Stateful inspection is a firewall feature that filters data packets based on the context of previous data packets. This important feature uses header information from established communication connections to improve overall security. An understanding of how stateful inspection works, the key pros and cons, and its use cases provides important insight into how stateful inspection can be used successfully in a security stack.
How Does Stateful Inspection Work?
Stateful inspection reads and stores header information from established communication protocols. The stored information informs the state or condition of communication at any given time. The packet context based on the communication history and the stored state information then provides the circumstances and conditions to use more complex firewall filtering rules to validate legitimate packets and block attacks attempting to corrupt protocols.
Packet State
A packet state indicates the current status of a communication connection. Each time two computers begin communicating, they exchange information to establish the connection and subsequently the header of each data packet contains information about the specific connection.
Stateful inspection primarily operates on the transport control protocol (TCP) used in critical and fundamental protocols such as file transfer protocol (FTP) and secure web browsing (HTTPS). The TCP state changes for each stage of communication by using synchronization (SYN), acknowledgement (ACK), finish (FIN), and data packets between the initiating device and the second device receiving the communication, as outlined in the table below:
| Initiating Device State | Second Device State | Packet | Purpose & Effect |
|---|---|---|---|
| Closed | Listen | <no packet> | Initial state status |
| Syn_Sent | Listen | SYN | Initiating device sends a SYN request to initiate communication |
| Syn_Sent | Syn_Recd | SYN+ACK | The second device sends a SYN and an ACK response to establish communication |
| Established | Syn_Recd | ACK | Initiating device sends an ACK response to confirm communication |
| Established | Established | <no packet> | Second device receives initial ACK |
| Established | Established | <data packet with first sequence number> | Initiating device sends first data |
| Established | Established | ACK (with first sequence number) | Second device sends ACK to confirm receipt of the first data packet |
| Established | Established | <data packets increment sequence number as needed> & ACK responses | Both devices can now send data with incrementing sequence numbers, each confirmed by an ACK response |
| FinWait_1 | Established | FIN | Initiating device attempts to end communication with a FIN packet |
| FinWait_1 | CloseWait | ACK | Second device acknowledges FIN request |
| FinWait_2 | Last_ACK | FIN | Second device also sends a FIN request to end communication |
| TimeWait or Closed | Last_ACK | ACK | Initiating device sends final FIN request acknowledgement |
| TimeWait or Closed | Closed or Listen | <no packet> | Both devices end communication |
Packet Context
Packet context compares the information in each data packet header against the communication state based upon IP address, sequence code, port number request, and protocol. The stateful inspection allows expected packets and blocks unexpected packets that conflict with the communication state.
For example, a firewall performing stateful inspection may be tracking an active FTP transfer with the FTP server and show a network laptop in a Listen or Closed status. The firewall allows ACK or FIN packets sent to the active FTP connection (with the correct IP sender and receiver, protocol, port, and sequence number) but won’t expect and therefore drops any ACK or FIN packet sent to the laptop.
Stateless protocols (UDP, HTTP, etc.) don’t use sequences or acknowledgements, but the firewall or other device performing stateful inspection can still store information regarding ports, device profiles, and sending or receiving IP addresses. This pseudo-stateful condition lacks the same security detail, yet still provides effective defense against some attacks.
What Stateful Inspection Defends Against
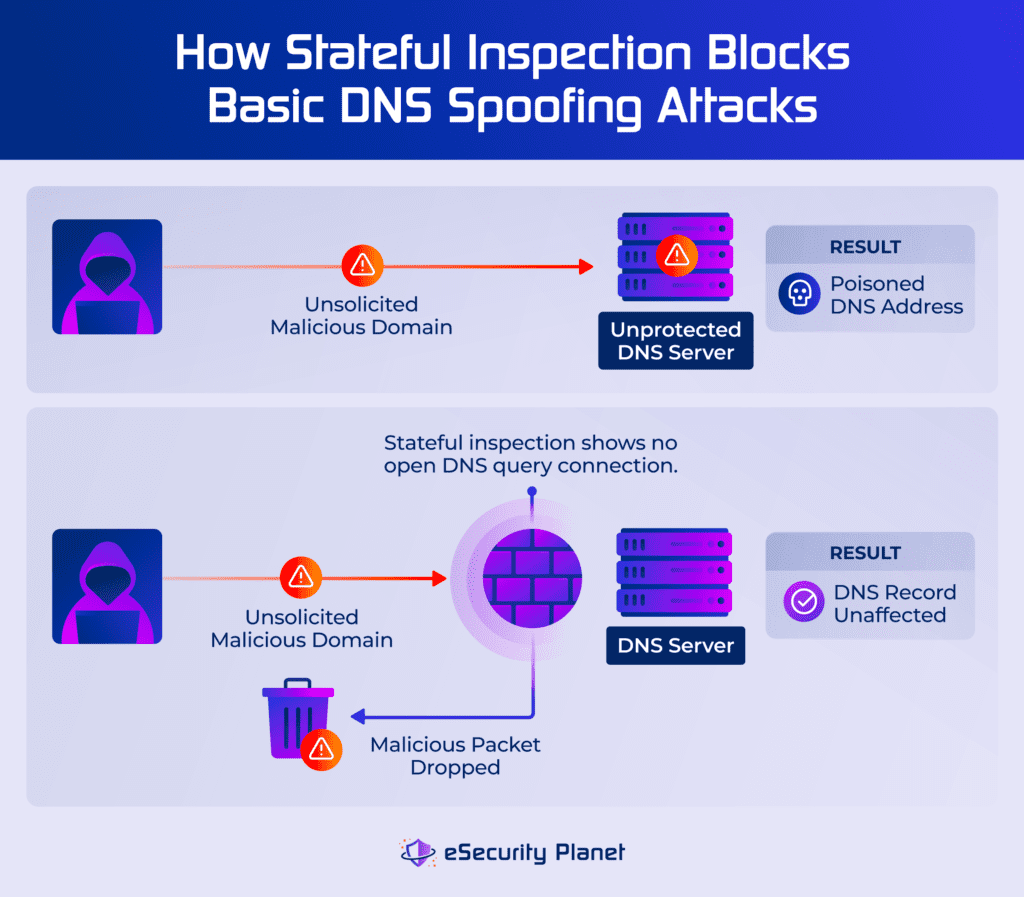
Stateful inspection protects network assets against attacks that attempt to corrupt or abuse processes such as TCP or Domain Name Service (DNS) that don’t check context when they receive data packet instructions. The state and context information saved by the firewall or other device performing stateful inspection provides the context used to block DNS spoofing and distributed denial of service (DDoS) attacks.
For example, DNS stores the IP addresses associated with URLs such as eSecurityPlanet.com, but attackers understand many DNS implementations fail to check for valid requests. Attackers send unsolicited answers (DNS spoofing) with incorrect information such as an unsolicited response with the IP address for URHacked.ru instead of eSecurityPlanet.com. Stateful inspection would block these unsolicited attempts that don’t match open DNS inquiries.
Use Cases for Stateful Inspection
Check Point Technologies developed stateful inspection to advance network firewalls and provide more sophisticated defense against common attacks. However, some host-based firewalls, gateways, and specialized equipment also incorporate stateful inspection for specific security use cases to hide high-value assets or block DDoS attacks.
Network Security
Stateful inspection improves general network and cloud security for all assets screened by the feature. Previously, rules could only view each packet individually and apply static rules. Adding the state and context for each communication channel creates opportunities to apply dynamic rules that detect and block unsolicited, anomalous, and some types of malicious communication.
Discovery Prevention
Firewalls can establish rules to block any communication originating outside of a network segment or a cloud environment unless it comes from specifically allowed devices (aka allowlist or whitelist). The stateful inspection drops an attacker’s attempts to learn about high-value assets, such as database servers, using common network exploration tools such as ping or Nmap.
Server DDoS Protection
A common DDoS attack uses spoofed TCP packets to overwhelm a server. TCP lacks stateful checks so a DDoS attacker might send a large number of unsolicited SYN-ACK responses and a server would tie up resources attempting to match the packets to open communication. A stateful packet inspection tracks open communication and quickly drops the packets from this and many other similar types of attacks.
5 Advantages of Stateful Inspection
Stateful inspection provides five distinct security improvements for all types of firewalls based upon the applied context of communication history:
- Advanced rules: Enables more detailed rules that incorporate identity, connection state, and application into consideration to allow or deny the communication data packet.
- Dynamic inspection: Adapts policies to the context of each communication session based on previous packet analysis and recorded experiences with the IP address.
- Enhanced protection: Catches more DDoS, Domain Name Service (DNS) spoofing, and similar types of attacks that attempt to fool vulnerable processes.
- Improved flexibility: Applies advanced rules and dynamic inspections to enable a robust decision making process that can quickly adjust to block perceived threats.
- Robust logging: Provides more detailed context and packet information in the produced log records to improve incident response, threat analysis, and forensic investigation.
5 Disadvantages of Stateful Inspection
Although stateful inspection provides many advantages, the feature can’t provide foolproof security due to its weaknesses:
- Communication breakdown: Introduces errors for certain categories of communication such as asymmetric routing that uses different paths or slow connections.
- Increased complexity: Requires more complex rules to flexibly handle multiple conditions and combinations, which can leave security gaps or cause rule conflicts.
- Resource intensiveness: Needs more resources to store states on past and continuing communication connections as well as to continue to perform analysis and apply rules.
- Security vulnerabilities: Remains weak to various spoofing attacks, can’t recognize application attacks, and doesn’t inspect packet contents for potential malware.
- Slowed traffic: Takes more time to store state information and perform packet filtering compared to the simple rule processing of stateless packet inspection.
Stateful Inspection vs Other Firewall Features
Stateful inspection provides a powerful tool implemented in most firewalls, but most admins will combine stateful inspection with other firewall capabilities to maximize both security and operations benefits. Here’s a brief comparison against other firewall features that provide different capabilities:
Stateful vs Stateless Inspection
All packet inspections fall into either stateful or stateless inspection. Stateful packet inspection retains information regarding established connections to greatly improve security but also requires more resources and processing power. Use stateless packet filtering features or firewalls to rapidly drop packets based on simple rules to reduce the traffic subjected to the more complex stateful analysis.
Stateful vs Deep Packet Inspection
Stateful inspections examine the communication information contained in data headers to quickly drop easily detected malicious packets. Add deep packet inspection features to next-generation firewalls to examine the data contents of the remaining packets and provide additional protection such as blocking malware deliveries within established HTTPS connections.
Stateful vs Proxy Filtering
Stateful inspections examine, but don’t alter, communication connections between two devices, which enables external attackers to probe the network. Establish additional proxy capabilities used in circuit level gateways or application layer gateways to establish separate connections between the firewall and each device. This additional filtering blocks asset discovery and enables additional opportunities to detect malicious intent without slow deep packet inspection.
Bottom Line: Stateful Inspection Begins Communication Protection Processes
Stateful inspection significantly improves security protection for network communication but can’t provide protection against all attacks. Even when combined with other strong features such as packet filtering, or deep packet inspection, firewalls only provide an initial layer of defense that requires other layers of defense to adequately reduce attack risk.
To strengthen security, learn more about other network security solutions such as intrusion detection and prevention systems (IDPS) that monitor and detect potential attacks within network communication traffic.




