A virtual local area network (VLAN) is a virtualized segment that’s created on a physical network to separate and group devices into more logical environments. This separation helps to control traffic, optimize network performance, and even improve security by isolating sensitive workloads and data.
However, as useful as VLANs can be for improving network performance and management, they can also get convoluted and overly complex for enterprise network managers who are juggling multiple VLANs and specs at once. That’s where VLAN tagging — the practice of adding metadata labels, known as VLAN IDs, to information packets on the network — can help. These informative tags help classify different types of information packets across the network, making it clear which VLAN each packet belongs to and how they should operate accordingly.
In this guide, we’ll explore what VLAN tagging is, how it works, and why and how you may want to implement the strategy in your own network virtualization projects.
Also read: VLANs: Effective Network Segmentation for Security
Network Components and Protocols Used in VLAN Tagging
VLAN tagging is a complicated topic, so we’ll start with a discussion of the network components and protocols used in VLAN tagging and the roles they play before we get into specifics and best practices.
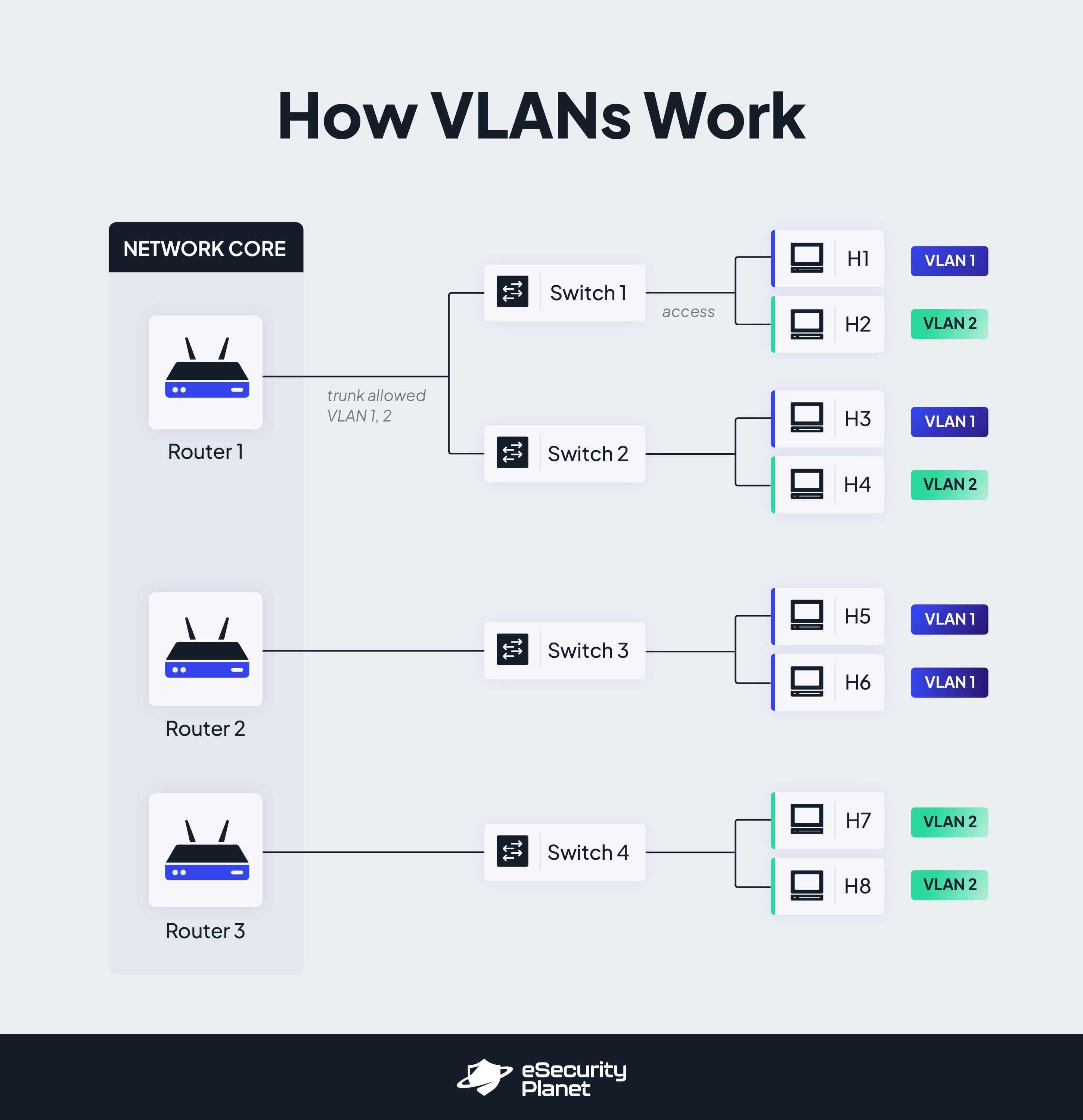
- Switches: A network switch connects other devices within a VLAN. In VLAN tagging, switches are responsible for VLAN tag assignment, VLAN trunking, VLAN routing, and other VLAN management tasks that involve directing and labeling network traffic.
- Broadcast Domain: In a traditional network, the broadcast domain includes any devices and other components in that network; because they’re all in the same flat network, they can all receive a message when it’s broadcast. Broadcast domains are made smaller and more function-specific with the help of VLANs and VLAN tagging, a process that segments domains so devices can only receive messages and packets from other devices on the same VLAN segment.
- Router: A network-layer router makes it possible to route data packets across different VLAN. While switches focus on inter-device connections, routers are most useful for inter-switch connections and larger network operations.
- User Authentication: In addition to checking VLAN IDs to ensure they match and are approved for that particular VLAN, many other user authentication methods are typically used to ensure devices and users are approved for that VLAN. A remote authentication dial-in user service (RADIUS) server or other authentication server is typically used to authenticate and authorize user traffic.
- Trunk: The trunk port forwards and facilitates VLAN-to-VLAN communication across multiple VLANs. It operates at the layer two protocol level and is able to manage the transmission of tagged VLAN traffic via switches and routers.
- Layer Two Protocol: Also known as the data link layer, this type of networking protocol is where switches, wireless access points, frames, and other devices are able to exchange information packets within a single VLAN.
- Layer Three Protocol: Also known as the network layer, layer three routing is a more complex layer on top of layer two that makes it possible for information packets to travel to and from devices in separate VLAN segments. Routers operate at level three.
- Single Tagging: This is the ideal approach for VLAN tagging, wherein each VLAN and information packet receives a single type of tag. Single tagging makes it much easier to identify where data packets belong, where they can travel, and with what other devices they can interact.
- Dual/Double Tagging: This is when an information packet erroneously receives two or more VLAN tags. It occurs when a single packet travels through a network and goes through multiple tagging projects. This most often happens when a packet moves to a new VLAN from its previous VLAN but never sheds the tags and naming structure from that previous VLAN.
- Mixed Tagging: Mixed tagging happens when, in a single VLAN or group of VLANs, several different tagging standards are used, whether it’s done unintentionally or purposely because different devices support only certain tagging standards. Mixing tags in a VLAN environment can cause compatibility issues between devices and make it difficult for network administrators to monitor VLAN performance from a single dashboard view.
How VLAN Tagging Works
To begin the VLAN tagging process, you must first virtualize your physical network and set up different VLANs. These VLANs can be grouped however you see fit — some users create VLANs based on device location while others create VLANs based on department, traffic volume, or some other categorical classification. Regardless of how you decide to classify and group your VLANs, you can set them up through systems like wireless access point management systems.
Once your VLANs have been set up, it’s time to designate a specific VLAN ID to each VLAN; VLAN IDs are typically 12-bit values. From there, VLAN IDs are applied to the headers of different information packets that move through the network. Existing information packets can be manually given the VLAN ID that makes the most sense.
As new users and devices attempt to log into the network, an authentication server and/or other authentication tools will first be used to determine if that new host is valid. Once the user or device has been authenticated, a VLAN switch adds a logical VLAN ID to any information packets that item sends on the network. This VLAN ID ensures that the information packet stays within the appropriate VLAN and is only broadcast to that segment of the broadcast domain.
For more complex packet movement, trunks and/or routers may be set up to facilitate inter-VLAN movement. Otherwise — unless an error like dual tagging occurs — that packet is labeled and set up to stay among the hosts, ports, and switches that are present on its particular VLAN.
For an example of VLANs used for network security segmentation purposes, see Building a Ransomware Resilient Architecture.
Is VLAN Tagging Necessary?
VLAN tagging is a useful process, especially for larger networking environments that require admins to juggle different department classifications and expectations, device and user types, traffic types, permissions, and other factors simultaneously. It also helps network administrators for networks of all sizes to get more organized, understand the traffic they have flowing through their network, and segment the network in a logical way that improves performance and traffic flow.
However, VLAN tagging is not necessary for everyone; its usefulness depends on your network size, the number of VLANs you’re operating, and other organizational requirements. In fact, if you don’t know what you’re doing when you first set up VLAN tags, especially if you fail to standardize your processes and procedures, VLAN tags can actually cause more management difficulties than working in an untagged VLAN environment.
Your team should only go into a VLAN tagging project only if you stand to benefit from features like inter-VLAN routing, more granular policy management, and stronger broadcast controls. If you’re primarily looking to set up an easy-to-use VLAN environment for simple user devices and VLAN classifications, untagged VLANs will likely meet your needs.
Also read: Microsegmentation Is Catching On as Key to Zero Trust
7 VLAN Tagging Best Practices
VLAN tagging isn’t easy, but following these best practices will help you get it right.
1. Maintain Consistent VLAN Standards
To make sure your tags don’t get too confusing and devices on your VLAN remain compatible with each other, stick to a standardized naming convention and uniform tagging standards. With VLAN tagging in particular, users have the option to choose between different methodologies and standards, such as IEEE 802.1Q and ISL. Either standard may be the right fit for your organization, but choosing to work with both can create a mixed tagging scenario where it’s easier to lose track of traffic, misconfigure different aspects of the VLAN, and generally have information packets get misunderstood or misdirected.
2. Monitor and Audit for Dual Tagging and Other Tagging Errors
Different tagging errors can easily crop up in your VLAN environment, especially if multiple users and teams are working on tagging initiatives. To make sure you don’t end up with a scenario like information packets with dual tags, continually monitor traffic moving within and across VLANs with network monitoring tools. For the occasional, more in-depth analysis of tag quality, make VLAN tag assessment a part of your regularly scheduled network audits and vulnerability assessments.
3. Control Broadcast Domain Size
Regardless of how well you tag your VLANs and information packets, your network can still get bogged down and run slowly if your broadcast domain and the traffic within that domain grows too large. As your network activity continues to grow, consider creating new sub-VLANs in order to reduce broadcast traffic and make it easier to manage network security and performance in granular segments.
4. Consider Users, Use Cases, and Other Logical Groupings for Tags
Tag groups can be aligned to nearly any category or classification, so it’s best for organizations to think through how they want to group their virtualized network traffic. Do you have third parties, stakeholders, or employees who need more or less access to certain resources? Are certain devices or applications being used in a way that takes up more bandwidth and requires special attention? Do certain devices transmit data that requires stricter data security and compliance practices? These are all questions that should inform how you divide up and tag individual VLANs.
5. Invest in Network Monitoring and Other Cybersecurity Tools
Network monitoring solutions can prevent bigger cybersecurity issues from spiraling out of control on any type of network, including a virtualized network like a VLAN. As a bonus, certain network monitoring tools give users the levels of customization necessary to track VLAN tagging elements, including if certain information packets have been mistagged or accidentally received multiple tags.
Related: 34 Most Common Types of Network Security Solutions
6. Use Staging Environments to Test VLAN Configurations
Misconfigurations are some of the most common issues — and security threats — that networking professionals face when they first get started with VLANs and VLAN tagging. Although working out the kinks in a staging environment might not solve all your problems, especially as network traffic and devices grow more complex, getting your VLAN initially configured in a staging environment gives you a chance to test its capabilities and performance without negatively impacting your actual network’s performance.
7. Keep VLAN Tagging Documentation Up-to-Date
As team members leave and new team members are brought on to your IT and networking teams, the only way to ensure everyone knows how to maintain current VLAN tagging standards is through detailed, up-to-date documentation. Any time a new VLAN or VLAN ID is created and also as internal standards or rules for data management change, be sure to update that documentation and keep it in a location where all relevant stakeholders can access it. For better results, require that all internal networking professionals go through regular training on VLAN tagging and VLAN usage best practices.
Top Issues Faced With VLAN Tagging
VLAN tagging, when performed correctly, can help networks operate more efficiently and securely. However, the opposite may become true if networking professionals aren’t careful. Keep an eye out for the following most common issues faced with VLAN tagging as you embark on a tagging project:
Misconfigurations
There are a lot of different components and moving parts involved in VLAN tagging. Because of its complexities, organizations frequently misconfigure their VLANs and VLAN tags with errors like mismatched VLAN IDs, untagged ports, misconfigured switches and trunks, and overloaded VLANs that hold too many devices and cause network congestion. These issues can not only cause the network to perform more slowly and inefficiently but can also lead to security issues like unauthorized access.
Management Costs
Although correctly configured VLAN environments often lead to cost savings, there are still areas of VLAN management and VLAN tagging that can be cost-prohibitive. For example, smaller organizations may not be able to afford initial costs or maintenance costs for specialized servers like RADIUS servers.
Limited Internal Expertise
Not all organizations have enough in-house expertise or the resources to work with an expert third party for VLAN tagging projects. Whether it’s during initial implementation, ongoing monitoring, or periodic troubleshooting, many organizations run into issues they can’t solve when certain components aren’t working as intended.
Consistent Maintenance and Monitoring Requirements
Related to the issue of limited internal expertise, many companies do not have the resources they need to continually monitor for network performance issues and emerging security vulnerabilities, which causes them to struggle with maintaining high VLAN standards. VLANs require complex network operations to run smoothly, especially since so many devices and networking tools are involved. Interoperability, network traffic, quality of service (QoS) policies, and user access controls are all complex issues networking professionals need to stay on top of for VLANs and their tags to serve their purpose.
Bottom Line: Getting VLAN Tagging Right
VLAN tagging can be a complex process if your team isn’t prepared to keep up with and monitor network configurations, and especially if your team has greener networking professionals. However, especially for larger companies that are managing large swathes of varied traffic and user types, VLAN tagging is one of the most effective, cost-efficient, and scalable ways for system administrators to manage cybersecurity; bandwidth; network performance; and role-based, device-based, and traffic-based controls. Network administrators can reap all sorts of benefits from this organizational management framework for VLANs so long as they’re willing and able to troubleshoot their tagging setups and methodologies consistently.
Read next: Network Protection: How to Secure a Network




