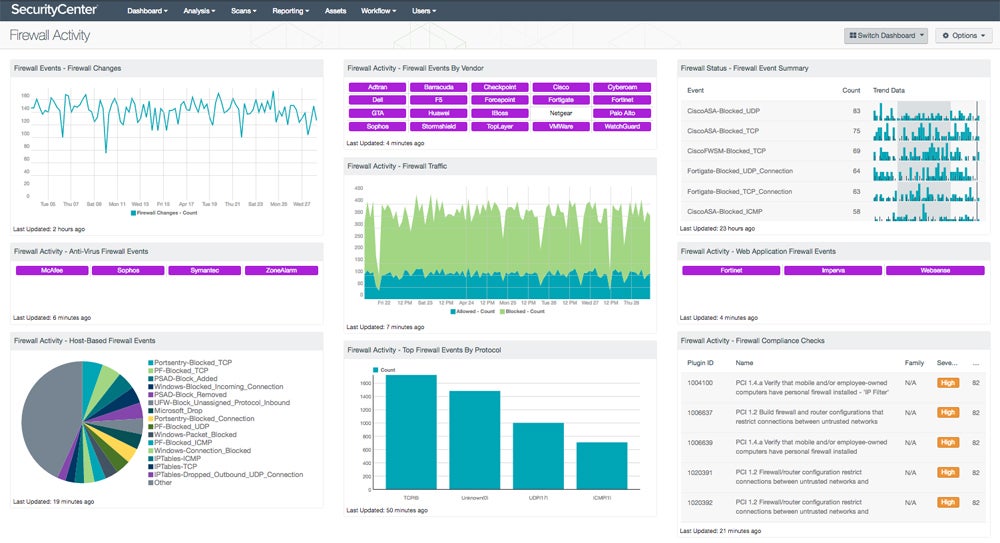
Integrate your firewall with network monitoring tools for more efficient tracking of your network’s performance and security.
8. Manage & Maintain the Correct Firewall Configuration
Firewall configuration management and maintenance imply continual efforts to ensure maximum functionality and security. This includes testing and deploying patches, updating policy rules to accommodate new threats or changes in network requirements, and monitoring performance to identify possible resource issues. Continuously monitor logs and alerts to detect and respond to threats effectively.
Periodic testing validates firewall rules, and regular backups of policies and rule sets protect against data loss. Formal configuration management methods should govern ruleset modifications, with admin access limitations and detailed documentation for accountability. Every six months, perform firmware updates, vulnerability checks, and configuration reviews to make sure the firewall remains efficient and effectively protects the network.
6 Common Mistakes to Avoid When Setting Up a Firewall
Misconfigured firewalls pose serious risks, allowing attackers easy access and endangering organizational security. Common failures involve providing unrestricted outbound traffic, forgetting to detect internal threats, updating rules inconsistently, establishing overly broad policies, testing using production data, and failing to log appropriately. These flaws expose networks to vulnerabilities and breaches, weakening security protections.
Allowing Unrestricted Outbound Traffic
A typical mistake is configuring the firewall to enable unrestricted outbound traffic. While focusing on inbound threats, failing to monitor outgoing traffic allows malware or attackers to exfiltrate data, potentially leading to costly breaches. Controlling outgoing traffic prevents unauthorized data leaks and maintains network security.
Neglecting Internal Threats
Focusing primarily on external threats exposes networks to inside attacks, including compromised internal hosts. Internal firewalls and access restrictions should be built to reduce risks from insider attacks or externally compromised systems, ensuring complete network protection.
Performing Inconsistent Firewall Rule Updates
Adopting a “set it and forget it” approach to firewall rules results in obsolete setups that don’t meet current network requirements or security policies. Regularly monitor and update firewall rules to account for changes in network architecture, user access, and regulatory compliance, ensuring an effective security posture and minimizing vulnerabilities.
Creating Overly Broad Policy Configurations
Configuring firewalls with too permissive policies, which allow traffic from any source to any destination, broadens the attack surface and exposes the network to unnecessary risk. Minimize the potential for breaches by adhering to the concept of least privilege and ensuring that the firewall regulations restrict access to just necessary services and resources.
Testing Systems with Production Data
Using production data in test settings jeopardizes security and breaches governance guidelines. Test systems shouldn’t connect to production systems or collect critical data to avoid being exposed to low-security situations. Enforcing rigorous access controls to test data assures regulatory compliance while also maintaining data integrity.
Failing to Conduct Proper Logging & Monitoring
Failure to evaluate firewall log outputs or configure monitoring systems with adequate granularity reduces threat detection and incident response capabilities. Proper logging architecture and analysis quickly detect and investigate security occurrences, enabling proactive defense actions and lowering the risk of breaches.
10 Best Practices for Setting Up a Firewall
Any errors in the configuration of your systems may increase your vulnerability to security breaches. From ensuring compliance to creating multiple layers of security, adopt the best practices below to limit these risks and avoid typical errors while configuring a firewall.
Select the Correct Firewall Type
Choose the firewall type that best meets your network’s needs. Available options include packet-filtering firewalls, stateful inspection firewalls, and sophisticated proxies with intrusion detection and prevention. For example, for a small office network, a stateful inspection firewall with minimal traffic filtering features may suffice, providing protection without being overly complex.
Utilize Compatible Security Tools
Use logging tools and run frequent audits to evaluate firewall performance. Employ penetration and vulnerability testing to assess network security. When choosing a firewall, consider a solution that strikes a balance between critical features and performance considerations, avoiding needless complexity that may reduce network efficiency. Look for compatible network security tools, such as endpoint protection platforms or threat intelligence platforms.
Streamline Processes via Automation
Automation tools make firewall configuration easier, reducing manual labor and lowering the risk of misconfiguration. Automation scripts and orchestration systems, for example, improve efficiency and provide a consistent security posture by streamlining rule management and policy enforcement across varied network environments. There are also solutions available that automate rule management, policy analysis, and compliance auditing.
Establish a Centralized Logging & Monitoring System
Centralized logging and monitoring systems collect vital information about potential threats and security breaches. Implementing a centralized logging system enables the efficient gathering, analysis, and visualization of firewall data across the network. A centralized system provides rapid detection of security issues, effective incident response, and proactive security actions to protect the network from potential threats.
Consider the Cloud Traffic
When establishing firewalls, prioritize solutions that can handle cloud-based apps and remote users. Implement policies and procedures that go beyond the traditional on-premise approaches. Failure to update firewall configurations to enable cloud traffic not only reduces productivity but also exposes enterprises to increased dangers, emphasizing the importance of a hybrid security approach that includes cloud-native defenses.
Prevent False Positives when Blocking Traffic
Fine-tune firewall policies to prevent excessively strict rules or requirements. Implement bespoke setups and whitelists to allow legitimate communications while limiting dangerous risks. Expect some initial issues and complaints as users adjust, but refine arrangements based on traffic patterns to guarantee effective security without compromising productivity.
Ensure Compliance
Firewall protection is pivotal for compliance adherence like PCI-DSS and HIPAA. Implement strong firewalls around sensitive data and ensure configuration changes meet regulatory standards. For example, adhere to logging compliance, especially under PCI-DSS, by enabling automated logging and verifying audit accuracy for comprehensive data recording.
Document the Firewall’s Capabilities
Record the firewall’s capabilities for optimal planning and deployment. For example, if a firewall lacks advanced intrusion detection capabilities, your company may need to enhance its security plan. Each firewall model has distinct characteristics and limits that influence security policies and deployment methods. Include these details in the planning document so that the firewall’s capabilities match the organization’s security objectives and requirements.
Create a Defense-in-Depth
Defense-in-depth is a security technique that involves establishing multiple layers of defense to protect against diverse threats. For example, a business may install a next-gen firewall at several network points, supplemented with antivirus software and intrusion detection systems. This strategy ensures that if one security layer fails, others are in place to reduce the risk and prevent a successful attack.
Conduct Regular Updates
Establish a consistent timetable for firewall assessments and updates to maintain continuing security while avoiding crucial activities during busy IT operations. Regular updates are required for firewall maintenance. To avoid illegal access, access controls should be reviewed and adjusted on a regular basis. Keep up with vendor-provided firmware, software patches, and security upgrades to resolve vulnerabilities and improve protection.
Bottom Line: Set Up a Firewall to Boost Your Network Security
A firewall efficiently strengthens defenses against cyberthreats while preserving data integrity and network operation. Make sure you have a specific setup for each network, taking into account its unique requirements. A comprehensive firewall audit identifies particular requirements and assesses your current structure. Additionally, regular maintenance guarantees an optimized firewall configuration, resulting in effective security measures that last over time.
To gain insights into your company’s specific firewall needs and assess its current status, explore our guide on performing a comprehensive firewall audit.




