Standalone cybersecurity tools are not enough to maintain the security posture of an entire organization. Between malware, phishing attacks, zero-day threats, advanced persistent threats, reconnaissance, and brute force attacks, hackers are looking for any and every avenue into a network.
If organizations don’t opt for full security suites, several solutions may be needed to protect against these threats. Let’s cover some of the most important cybersecurity software and tools in your security arsenal and some of the best vendors in each category.
Top Cybersecurity Software
We’ve narrowed this list down to four categories of software that are essential to modern cybersecurity: Extended detection and response (XDR), next-generation firewalls (NGFW), cloud access security brokers (CASB), and security information and event management (SIEM).
If you’re looking for antivirus software, see our list of the best ones.
- XDR
- NGFWs
- CASBs
- SIEM
Best Extended Detection & Response (XDR) Tools
Extended detection and response (XDR) software combines multiple cybersecurity tools, including endpoint detection and response (EDR), threat intelligence, and network traffic analysis. Rather than monitoring endpoints alone, like EDR, XDR takes a multi-layered security approach, covering email, endpoints, cloud environments, and on-premises networks.
XDR typically pairs well with secure access service edge (SASE) platforms to include coverage for Internet of Things (IoT) devices and the network edge.

ESET PROTECT Enterprise
ESET PROTECT Enterprise is a robust security solution designed to protect organizations of all sizes with an integrated approach to endpoint security, threat detection, and response. It excels in automated and manual threat remediation, leveraging its XDR capabilities to provide real-time visibility across endpoints.
Pros
Cons
ESET PROTECT Enterprise offers flexible pricing, from approximately $39 per endpoint to $140+ annually, with discounts available for larger organizations or multi-year subscriptions.
- Advanced Machine Learning: Detects and blocks sophisticated threats through AI-driven models, even before they can be executed.
- Multi-Layered Protection: Combines endpoint detection and response (EDR) with cloud sandboxing, network attack protection, and full disk encryption.
- Centralized Management Console: Administrators can monitor, manage, and respond to incidents through a unified interface.
- Customizable Reporting and Alerts: Users can prioritize critical threats and reduce false positives.

Cisco XDR
Cisco XDR is a comprehensive, cloud-native platform that integrates Cisco’s extensive security portfolio, including Secure Endpoint, Secure Network Analytics, and Threat Response. Its XDR solution offers cross-platform threat detection and remediation with deep integrations into Cisco’s security products, providing a seamless experience for security teams.
Pros
Cons
Cisco XDR is available as part of Cisco SecureX, with pricing depending on the size of your organization and specific deployment requirements. Licensing typically starts at around $0.99 per month up to $140+ for larger organizations, with custom pricing for enterprise-scale solutions.
- Cloud-Native Architecture: Ensures scalability and ease of deployment, leveraging Cisco’s cloud security infrastructure.
- Unified Threat Intelligence: Combines data from across Cisco’s security ecosystem to comprehensively view potential threats.
- Automated Playbooks: Offers customizable automation workflows for streamlined responses to common security incidents.
- Cross-Layer Detection: Detects threats across endpoints, networks, email, and cloud applications for comprehensive protection.

CrowdStrike Falcon Insight XDR
CrowdStrike Falcon XDR offers a unified command console that enables swift threat identification and remediation, providing cross-platform attack insights and alerts to accelerate response times.
Automated multi-stage workflows reduce the burden on security teams by streamlining threat mitigation, while advanced analytics detect threats without manual rule adjustments. Its extensive integrations allow cybersecurity experts to connect and correlate data from various tools into a single console, enhancing visibility and coordination across the entire organization.
Pros
Cons
CrowdStrike Falcon Insight XDR is priced per endpoint, with options starting at around $59.99 per endpoint monthly. Pricing may vary based on the number of endpoints and additional features included.
- CrowdStrike Threat Graph: Analyzes over 1 trillion events per week, enabling rapid threat detection and response across the enterprise.
- Cloud-Native Platform: Scalable, easy to deploy, and doesn’t require extensive on-premises infrastructure.
- Extended Coverage: Protects endpoints, identities, cloud environments, and workloads, providing visibility across the entire attack surface.
- Automated Threat Remediation: Integrates AI and machine learning to automate detection and response, minimizing human intervention.
Best Next-Generation Firewalls (NGFWs)
Next-generation firewalls (NGFWs) extend traditional firewall protection from the network layer to the application layer to prevent breaches and add threat intelligence from outside the network. They still validate traffic via packet filtering and VPN support, but they can also use whitelists or a signature-based IPS to determine whether applications are safe or not.

Cisco Secure Firewall
Cisco Secure Firewall (formerly known as Firepower) is an advanced NGFW solution that integrates deeply with the Cisco security ecosystem. It offers comprehensive threat detection, visibility, and real-time protection. It stands out with its encrypted traffic analysis, enabling the detection of threats within encrypted streams without decryption. It is ideal for businesses of all sizes, providing robust security across on-premise, cloud, and hybrid environments.
Pros
Cons
Cisco Secure Firewall pricing varies depending on the deployment (on-premise or cloud), the size of the network, and the security features required. It typically costs around $2,000 per firewall device, with subscription fees for security services such as threat intelligence.
- Advanced Malware Protection (AMP): Real-time detection and blocking of malware, including sandboxing and retrospective threat analysis.
- Intrusion Prevention System (IPS): Proactively prevents known vulnerabilities and potential attacks.
- Encrypted Traffic Analytics (ETA): Monitors and detects malware even in encrypted traffic.
- Seamless Cloud Integration: Integrates with multi-cloud environments to protect both cloud-native and hybrid setups.
- Threat Intelligence via Talos: Provides real-time global threat intelligence from Cisco’s Talos threat research team.

Palo Alto Networks NGFW
Palo Alto Networks NGFW is known for its cutting-edge technology in identifying, controlling, and securing applications, users, and data across networks. With their proprietary App-ID and Content-ID technologies, these firewalls provide granular control over applications and deep visibility into network activity.
Its NGFWs also use machine learning to enhance threat detection and improve security posture. This firewall suits organizations of all sizes, from small businesses to large enterprises.
Pros
Cons
Palo Alto Networks NGFW pricing starts at about $1,000 for the entry-level PA-220, while the high-end PA-7000 series begins at around $200,000. The rugged PA-220R offers up to 320 Mbps in threat prevention throughput, whereas the flagship PA-7080 delivers an impressive 300 Gbps and can handle up to 6 million new sessions per second.
- App-ID Technology: Identifies applications regardless of port, protocol, or encryption, ensuring granular control over all network traffic.
- Threat Prevention: Blocks known threats, exploits, and malware using signatures and machine learning models.
- WildFire: Cloud-based malware analysis environment that inspects suspicious files and ensures zero-day protection.
- User-ID: Associates network activity with individual users, providing insight into user behavior and security events.
- PAN-OS Operating System: Centralized management of security policies and threat prevention across multiple firewall instances.

Forcepoint
Forcepoint stands out as a Visionary in Gartner’s evaluation, offering an NGFW that seamlessly connects and protects users and data across an organization’s offices, branches, and cloud environments. Security teams can swiftly deploy, monitor, and update thousands of firewalls, VPNs, and intrusion prevention systems (IPS) through a centralized console, whether on-premises or through a managed service provider.
The solution includes high-availability clustering and SD-WAN capabilities, working harmoniously with the Forcepoint Human Point System to enhance user and data protection alongside cloud and access gateway security. A unified software core ensures consistent operation and performance across all physical, virtual, and cloud-based appliance types.
Pros
Cons
Pricing for Forcepoint’s NGFWs varies based on capacity and features, starting at under $1,000 for the small office/home office model. The high-end 6200 series is priced at over $100,000, while the 2105 model tested by NSS Labs is approximately $40,000.
- Multi-Link Capabilities: Enables load balancing and failover across multiple network links, ensuring continuous uptime.
- Intrusion Detection and Prevention (IDPS): Prevents attacks by detecting vulnerabilities and stopping exploits in real-time.
- Sandboxing: Isolates and analyzes suspicious files to detect malware and zero-day exploits.
- Unified Central Management: Allows simplified management of multiple firewall instances across various locations.
- Data Loss Prevention (DLP): Protects sensitive data by preventing unauthorized sharing and transfers.
Best Cloud Access Security Brokers (CASBs)

Censornet
As part of the vendor’s Autonomous Security Engine (ASE) solution, Censornet Cloud Access Security Broker integrates adaptive multi-factor authentication, email security, and web security for comprehensive protection. Additionally, Censornet’s CASB includes Identity as a Service (IDaaS) to ensure secure user authentication.
Censornet provides robust reporting capabilities, featuring pre-built trend reports that users can easily download and share with colleagues or clients. Security teams can access multiple report views, allowing them to analyze data by device, threat level, user, and other criteria for enhanced visibility and decision-making.
Pros
Cons
The email security plan begins at just £1.70 per user per month, while the web security and antivirus plan is available starting at £2.30 per user per month. For those interested in the CASB plan, pricing starts at £2.50 per monthly user. Contact their sales team to obtain a tailored quote for your business.
- Comprehensive risk assessment, rating, and categorization for cloud applications.
- Detailed policy-setting controls based on user, role, device, network, and function.
- In-depth audit reports featuring various criteria, such as application classification, risk level, and threat type.
- A dedicated security awareness training program to enhance user knowledge and preparedness.

Skyhigh Security CASB
Skyhigh Security’s CASB solution is designed to enforce data loss prevention policies, effectively blocking attempts to transfer corporate information to personal devices. Utilizing forward and reverse proxy methods for inline deployment ensures robust security across the board. The solution integrates via API with various business applications, including Slack, Zoom, and GitHub, alongside multiple identity and access management tools.
Originating from McAfee’s former cloud business, Skyhigh includes its CASB tool as a key component of its comprehensive SASE (Secure Access Service Edge) platform.
Pros
Cons
Skyhigh offers a demo for potential customers and provides three plans: Essential, Advanced, and Complete. Please note that the Essential plan lacks endpoint data loss prevention. For an accurate quote, contact Skyhigh’s sales team.
- A centralized policy engine that offers templates, import options, and the ability to create custom policies.
- Seamless integrations with existing security solutions, including SIEM, secure web gateways (SWG), next-generation firewalls (NGFWs), and enterprise mobility management (EMM).
- Advanced user behavior analytics to detect and mitigate potential insider threats.
- A Shadow IT Cloud Registry that evaluates the risks associated with cloud applications employees may wish to use.

Netskope
Netskope has established itself as a pioneer in CASB technology, consistently delivering robust security assessments and compliance solutions. The company has bundled several offerings into a comprehensive SASE solution. Key features of the CASB solution include the Cloud Exchange, which facilitates tech integrations with third-party security solutions like EDR and SIEM, and effective malware blocking for email and cloud storage services.
Pros
Cons
Prospective customers can request a demo from Netskope and schedule an executive briefing to develop tailored business solutions that meet their organization’s unique needs. For precise pricing information, please reach out to the sales team.
- Real-time encryption and key management that complies with certified FIPS 140-2 Level 3 standards.
- Seamless integrations with productivity tools, single sign-on (SSO), cloud storage, enterprise mobility management (EMM), and security applications.
- An intuitive dashboard that consolidates all traffic, users, and devices for SaaS, IaaS, and web activities.
- Role-based access control tailored for administrators, analysts, and other privileged user roles.
Best Security Information & Event Management (SIEM) Solutions
Security Information and Event Management (SIEM) solutions enable organizations to monitor their networks for threats and vulnerabilities through a unified management console. These tools offer real-time analysis, enhanced network visibility, and contextual alerts, allowing businesses to effectively track threats across their entire environment.
However, SIEM systems require skilled cybersecurity professionals to manage and monitor them, making them less ideal for small businesses that lack dedicated in-house security teams.

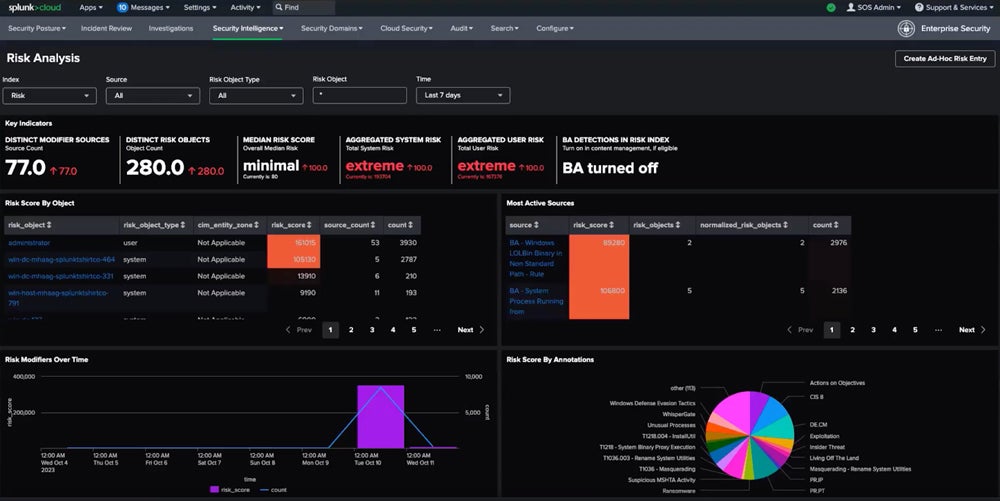
Splunk Enterprise Security
Splunk Enterprise Security is a robust, analytics-driven SIEM solution that scales across both on-premises and multi-cloud environments. Renowned for its powerful threat detection capabilities, Splunk offers unmatched flexibility with access to over 2,800 integrated apps, seamlessly connecting data and workflows.
Its industry-leading IT observability tools make it an excellent choice for gaining deep, comprehensive insights into an organization’s entire IT landscape, offering a unified security and operational efficiency platform.
Pros
Cons
- Vendor price: Contact Splunk
- Marketplace price: $150+ per month per 1 GB data
- Free trial: Available for 60 days via Splunk Enterprise
- Categorizes risks based on user and system compliance with established security frameworks, ensuring adherence to industry standards.
- Scales efficiently for structured and unstructured data, enabling smooth processing of diverse data types and volumes.
- Features a threat intelligence management tool, enhancing the ability to analyze and respond to emerging cyber threats quickly.
- Offers flexible deployment options across cloud, IaaS, software, hardware appliances, or hybrid environments, catering to varied organizational needs.
- Provides access to over 700 detection rules aligned with frameworks like MITRE, NIST, Kill Chain, and CIS 20, ensuring comprehensive threat identification and response.

IBM QRadar
IBM Security QRadar SIEM is a top choice among enterprises, continuously evolving with the SIEM market. The introduction of the IBM Security QRadar Suite seamlessly integrates threat detection, investigation, response, SOAR, SIEM, EDR, and XDR into a unified platform for hybrid cloud environments.
Its global reach ensures localized support, deep regulatory expertise, and robust regional channels, making it a dependable solution for organizations worldwide. This comprehensive platform offers scalability and adaptability to meet the complex security needs of modern enterprises.
Pros
Cons
- Free version: Available but limited via QRadar Community Edition
- IBM QRadar SIEM (Software): $320 to $26,540 per month
- IBM QRadar SIEM (SaaS): $2,340 to $25,922 per month
- Custom plans: Contact IBM for a quote
- Free trial: Available through certain MSSPs
- Delivers continuous monitoring across both on-premises and cloud environments, ensuring complete visibility across the entire kill chain.
- Utilizes IBM’s Security X-Force and STIX/TAXII threat feeds for enriched, real-time threat intelligence that strengthens overall security posture.
- Provides extensive compliance support for key regulations like HIPAA, SOX, ISO, PCI, NIST, GLBA, GDPR, and CCPA, ensuring organizations stay audit-ready.
- Flexible deployment options include hardware appliances, software, SaaS, and virtual machines, making it adaptable to both on-premises and IaaS environments.
- Seamlessly integrates with diverse security ecosystems through access to over 450 interfaces, APIs, and an SDK, offering broad compatibility and functionality.

Securonix
Securonix is renowned for its innovative approach and strong SOAR integration capabilities. Its Unified Defense SIEM seamlessly combines threat detection, investigation, and response, offering a comprehensive security solution. The Autonomous Threat Sweeper enhances threat detection by leveraging the Snowflake Data Cloud for improved searchability. Additionally, the Threat Coverage Analyzer identifies security gaps in alignment with industry standards such as MITRE ATT&CK and US-CERT, ensuring robust protection against emerging threats.
Pros
Cons
- Vendor price: Contact Securonix Security Operations and Analytics Platform
- Marketplace price: $67,331+ per year for a basic SIEM subscription
- Free trial: Available for SaaS offering
- Offers centralized data ingestion across cloud, on-premises, and hybrid environments, utilizing a unified console to simplify data collection.
- Facilitates in-depth analysis by allowing comprehensive historical data searches, essential for identifying and managing slow-burning threats.
- Built for on-demand scalability, the SaaS subscription model ensures flexibility and efficiency in cloud-based security operations.
- Provides access to over 350 connectors and API-based interfaces, enabling extensive data collection from various cloud sources.
- Features an investigative workbench where users can create cases based on industry scenarios, enhancing practical application and analysis.
What are the Benefits of Cybersecurity Software?
Each type of software on this list offers multiple benefits as part of comprehensive cybersecurity defenses.
XDR Benefits
XDR adds to EDR’s capabilities by extending protection from endpoints to email, cloud, and on-premises networks. This lowers the operational costs of cybersecurity because security professionals don’t have to integrate and examine multiple tools to get a full picture of a threat. Additionally, XDR allows security teams to identify threats faster, so the threats have a smaller window to collect data and cause problems.
It also improves the productivity of security teams because they have a single management console for the organization’s entire environment. Additionally, the reports provide actionable insights on threats and security operations to secure the network against vulnerabilities.
NGFW Benefits
NGFWs are the third generation of firewalls. This new era introduced multiple new features alongside traditional firewall capabilities. Some of the most beneficial include:
- Intrusion prevention systems (IPS): Allows NGFWs to inspect, alert, and actively remove malware and intruders.
- Deep packet inspection (DPI): DPI offers targeted inspection and can locate, categorize, block, or reroute packets that contain problematic code or data payloads.
- Layer 7 application control: NGFWs can protect data in layer 7 of the OSI model, which presents data in a form that user-facing applications can use. This is commonly where distributed denial-of-service (DDoS) attacks occur, making it a critical protection layer.
CASB Benefits
CASB products are cloud-based or on-premise software solutions that enforce security policies, regulatory compliance, and governance requirements when accessing cloud services. These tools can manage single sign-on, log data, authentication and authorization, device profiling and encryption, and tokenization.
CASB solutions can also block access to cloud services if they detect unauthorized user or application attempts to access resources. They also alert teams of malware and other possible attacks when detected.
SIEM Benefits
SIEM products serve two primary purposes. The first is to collect, store, analyze, investigate, and report on logs and other data. The second is to alert security staff to the most important threats.
Insights pulled from this analysis help with the early detection of attacks, facilitate improved incident response, and assist in maintaining regulatory compliance. SIEM systems also typically incorporate threat intelligence feeds that offer data on correlated events to help identify attacks.
Frequently Asked Questions (FAQs)
What Are Some Top Features Of Cyber Security Software Tools?
Top features of cybersecurity tools include multi-layered detection engines using advanced threat intelligence to block spam, malware, and data leaks. They ensure business continuity with a 100% uptime SLA, keeping email accessible during outages. Multipurpose archiving stores and replicates data from email, files, and IMs to maintain data integrity.
These tools also simplify backup, recovery, compliance, and e-discovery. Additionally, end-user training enhances cybersecurity awareness, making employees a vital defense against cyberattacks.
Why Are Cyber Security Software Tools Important For Business?
Cyber security software tools are vital to protect businesses from criminal cyberattacks that cause business disruption, data leaks, and ransomware payments in increasing cases.
How Often Should I Update My Cybersecurity Software?
You should update your cybersecurity software regularly, ideally as soon as updates are available. Most software updates include new security patches and definitions to defend against emerging threats. Regular updates ensure that your system is protected against the latest vulnerabilities.
Is Cybersecurity Software Enough to Keep My System Secure?
While cybersecurity software is essential to your overall security strategy, it is not enough. Users must also follow best practices, such as using strong passwords, enabling two-factor authentication, keeping systems up to date, and being cautious of suspicious emails or websites.
Is Free Cybersecurity Software Effective?
Free cybersecurity software can provide basic protection but often lacks advanced features and may not offer the same level of support as paid versions. Investing in a premium solution is usually a better option for comprehensive protection, especially for businesses.
Bottom Line: Keep Your Data & Devices Safe with Leading Cybersecurity Tools
As cyber threats become more sophisticated, safeguarding your data and devices is more important than ever. The top cybersecurity tools for 2025 provide various solutions designed to meet the needs of individuals and businesses alike. Whether you need protection against malware, secure browsing, or comprehensive privacy management, these software options offer robust defenses to keep your information safe.
Choosing the right cybersecurity tool ensures that your personal and sensitive data is protected, giving you peace of mind as you navigate the digital world. Take the time to assess your security needs and invest in the best solution to stay protected against emerging threats.