Incident response frameworks and practices are detailed action plans to resolve security breaches inside a business or organization. They give the business a thorough and proactive approach to security by methodically recording every aspect of an incident, including how it happened and the measures that were taken, and describing the subsequent steps to prevent such incidents in the future.
The National Institute of Standards and Technology (NIST) and the SANS Institute have developed well-known and respected incident response frameworks that have created standardized practices for developing and putting into practice efficient incident response processes.
Choosing an Incident Response Framework
NIST and SANS both provide incident response frameworks to help businesses build strong capabilities. A thorough and systematic strategy, the Computer Security Incident Handling Guide (NIST SP 800-61) by NIST focuses on six phases: preparation, detection and analysis, containment, eradication and recovery, post-incident activities, and lessons learned. The SANS Incident Handler’s Handbook, on the other hand, takes a more tactical and procedural approach, emphasizing the important steps to follow at various phases of an event.
NIST
- Preparation
- Detection and analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
SANS
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned
The NIST framework includes interaction with external organizations, policy formulation, and planning as part of its coverage of a wider variety of incident response operations. It offers instructions for assembling an emergency response team, specifying duties, and setting up communication lines. SANS, in contrast, focuses mostly on technical elements of incident response, such as identification, containment, and eradication.
While reflecting real-world insights and new trends, the SANS framework benefits from the combined expertise and experience of the SANS community. The NIST framework, created in collaboration with professionals in the field, is more concentrated on offering uniform guidance that may be applied in a variety of industries. Both frameworks provide insightful advice for developing incident response capabilities, and businesses may mix components from each to develop a tailored strategy that meets their unique needs.
The specifics of incident response might change based on elements like your company’s specialties, the type of event at hand, and the regulations that are relevant to your sector. Organizations continually hone their methods for successful crisis response through this dynamic and iterative process.
This entails completing frequent testing exercises, giving staff members thorough training, and making a proactive investment in the creation of new response capabilities. Businesses may keep ahead of new risks by adopting a proactive and adaptable strategy and ensuring that their incident response procedures are durable and efficient over time.
Also read:
7 Steps to the Incident Response Process
A well-defined incident response strategy can help your firm proactively monitor security occurrences, assess the efficacy of your current policies, and spot areas that need further improvement. Here are six steps to consider implementing into your organizational architecture so you can create a strong incident response capacity.
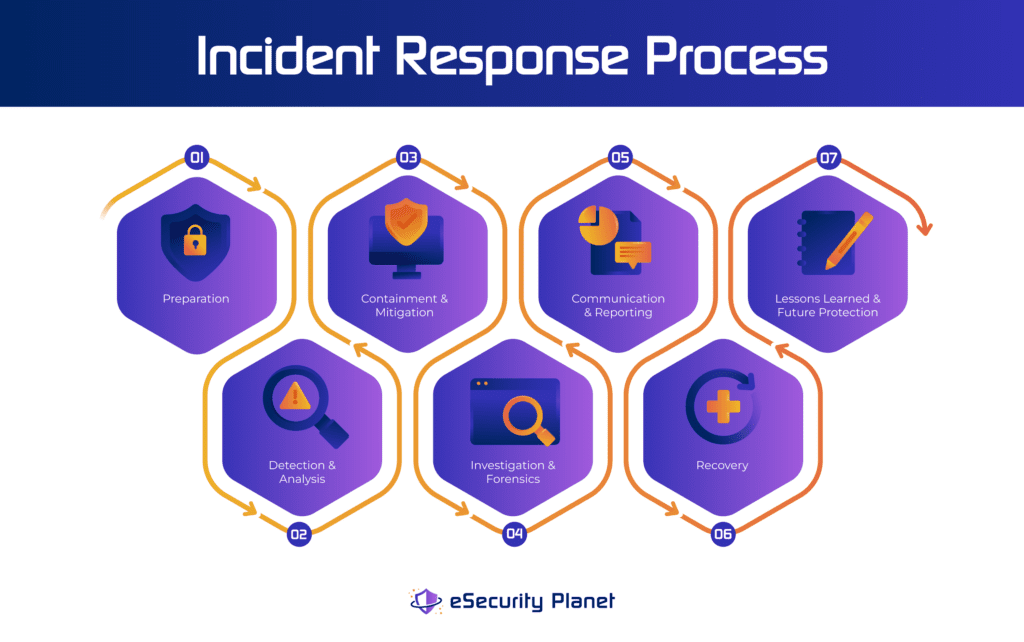
1. Preparation
Preparation involves developing the processes, procedures, and resources required for efficient event response. Creating an incident response plan, defining roles and duties, identifying important employees, and creating communication routes are all part of it.
2. Detection and Analysis
Next, identify a security event through intrusion detection systems, log monitoring, network monitoring, or user reporting. When an event is discovered, the incident response team should investigate it and identify the nature and severity of the issue.
3. Containment and Mitigation
Once the incident has been confirmed, the emphasis changes to confining the issue to avoid future harm or unwanted access. This entails isolating and stopping impacted systems or taking other appropriate measures to limit the impact. You can implement certain mitigation strategies to minimize the immediate potential harm caused by the incident.
4. Investigation and Forensics
Conduct a full investigation to determine the cause, scope, and extent of the occurrence. This includes gathering evidence, doing forensic analysis, analyzing logs, and determining the access point and vulnerabilities exploited. The purpose is to collect data that will help prevent such situations in the future.
5. Communication and Reporting
Effective communication is critical throughout the incident response process. Management, IT teams, legal counsel, and, if required, law enforcement authorities should all receive regular information. Write a clear and simple report detailing the occurrence, actions done, and lessons gained.
6. Recovery
After the event has been controlled and investigated, focus your attention on restoring regular operations. Remove any suspicious or malicious presence, rebuild or restore affected systems, and validate their integrity. The incident response team along with IT staff is responsible for implementing necessary security patches, updates, or changes to prevent similar or identical incidents from occurring.
7. Lessons Learned and Future Protection
The final step entails reviewing the occurrence and drawing useful conclusions to enhance security procedures. Organizations may put proactive steps in place to strengthen their defenses, improve incident response skills, and defend against similar occurrences in the future by identifying vulnerabilities, flaws, and gaps in the current systems and networks.
Building Your Own Incident Response Plan
Making the effort to create your incident response plan empowers your organization’s security and resilience. By tailoring the plan to meet your particular needs, you will have the flexibility to actively defend your business and its valuable assets from threats. It is important to leverage industry best practices, frameworks, and guidelines provided by organizations like NIST and SANS to ensure that your incident response plan is standardized and at the same time suits your business needs.
Also read: What is Incident Response? Ultimate Guide + Templates
Bottom Line: Incident Response Process & Frameworks
Incident response processes and frameworks are essential for efficiently resolving cybersecurity breaches and preventing future threats or attacks. By following standardized guidelines and leveraging resources from well respected organizations such as NIST and SANS, you can create an incident response process tailored to your business’s needs.
Implementing a well-defined incident response strategy — including steps like preparation, detection and analysis, containment and mitigation, investigation and forensics, communication and reporting, recovery, lessons learned, and future protection — empowers organizations to proactively safeguard their assets and strengthen their defenses against potential threats.
Also read:




