As cybercriminals continue exploiting emails — the backbone of business communications — for phishing and domain impersonation, DMARC is a critical first line of defense.
Without robust safeguards, attackers can spoof trusted domains, deceiving employees, customers, and partners. DMARC detects and blocks fraudulent emails before they reach inboxes, strengthening an organization’s email security posture.
This comprehensive guide will explain DMARC, its operation, its pros and cons, and common misconceptions about it.
What Is DMARC?
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is an email security protocol that prevents outbound emails from spoofing. It empowers domain owners to set policies that specify how receiving mail servers should handle emails that fail authentication checks, protecting against phishing and other email-based threats.
Global enterprises like Microsoft, Google, and Paypal use DMARC to safeguard communications and maintain customer trust. By reducing the risk of impersonation and phishing attacks, DMARC boosts overall network security.
How Does DMARC Work?
DMARC protects domains from fraudulent emails by verifying messages through two vital email protocols: Sender Policy Framework (SPF) and DomainKeys Identified Message (DKIM).
SPF checks whether the server sending the email is allowed to send messages to a specific domain, while DKIM adds a digital signature to confirm the message has not been altered in transit.
DMARC takes this a step further by making sure the “From:” address in the email matches the results of the SPF and DKIM checks. This alignment is important for determining how to handle emails that fail authentication.
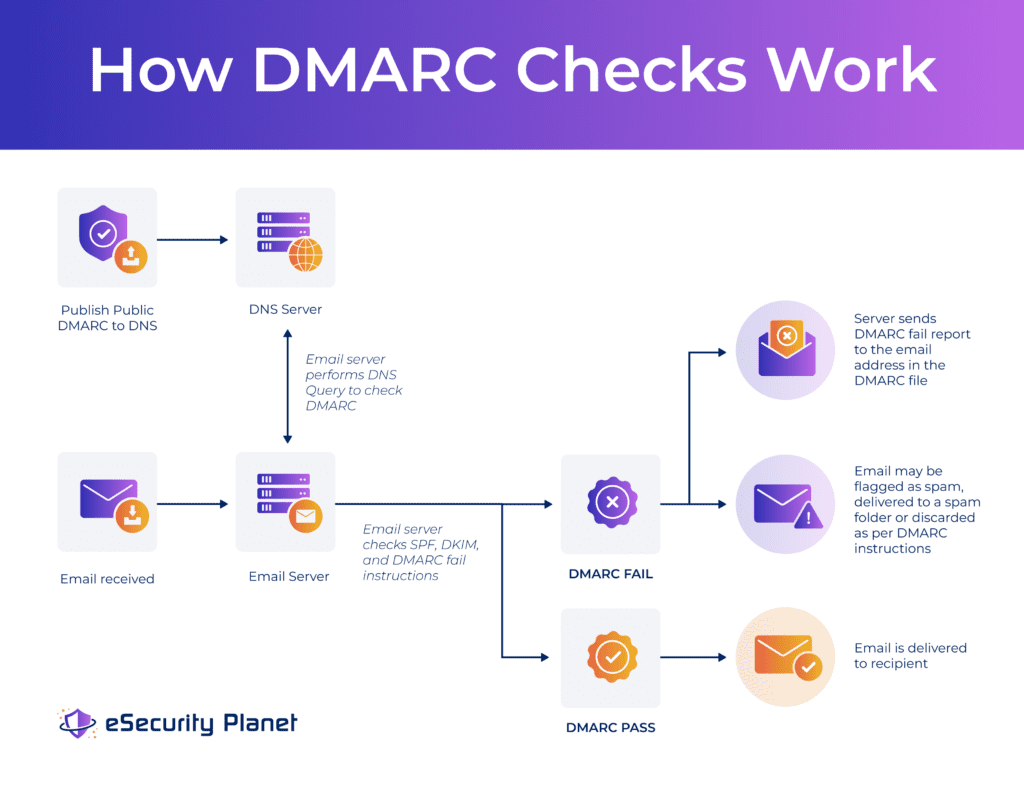
DMARC Policy
The first step in the DMARC process is setting up a DMARC policy, added to a domain’s DNS record.
This policy defines how the receiving servers should handle emails that fail SPF or DKIM checks. It also enables DMARC Alignment, which checks between the “From:” field displayed in the email and the “From:” field in the header. This counters a common spoofing technique where the attacker changes the “From:” field to impersonate a trustworthy sender.
The policy also specifies where compliance and forensic reports should be sent for any failed messages.
DMARC Record
Once the policy is defined, it is published in the domain’s DMARC record within the DNS. Without a proper record, policy enforcement and reporting are impossible. This information is publicly available, so email servers can query it to check the domain’s authentication rules.
For example, Microsoft’s DMARC.TXT file reads as:
_dmarc.microsoft.com. 3600 IN TXT "v=DMARC1; p=none; pct=100; rua=mailto:d@rua.contoso.com;
ruf=mailto:d@ruf.contoso.com; fo=1"
For a complete list of variables and options for the DMARC record, see the DMARC Setup Guide: How to Implement a Basic DMARC Setup.
DMARC Alignment
A core element of the DMARC email protocol is alignment, in which the domain in the message’s “From:” field is compared against other authenticated domain names from the SPF and DKIM checks. If either SPF or DKIM alignment checks pass, then the DMARC alignment test passes.
DMARC supports both strict or relaxed alignment:
- Strict Alignment: Requires the domain names to be identical.
- Relaxed Alignment: Allows the top-level “Organizational Domain” to fulfill the match requirement.
DMARC Policy Enforcement
With alignment confirmed, the receiving mail server applies the DMARC policy in the domain’s DNS record. Depending on the policy, the server will take one of the following actions:
- p=reject: Rejected emails go undelivered to the recipient.
- p=quarantine: Emails marked as suspicious and sent to the spam folder.
- p=none: No action is taken, and the email is delivered regardless of SPF or DKIM failure.
DMARC Reports
Finally, DMARC generates aggregate and forensic reports, so organizations can monitor authentication failures and detect potential attacks. These reports are in machine-readable formats that may require third-party DMARC reporting tools for analysis. They are often sent as .zip attachments, so the designated email must support this file type.
- Aggregate DMARC Reports: These offer statistical data on emails claiming to be from an organization’s domain. These XML reports show authentication results (pass/fail) and how messages were handled. Aggregate reports track delivery rates, detect misconfigured internal senders, and spot spoofing attempts.
- Forensic DMARC Reports: These reports provide copies of email messages that fail DMARC authentication. An organization can analyze these emails to troubleshoot its domain authentication issues or to spot malicious websites and domains.
DMARC Advantages
As of late 2024, about 20% of the top 10 million domains have implemented DMARC, showing how organizations see its value in bolstering email security. DMARC introduces a range of advantages that significantly reduce the risk of email-based threats, enhance customer trust, and elevate the effectiveness of email communications.
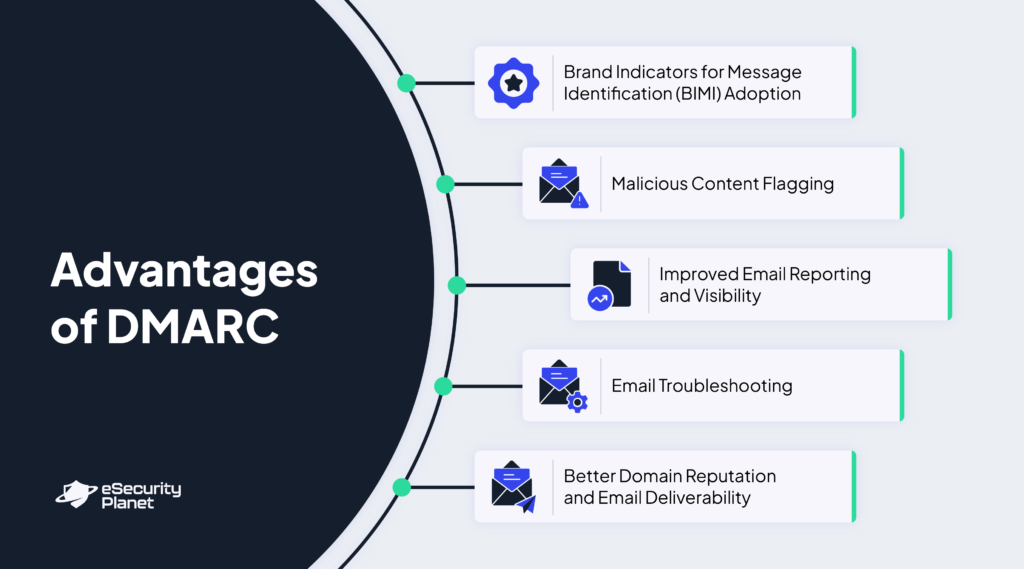
Brand Indicators for Message Identification (BIMI)
Organizations that deploy DMARC can adopt Brand Indicators for Message Identification (BIMI), a standard that enables a brand’s logo to display for authenticated emails. Large email providers such as Yahoo! or Gmail support this standard, improving brand recognition, trust, and engagement for email recipients.
Malicious Content Flagging
If an email fails authentication, DMARC flags this content and prevents its delivery, stopping Business Email Compromise (BEC) phishing and thwarting ransomware attacks. Content flagging also prevents a brand’s name from being impersonated to spread various malware types or engage in malicious activities, safeguarding its reputation — especially for high-profile organizations where impersonation can have severe consequences.
Improved Email Reporting and Visibility
Without the DMARC email protocol, businesses often struggle to understand why some emails get flagged as spam or fail to reach recipients. DMARC’s detailed reports explain email rejections and highlight why messages fail.
These reports also reveal any attempts to spoof the organization, providing insight into possible threats. Businesses can use this data to take proactive steps to boost the performance of their email campaigns and prevent third-party impersonation.
Email Troubleshooting
Besides letting organizations know if their emails are delivered, DMARC reports give insights into potential email setup issues. By analyzing these reports, businesses can find misconfigurations and refine authentication settings, so their messages are not mistakenly flagged as spam in the future.
Better Domain Reputation and Email Deliverability
DMARC shows internet service providers (ISPs) that an organization effectively manages its email security, strengthening its reputation. A good domain reputation boosts email deliverability, particularly for marketing campaigns. Some organizations cite a 5-10% increase in campaign success after enforcing DMARC email policies.
DMARC Disadvantages
While DMARC fortifies email security, it presents challenges that must be addressed to maximize its efficacy. Failing to manage these drawbacks will limit DMARC’s ability to protect organizations, leaving them vulnerable to risks.
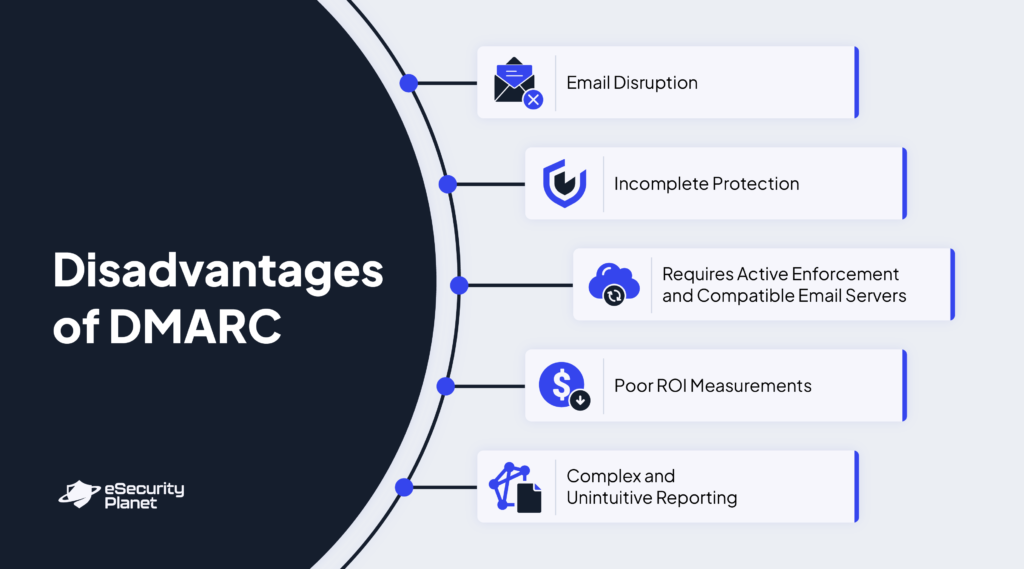
Email Disruption
Successful DMARC implementation requires careful testing to account for all legitimate email sources. An organization enforcing a strict DMARC policy without identifying such sources may accidentally block and disrupt otherwise valid emails. This can affect business communications and require ongoing monitoring to authenticate legitimate emails.
Incomplete Protection
DMARC prevents direct domain spoofing but does not protect against all cybersecurity traits, such as look-alike domain attacks. Cybercriminals can register domains with slight variations, like replacing “Amazon” with “Arnazon” or “Amaz0n.” Attackers may also configure SPF, DKIM, and DMRAC records for their malicious domains, allowing phishing emails to pass authentication checks.
Requires Active Enforcement and Compatible Email Servers
Active reinforcement and correct server configuration are necessary for DMARC to work. Many organizations opt for the “p=none” policy to avoid disrupting legitimate emails while fine-tuning their setup. However, this policy does not block spoofed emails, so organizations are still exposed.
Additionally, email servers must be configured to check SPF, DKIM, and DMARC records. Without this, phishing emails can bypass security measures, rendering DMARC ineffective.
Poor ROI Measurements
The benefits of DMARC, such as better email deliverability and brand protection, are difficult to quantify. While it helps lower phishing attacks, the primary beneficiaries are usually external parties — like email recipients — rather than the organization itself. This makes it harder for businesses to justify the costs of applying and monitoring DMARC, as the direct value may not be immediately clear or tangible.
Complex and Unintuitive Reporting
DMARC aggregate and forensic reports are designed for machine processing, making it difficult for humans to read and interpret. Third-party DMARC reporting or monitoring services are required to analyze these reports and gain actionable insights. Without these reporting tools, detecting unauthorized senders and troubleshooting email issues can be time-consuming.
DMARC Best Practices
Proper DMARC implementation and ongoing maintenance are essential for stronger email security. Otherwise, misconfigurations can occur, inadvertently blocking legitimate emails or creating protection gaps that allow phishing attacks to succeed.
Following best practices to ensure DMARC strengthens email authentication without disrupting business communications is important. This way, organizations can prevent spoofing attempts while maintaining smooth email operations.

- Begin with a Monitoring Phase: Administering DMARC too quickly can cause issues if allowable senders are not accurately configured. Organizations should start with a ‘“p=none” policy, to collect email authentication reports without affecting delivery. These reports help uncover authorized and unauthorized senders, making it easier to adjust settings before stricter enforcement.
- Gradually Deploy DMARC Policies: Organizations should gradually enhance their DMARC policy after identifying legitimate senders. Moving from “p=none” to “p=quarantine” filters suspicious emails rather than outright blocks them. Once it is confirmed that only unauthorized messages are being affected, the policy can be set to “p=reject” to stop the delivery of phishing emails.
- Maintain Accurate SPF, DKIM, and DMARC Records: SPF and DKIM must be correctly configured for DMARC to work as intended. SPF should list all valid email-sending sources and DKIM must be applied to outgoing emails. Updates are also needed when email providers or third-party services change.
- Continuously Review and Adjust Email Authentication Settings: Companies frequently use new tools for marketing, customer support, and internal communication, which could affect email authentication. Regularly checking DMARC reports helps detect unauthorized senders and verify that authorized ones have the correct configurations.
- Use DMARC Reporting Tools for Better Visibility: Raw DMARC reports can be challenging to interpret without specialized tools. DMARC monitoring services aid organizations in visualizing authentication data, pinpointing spoofing attempts, and responding more efficiently to security threats.
Misconceptions About DMARC
Some misconceptions about DMARC can lead to misimplementation or compromise email security. Understanding this email protocol’s true capabilities and limitations is imperative for organizations to benefit from its protection against phishing and spoofing attacks.
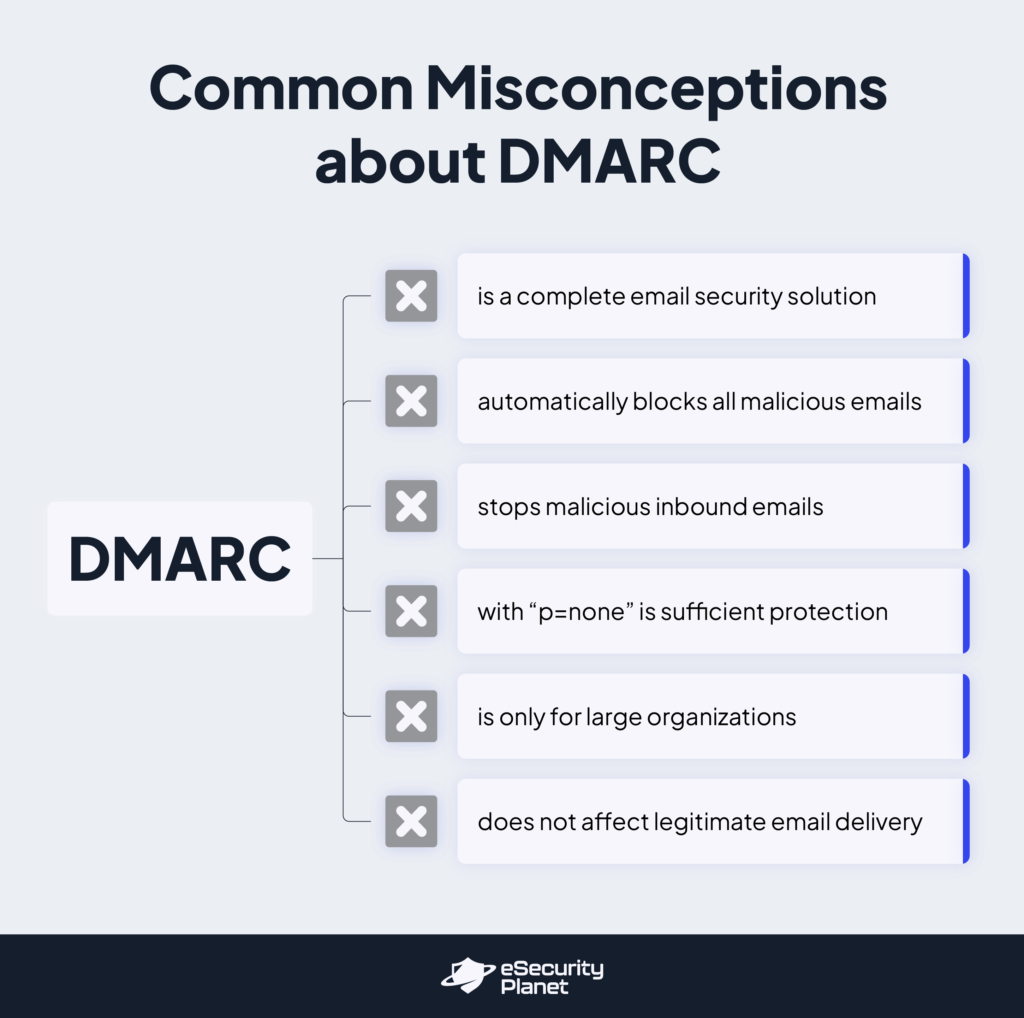
- DMARC is a Complete Email Security Solution: DMARC is not a standalone solution for all email security risks. While it is key to verifying the authenticity of emails through SPF and DKIM, it cannot prevent all types of threats, such as lookalike domain attacks. Organizations should use DMARC alongside other measures, like threat intelligence, email filtering, and even email security software to reinforce email protection.
- DMARC Automatically Blocks All Malicious Emails: DMARC does not automatically block all malicious emails. It only verifies whether an email aligns with SPF and DKIM records and takes action based on the configured policy. Even though it can reject or quarantine unauthorized messages, emails from compromised accounts can still go through.
- DMARC Stops Malicious Inbound Emails: Another common misconception is that DMARC can block all inbound phishing emails. It prevents attackers from impersonating your domain in outbound emails by authentication. Filtering harmful inbound messages relies on spam filters and antivirus programs.
- Setting DMARC to “p=none” Is Sufficient: Setting DMARC to “p=none” does not actively protect against spoofed emails — it only generates reports without taking action on failed messages. To block spoofed emails effectively, organizations should move to “p=quarantine’ or “p=reject,” which either flags suspicious emails or completely rejects them.
- DMARC is Only for Large Organizations: Many assume that only large enterprises need DMARC, but businesses of all sizes are at risk of domain spoofing and phishing attacks. In reality, any organization with a custom email domain should use DMARC to stop cybercriminals from sending fraudulent emails on their behalf.
- DMARC Does Not Affect Legitimate Email Delivery: Some believe that DMRAC will never interfere with legitimate emails, but misconfiguration can cause valid messages to be rejected or marked as spam. Appropriate setup and ongoing monitoring are vital to ensure smooth email delivery.
DMARC: Frequently Asked Questions (FAQs)
Do All Email Service Providers Support DMARC?
Unfortunately, no. The email service provider needs to set a custom Return-Path domain to collect email bounces separate from the email address used in the “from” address. This Return-Path domain must be at the same top-level domain as the “from” address, and some vendors do not always support this option.
Do You Need DMARC for Email?
Yes. DMARC is indispensable for any business that values email deliverability, security, and brand reputation, regardless of size. It is considered an industry-standard best practice for protecting your brand and domain name and your sending reputation, which is key for email deliverability.
Bottom Line: Understanding What is DMARC for Email Security
Email remains a primary target for cybercriminals, making DMARC more important than ever. Although this email protocol has challenges to be addressed, its potential to prevent domain spoofing and take email security to the next level makes it a substantial tool for any organization.
A well-configured DMARC policy safeguards your domain and helps build trust in your communications. As attackers develop new tactics, organizations that bolster their email security will be better equipped to uphold their name and integrity while protecting their users.
Find out how to fortify your email defense by reading our guide on how to improve email security for enterprises.




