Patch management is the continuous process of releasing and deploying software updates, most commonly done to solve security and functionality issues. But to do patch management right, you need a detailed, repeatable process.
Establishing an efficient patch management process is critical for keeping your systems secure and stable. Patches address vulnerabilities that could be exploited by hackers; bug fixes that correct faults or defects in the software, and feature upgrades that offer enhancements to improve the user experience. Installing these patches and updates keeps your software and firmware secure, reliable, and up to date with the latest improvements.
This step-by-step guide to the patch management process can help you stay ahead of vulnerabilities and reduce cyber risk.
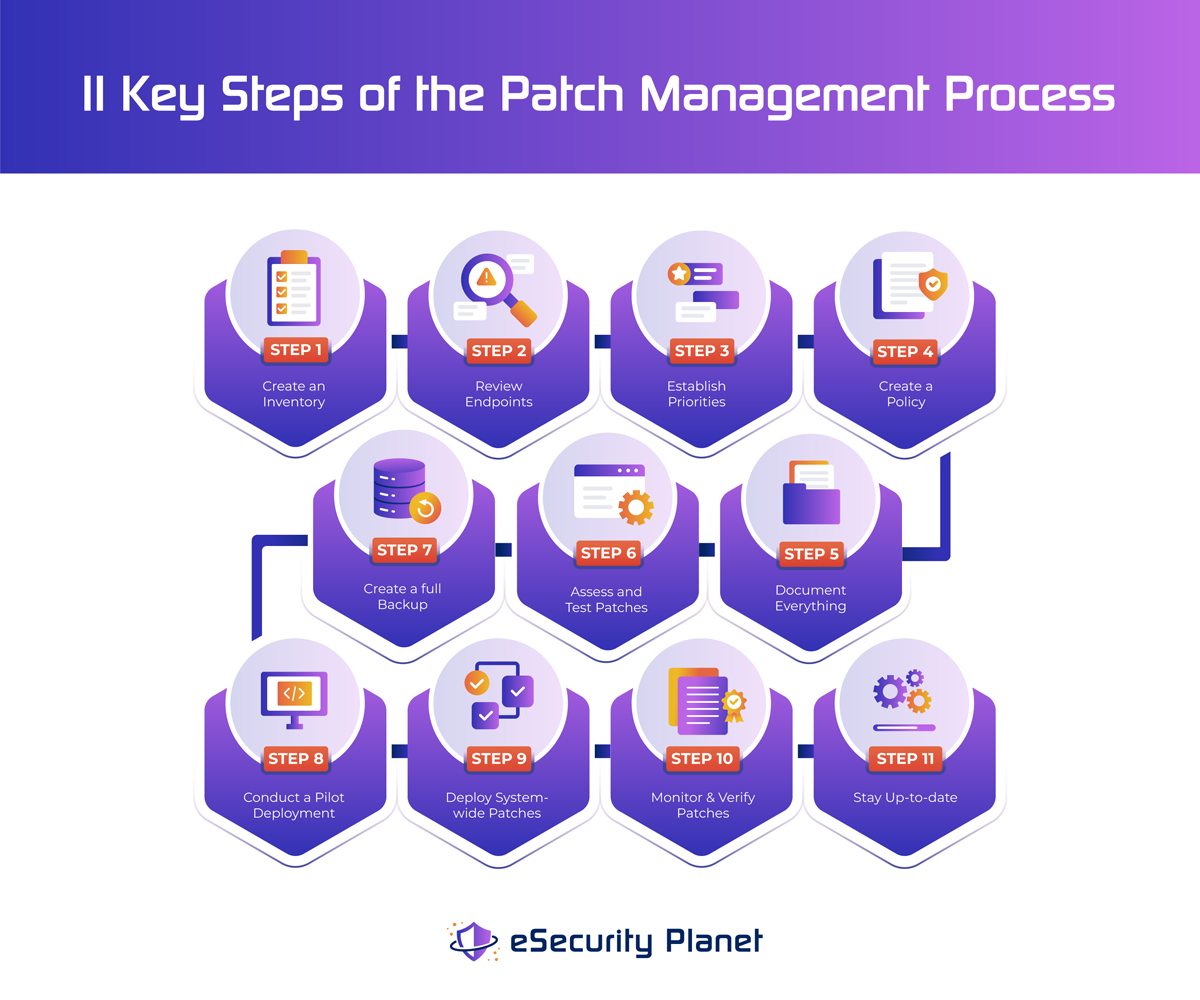
- Step 1: Create an inventory
- Step 2: Review endpoints that need patching
- Step 3: Establish priorities
- Step 4: Create a patch management policy
- Step 5: Document everything
- Step 6: Assess and test patches
- Step 7: Create a full backup
- Step 8: Conduct a pilot deployment
- Step 9: Deploy system-wide patches
- Step 10: Monitor & verify patches
- Step 11: Stay up-to-date
- Goals of the patch management process
- Bottom line: the patch management process
Also read: Patch Management Policy: Steps, Benefits and a Free Template
Step 1: Create an inventory of all software applications and systems
The first step in patch management is to develop an inventory of all software programs and systems in the organization. This inventory gives a comprehensive knowledge of your environment’s extent and complexity, ensuring that no software or system is ignored throughout the patching process. A thorough inventory is the first step in determining which fixes have been implemented and which may be missing. Knowing the current condition of patching will aid in developing a plan.
One challenge for organizations is they often don’t know everything that’s connected to their networks. IT asset management tools can be an effective way to help teams identify all the assets they need to monitor.
See the Top IT Asset Management (ITAM) Tools for Security
Step 2: Review the endpoints that need patching
Conduct an extensive inspection of all endpoints in your company that require patching. Servers, workstations, laptops, and any other device that runs software programs are included, as is the software, firmware and applications that run on them. Using the inventory produced previously, identify the exact endpoints that require patching to guarantee complete coverage, identify susceptible systems, prioritize patching, eliminate oversights, and ensure compliance with security rules. Organizations may successfully monitor and mitigate vulnerabilities by completing a thorough evaluation, lowering the risk of possible security breaches and ensuring a safe IT environment.
Step 3: Establish priorities based on risk and criticality
Once you have identified your software applications and systems, prioritize each depending on its importance and position in a potential attack path. Evaluate the impact of vulnerabilities on each system and prioritize patching efforts accordingly. This process guarantees that high-risk vulnerabilities and essential systems are given the attention they require.
The importance of the asset is every bit as important as the severity of the vulnerability. A vulnerability with a lower CVE score in a customer database might become more urgent when the value of the asset is considered.
Step 4: Create a patch management policy
Creating a patch management policy is essential to establishing a consistent and uniform patching procedure. A Patch management policy codifies the core IT need for all systems and software to be patched and updated in order of importance. It also outlines clear processes that can be followed and reported on, predetermined standards that can be tested and validated, and rules describing the requirements for patching and upgrades. Your organization’s patch management techniques, guidelines and roles and responsibilities should be outlined in the policy.
Also read: Patch Management Policy: Steps, Benefits and a Free Template
Step 5: Create documentation before and after patching
Keep detailed documentation throughout the patch management process. Document the condition of systems prior to patching, including versions, settings, and vulnerabilities. Document the modifications made after patching, including the patches deployed and their impact on the systems. This is critical for keeping track of system states, patches deployed, and their impact. It facilitates troubleshooting, compliance, auditing, and reporting. Organizations can improve their capacity to assess patch efficacy, solve issues, and certify compliance with security requirements by thoroughly documenting the patch management process.
Step 6: Assess and test patches
Patches must be assessed and tested before being deployed into the production system to ensure the efficient operation of your systems and applications. Evaluate the effects of the patches on your systems and applications in a controlled test environment. This procedure facilitates the detection of any potential conflicts, incompatibilities, or harmful effects that patching may have. Thorough testing reduces the risk of interrupting the production environment. By conducting comprehensive evaluations, uncovering conflicts or compatibility problems, and eliminating risks, you may prevent disruptions, keep systems reliable, and safeguard the integrity of your IT infrastructure.
Step 7: Create a full backup
Make a complete backup of key systems and data before applying fixes. This backup acts as a safety net in the event that any problems develop during the patching procedure. In the case of a malfunction, you can use the backup to restore the systems to their former condition.
Performing a complete backup prior to patch distribution is an important preventive practice. It reduces risks, facilitates system recovery, safeguards data, gives rollback possibilities, and instills trust. Organizations may provide a safer and easier patching experience by adding this phase into the patch management process, lowering the potential impact of any difficulties that may develop.
Many patch management tools include rollback features.
Step 8: Conduct a pilot patch deployment
To reduce the potential of widespread problems, it is best to test patches on a limited scale before rolling them out to the entire business. Apply the patches to a representative sample of systems. Keep an eye on the outcome and resolve any problems that may occur. This stage assists in identifying possible issues and refining the deployment procedure. A proactive strategy to minimizing risks and refining the deployment process is to conduct a trial deployment of representative patches before distributing them organization-wide. It helps identify possible issues, ensuring compatibility, and increasing trust in the effectiveness of the updates.
Step 9: Deploy system-wide patches
It’s now time to deploy the test patches throughout the organization to the right endpoints. Following the assessment, testing, and validation of the patches, the next step is to download them from the right source and deploy them based on the defined priorities and within the timeframe specified for patch distribution. This is another place where patch management tools will help.
To ensure the integrity of the IT environment, it is critical to take caution throughout this stage, continuously monitoring the deployment process and correcting any issues as often and quickly as possible.
Step 10: Monitor patch updates and fix any issues
For the patch management process to remain effective, verifying and monitoring patch updates is essential. It enables companies to check that patches were successfully installed, guarantee system operation, assess policy compliance, find new patches that need applying, and keep a consistent patching schedule. After fixes have been installed, monitoring and assessment of the patching procedure will measure its success. It is crucial to confirm that patches have been deployed properly, systems are operating as intended, and the organization’s patch management standards are being followed.
Organizations can use patch management solutions that automate and streamline the process to efficiently monitor patch updates. These solutions enable IT organizations to track which patches have been installed and spot any possible problems or gaps by providing visibility into the patching status of various systems.
System management and monitoring tools can help track the patching process and ensure the integrity of the patches that are delivered. Investigate and fix any patch failures or issues as soon as possible. Determine the fundamental reason for the failure and devise a solution. To remedy the issue and protect the security of your systems, you may need to retest, debug, or install alternative patches. When vulnerabilities can’t be fixed or completely mitigated by a patch, security controls can improve the protection of the affected asset. This process is often referred to as virtual patching.
Step 11: Stay up-to-date with the latest patches
Stay informed about the most vulnerabilities and patches for your systems and devices, and be sure to update your patch management software to keep that current too. Keeping up with the latest vulnerabilities and updates ensures that your systems have the best possible security safeguards in place to fight against known vulnerabilities.
These changes can also improve the operation and stability of your systems. Updating your software maintains compatibility with new technologies and reduces the possibility of software conflicts or performance problems. Review patch management resources, security bulletins, and vulnerability databases on a regular basis to ensure you are aware of any new fixes that are relevant to your systems. Again, this is another area patch management and vulnerability management tools can help by identifying issues for you.
This step allows you to maintain a proactive approach to patch management and respond quickly to emerging risks. By remaining up to date on the latest vulnerabilities and patches, you can address newly identified vulnerabilities and security risks quickly, while also meeting compliance requirements and adhering to industry standards.
Also read: Patch Management vs Vulnerability Management: What’s the Difference?
Goals of the Patch Management Process
Organizations may build a strong and proactive strategy for patching by aligning their patch management efforts with these goals, which will help assure the security, stability, and optimal performance of their software applications and systems.
- To create predictability and patching routine. Creating an organized approach to patch management begins with establishing regular patching schedules, following policies and procedures, and preserving documentation. Because patching operations are predictable, businesses can anticipate and plan for them, ensuring that they are carried out effectively and consistently.
- To allow the IT team to address urgent vulnerabilities. When required, patch management protocols should grant the IT team emergency capabilities. This not only includes security emergencies, but also includes the ability to make rollbacks in the event that a patch produces unexpected problems or interruptions.
- To enhance overall system security, integrity, and reliability. An effective patch management process increases the system’s security, integrity, and reliability. It ensures that systems are trustworthy, perform optimally, and are less prone to attacks or malfunctions. By keeping software programs and systems up to date with the most recent upgrades, organizations may improve their overall security posture, preserve sensitive data, and maintain the trust of customers and stakeholders.
- To ensure compatibility between applications and systems. Patch management ensures that software programs and systems are compatible with the organization’s IT infrastructure. Updates and patches are often done to solve compatibility issues that may develop as program versions or dependencies change. Organizations may maintain an adaptable and cohesive IT infrastructure by installing these updates, reducing any future conflicts or problems.
- To have complete visibility into patch status. Having complete insight into the status of patches across the company is a key objective of patch management. This entails being aware of the systems that have been patched, the ones that still need to be, as well as any problems or exceptions that may have arisen. Visibility enables businesses to monitor compliance, spot gaps, and take the necessary steps to keep all systems current.
- To improve system stability and performance. By fixing software errors and problems, patches play a critical role in increasing system stability and performance. Applications and systems may experience unexpected behavior, crashes, or performance problems as a result of bugs. Organizations may correct these problems and guarantee that software performs as intended by applying bug fixes via patches, creating a more dependable and stable computer environment.
- To protect systems from potential threats. Fixing security flaws in software programs and systems is one of the main goals of patch management. Organizations may address security gaps and shield their systems from possible dangers like unauthorized access, data breaches, or malware assaults by swiftly implementing updates. Maintaining the integrity and confidentiality of sensitive information requires minimizing security risks.
- To reduce downtime and disruptions caused by software issues. Organizations may minimize downtime and lower the likelihood of security risks by practicing proactive patch management. Unaddressed software bugs or vulnerabilities can cause system crashes or unplanned downtime. Promptly implementing updates, maintaining business continuity and reducing productivity losses minimizes potential software-related interruptions. Systematic patching lessens the need for costly rollbacks or system restorations by preventing key issues from developing. This leads to more efficient operations and lessens negative experience for end-users or consumers.
Bottom Line: Patch Management Process
The patch management process is critical to maintaining an efficient, secure and reliable IT environment. By following these 11 key steps of the patch management process, organizations may efficiently manage patches, reduce vulnerabilities, and secure their systems from potential cyber threats. Patch management processes must be proactive and organized in order to effectively protect the integrity and security of your software applications and systems.
Read more: Patch Management Best Practices & Steps




