The best alternative solutions to CrowdStrike Falcon are endpoint security and endpoint detection and response (EDR) platforms that help detect and prevent malicious threats.
Security products that protect endpoints offer features like device controls, vulnerability management, and threat hunting. If you’re looking for an alternative solution to CrowdStrike, I’ve compared popular solutions in the industry and narrowed them down to the best.
Here are the seven best alternative solutions to the CrowdStrike Falcon platform:
- Palo Alto Cortex XDR: Best for advanced security capabilities
- Trend Micro Vision One: Best for smaller teams with advanced needs
- Cybereason Defense Platform: Best for visualizing incidents and threats
- Bitdefender GravityZone: Best for small business budgets
- Sophos Intercept X: Best for basic EDR requirements
- Symantec Endpoint Security: Best for large-scale endpoint management
- SentinelOne Singularity: Best for forensics needs
Top CrowdStrike Alternatives Comparison
The following table compares a few features of CrowdStrike’s major competitors and the availability of a free trial.
| Behavioral Analytics | Device Controls | Custom Detection Rules | Free Trial | |
|---|---|---|---|---|
| Palo Alto Cortex XDR | ➕ | ✔️ | ✔️ | ❌ |
| Trend Micro Vision One | ✔️ | ✔️ | ✔️ | 30 days |
| Cybereason Defense Platform | ✔️ | ✔️ | ✔️ | ❌ |
| Bitdefender GravityZone | ✔️ | ✔️ | ✔️ | One month |
| Sophos Intercept X | ✔️ | ✔️ | ❌ | 30 days |
| Symantec Endpoint Security | ✔️ | ✔️ | ✔️ | ❌ |
| SentinelOne Singularity | ✔️ | ✔️ | ❌ | 7 days |
✔️ = yes ❌ = no ➕ = add-on
While these solutions are the best in the endpoint detection market, I found that Trend Micro Vision One was the best overall platform to replace CrowdStrike Falcon.
Continue reading to learn more about these products, or skip down to see how I evaluated the best EDR alternatives to CrowdStrike.

Trend Micro Vision One – Best for Smaller Teams With Advanced Needs
Overall Reviewer Score
4.2/5
Pricing
3/5
Core features
4.9/5
Advanced features
3.3/5
Ease of use and administration
5/5
Customer support
4/5
Trend Micro Vision One is a unified security platform for businesses of all sizes. With features like remediation suggestions and customized playbooks, it’s designed to protect the entire security infrastructure.
Trend Micro has been consistently building its security business for years, and Vision One is proof of that. It has functionality for both large enterprises and SMBs. Like CrowdStrike, Vision One is designed to cover multiple facets of business security.
Pros
Cons
- Contact for quote: Custom pricing available
- Free trial: 30 days
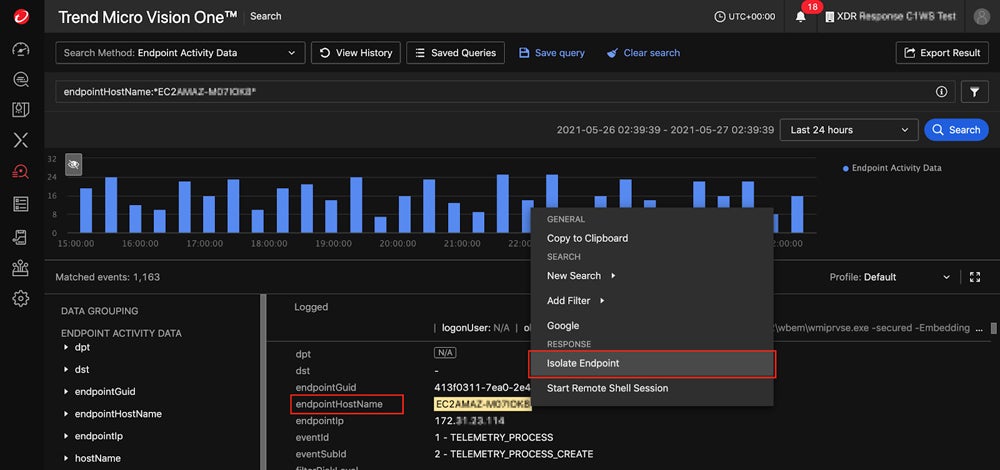
- Attack surface discovery: Vision One tracks down unknown assets and attack surfaces that have yet to be scanned and protected.
- Vulnerability management: The platform shows admins data like commonly exploited vulnerabilities and legacy operating systems being used.
- Risk scores: Trend Micro uses global threat intelligence sources to help determine which vulnerabilities are the most critical and should be fixed first.
- Various response options: Vision One can isolate endpoints, terminate processes, send threats to a sandbox, and force users to reset their passwords.
Vision One is a great solution for teams that want a comprehensive security platform. Still, some of its endpoint security features are unclear, including rogue device discovery and incident triage. If these are big priorities for you, consider Cybereason instead.

Palo Alto Cortex XDR – Best for Advanced Security Capabilities
Overall Reviewer Score
4/5
Pricing
2.4/5
Core features
4.4/5
Advanced features
3.5/5
Ease of use and administration
4.8/5
Customer support
4/5
Palo Alto Cortex XDR is a highly advanced security platform for protecting endpoints across your business infrastructure.
Palo Alto Networks is renowned for its excellent security — it recently posted perfect scores in the MITRE ATT&CK evaluations — and, like CrowdStrike, it offers advanced features like custom detection rules and incident triage.
I recommend Palo Alto for experienced teams that need top-notch security and can manage a large platform.
Pros
Cons
- Contact for quote: Custom pricing available; some pricing information available from Amazon Web Services
- Free demo: Contact to schedule
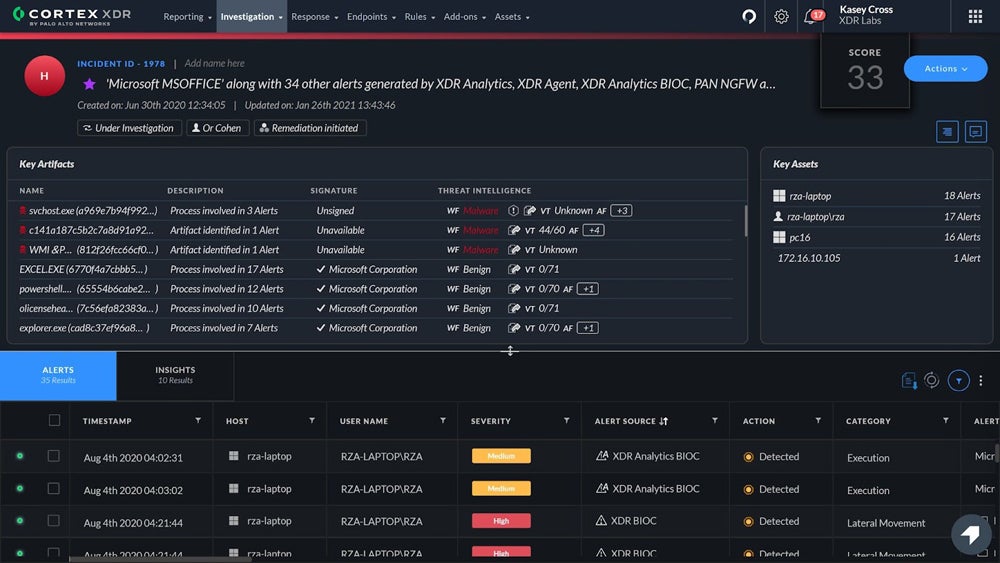
- Forensics: Cortex XDR investigates incidents involving endpoints even when they aren’t connected to the network.
- Root cause analysis: Palo Alto allows admins to examine the root causes of incidents and the sequence of events leading to them.
- Behavioral analytics: The platform analyzes threat trends and malicious behavior to detect malicious insider attacks and credential abuse.
- Incident prioritization: Cortex XDR prioritizes fixing incidents by grouping alerts and scoring the incidents.
Although Palo Alto Cortex XDR is a great security solution for enterprises, it will take less experienced teams significant time to learn and use it effectively. If you need an easier-to-use platform, look at Sophos instead.

Symantec – Best for Large-Scale Endpoint Management
Overall Reviewer Score
3.9/5
Pricing
2.2/5
Core features
4.4/5
Advanced features
5/5
Ease of use and administration
4.4/5
Customer support
2.6/5
Symantec Endpoint Security and Symantec EDR, recently acquired by Broadcom, offer broad endpoint and server management. Features include custom detection rules and suggestions for remediation.
Symantec is designed to protect data centers, hybrid infrastructures, and storage solutions like cloud buckets and network-attached storage. Like CrowdStrike, Symantec offers managed security services.
Pros
Cons
- Contact for quote: Custom pricing available
- Device controls: Security teams can develop rules to control peripheral devices like USBs connecting to endpoints within the infrastructure.
- Attack visibility: Symantec EDR shows you the attack chain of events during an incident, which you can sort chronologically and then perform remediations.
- Managing assets: The endpoint management solution’s asset relationships and software license management help teams better visualize their organization’s hardware and software.
- Custom rules: You can add your own incident detection rules to find threats that Symantec’s existing rules don’t already cover.
While Symantec is a strong endpoint security solution, some customers complained about customer support responsiveness after the Broadcom acquisition. Consider Sophos if you’re seeking a solution with high customer service reviews.

Sophos Intercept X – Best for basic EDR requirements
Overall Reviewer Score
3.9/5
Pricing
3.6/5
Core features
3/5
Advanced features
3.7/5
Ease of use and administration
5/5
Customer support
4.3/5
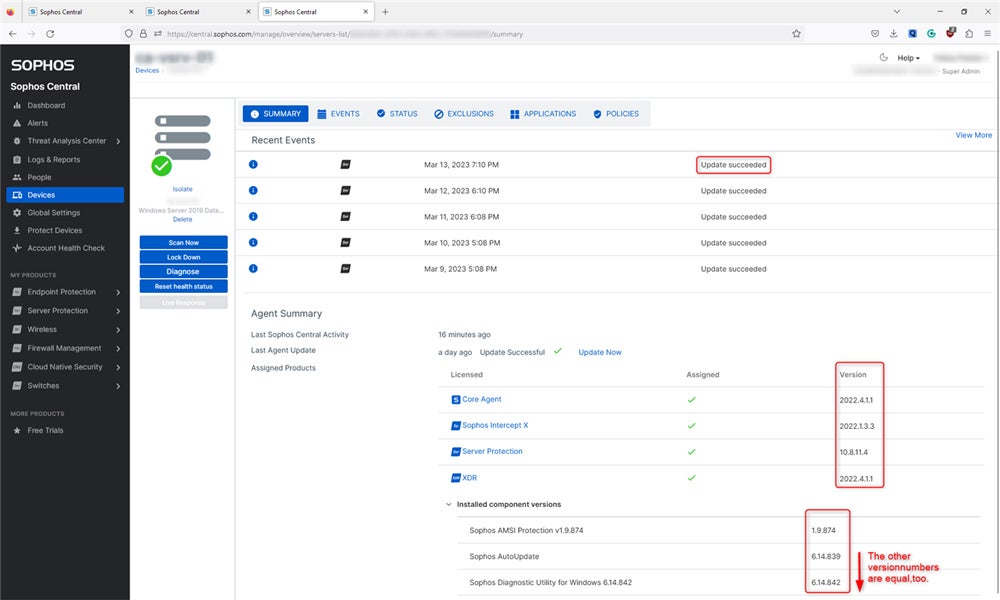
Sophos is an extremely popular network security and EDR provider. It offers tools for managing endpoints, such as application and peripheral device control. Renowned for its usability, Sophos is a strong solution for SMBs and less experienced teams, though it provides features like data loss prevention for larger companies.
While CrowdStrike is an advanced platform, Sophos is ideal for teams that need a basic but strong EDR foundation.
Pros
Cons
- Contact for quote: Custom pricing available
- Free trial: 30 days
- Free demo: Contact to schedule
- Prioritized detection: Intercept X uses artificial intelligence to prioritize which threats to detect.
- Web protection: Sophos examines web pages and data like IP addresses and blocks user access to malicious sites when needed.
- Behavioral analysis: The platform gathers process, registry, and file event data over time to determine threats versus normal activity.
- File integrity monitoring: Sophos protects Windows servers by identifying changes to the critical files on the servers.
Sophos is an outstanding solution for smaller teams and more basic EDR requirements, but it might not have enough advanced features for large enterprises. If your team needs more functionality, consider Palo Alto instead.

SentinelOne – Best for Forensics Needs
Overall Reviewer Score
3.7/5
Pricing
3.7/5
Core features
3.7/5
Advanced features
4.8/5
Ease of use and administration
3/5
Customer support
3.8/5
SentinelOne Singularity is a detection and response platform with vulnerability management and mobile device support capabilities.
SentinelOne’s RemoteOps Forensics solution belongs to the Singularity Platform and is a good choice for security teams that particularly want to focus on forensics. It offers features like automated evidence collection and custom forensic profiles. Like CrowdStrike, SentinelOne has multiple partnerships with other security vendors, including Okta and Zscaler.
Pros
Cons
- Singularity Core: $69.99 per endpoint; unspecified period of time
- Singularity Control: $79.99 per endpoint
- Singularity Complete: $179.99 per endpoint
- Singularity Commercial: $229.99 per endpoint
- Singularity Enterprise: Contact for quote
- Free trial of Singularity Control: 30 days
- Free demo: Contact to schedule
- Custom detection: Admins can create custom rules to detect specific threats to their systems or overall industry.
- Device control: Singularity allows customers to manage endpoints like USB and Bluetooth and discover unmanaged devices on their network.
- Forensic data collection: You can use RemoteOps Forensics to collect potential evidence when SentinelOne detects a threat automatically.
- Threat hunting: WatchTower, a SentinelOne service, provides 24/7 threat hunting and attack surface assessments.
Although SentinelOne is a great choice for teams that want a large platform and plenty of features, it doesn’t have live chat support. If that’s a priority for your team, consider Sophos instead.

Cybereason – Best for Visualizing Incidents & Threats
Overall Reviewer Score
3.7/5
Pricing
2.2/5
Core features
3.8/5
Advanced features
4/5
Ease of use and administration
4.2/5
Customer support
3.8/5
Cybereason is an enterprise-grade detection and response platform ideal for larger teams, though it can also benefit SMBs with a sizable budget.
One of its differentiating features is the MalOp, or malicious operation, tracking individual threats and all associated data. If you’re looking for a strong managed defense platform similar to CrowdStrike, Cybereason is a great choice, particularly for threat visualization.
Pros
Cons
- Custom pricing available: Contact Cybereason for a quote or purchase from resellers
- Free demo: Contact to schedule
- Endpoint control: Within a single interface, admins can set rules for specific endpoints based on their business’s security policies.
- Threat intelligence: Cybereason compares multiple threat feeds using machine learning-based analysis to determine the most helpful feeds.
- Remediation assistance: The Defense Platform shows admins which tools threat actors use and helps them quickly block threats and isolate malicious files.
- Integrations: Technology partners of the Cybereason Defense Platform include Okta, Proofpoint, Fortinet, and Palo Alto.
Cybereason is a strong choice for large enterprises and security teams that want to visualize the connections between different events. However, it’s not the best choice for small teams; consider Bitdefender instead if your business needs something simpler.

Bitdefender GravityZone – Best for Small Business Budgets
Overall Reviewer Score
3.7/5
Pricing
4.6/5
Core features
3.3/5
Advanced features
2.8/5
Ease of use and administration
4.2/5
Customer support
3.6/5
Bitdefender GravityZone is a multi-purpose security platform for small businesses and enterprises. You can choose your GravityZone package based on your needs; the most basic plan truly is an SMB solution, with features like web control and filtering.
However, the enterprise option offers plenty for large and experienced teams, like correlation across endpoints and response suggestions. Like CrowdStrike Falcon, GravityZone provides pricing for small teams.
Pros
Cons
- 100 devices: $4,000-$5,800 per year
- More than 100 devices: Contact for quote
- Free trial: One month
- Ransomware mitigation: When GravityZone detects strange encryption procedures, it creates tamper-proof file copies to prevent data loss.
- Risk management: Bitdefender assigns risk scores to individual threats and prioritizes misconfigurations and behaviors depending on criticality.
- Sandboxing: GravityZone can automatically send suspicious files or code to the Sandbox Analyzer to determine whether it’s malicious.
- Single pane of glass: GravityZone combines the whole Business Security platform into one management console, so your admins can manage everything from one location.
GravityZone is a great endpoint security solution for businesses, but it lacks a few features, including rogue device discovery and incident triage. If your security team needs those features, consider SentinelOne instead.
5 Key Features of CrowdStrike Competitors
Endpoint security platforms like CrowdStrike Falcon typically offer features such as device control, incident isolation, remediation suggestions, threat intelligence, and mobile device support.
Device Control
Endpoint security platforms typically offer device controls so teams can block or isolate devices that are seeing — or causing — security problems. This could be a strain of malware on a laptop or a mobile application trying to gain unauthorized access to a service. Admins can isolate the device so any threat won’t spread or block certain malicious processes.
Incident Quarantine
Threat actors often use lateral movement to travel through IT environments, but they can do that because of insufficient permissions and the connection points between devices and applications. Endpoint security solutions should allow admins to quarantine incidents or whole devices so that threats like malware can’t spread further.
Remediation Recommendations
Endpoint detection and response often include suggestions for remediating threats. A management console might provide threat data, such as affected applications, and then give a listed process for mitigating the threat, like quarantining it or sending it to a sandbox. These suggestions are helpful for security admins because they’re based on data that the EDR solution has already compiled, and the automation also saves the admins manual work.
Threat Intelligence
Endpoint security vendors like CrowdStrike often integrate with popular threat intelligence feeds or perform their own threat research. Security platforms like EDR and XDR need accurate sources of threat data. With a strong understanding of threats and their associated indicators of compromise, these platforms will be better prepared to combat them.
Support for Mobile Operating Systems
Ideally, endpoint security suites like CrowdStrike should cover mobile devices like phones, not just laptops and servers. Mobile phones can be just as much of a threat to enterprise security as computers, especially if they’re connected to a business network or are used to store sensitive data. Often, security platforms like EDR cover Android and iOS.
Flaws in mobile devices aren’t the only threats to business networks. Our guide explains major network security threats, including malware and denial of service.
How I Evaluated CrowdStrike’s Main Competitors
To analyze the best alternatives to CrowdStrike Falcon, the vendor’s main platform, I created a product scoring rubric that analyzed solutions in the endpoint security, EDR, and XDR spaces. The rubric included six major categories that buyers look for in endpoint security solutions. Each category had its own weight, and each also included multiple subcriteria. How well each security product met the subcriteria and their weighting contributed to their final score.
Evaluation Criteria
I started with core endpoint security features like device controls when creating the rubric. Then, I looked at usability and administrative features, like documentation and training videos. Next, I considered pricing, which included free trials, and advanced features, such as threat hunting. Finally, I scored the products based on customer support options, including the availability of demos.
- Core features (30%): This category included the most important endpoint security features, like vulnerability management, remediation suggestions, and device control.
- Criterion winner: Trend Micro
- Ease of use and administration (25%): I evaluated usability features like documentation, APIs, and a single management console.
- Criterion winners: Trend Micro and Sophos
- Pricing (15%): I looked at the availability of pricing information, including from resellers, and evaluated free trials.
- Criterion winner: Bitdefender
- Advanced features (15%): These included nice-to-have capabilities like threat hunting and rogue device discovery, which are particularly helpful for enterprises.
- Criterion winner: Symantec
- Customer support (15%): I considered customer support channels, like phone and email, as well as product demo availability.
- Criterion winner: Sophos
Frequently Asked Questions (FAQs)
Is CrowdStrike Better Than Competitors?
The top endpoint security and EDR platforms excel in different areas, including detection, protection, threat intelligence, and research. CrowdStrike is particularly renowned for its defense capabilities.
However, multiple other providers do well in threat protection — just look for signs like strong independent testing scores; these show that vendors can actually use the features they claim to offer.
Who Is CrowdStrike’s Biggest Competitor?
CrowdStrike has plenty of competitors, but the most notable one is probably Palo Alto Networks, one of the world’s best detection and response providers. It offers similar features and earns very comparable independent testing scores. Palo Alto’s detection and response platform, Cortex XDR, is an advanced solution ideal for enterprise teams with the knowledge and experience to configure its features.
What Are the Disadvantages of CrowdStrike?
CrowdStrike isn’t available as an on-premises EDR — it’s only available in the cloud. If your business is looking for an on-prem solution, you should look elsewhere.
Some potential customers may also be thrown off by the news about CrowdStrike last year, when the vendor ran a content update that caused crashes on millions of customers’ computer systems. Regardless of that significant operational hiccup, CrowdStrike is still one of the top vendors for endpoint security.
What’s the Difference Between Antivirus, Endpoint Protection Platforms & EDR?
CrowdStrike and its competitors all offer features in the antivirus, endpoint protection, and EDR families. However, the three have distinctions, even if they’re typically combined on CrowdStrike Falcon and other platforms.
Antivirus solutions mainly protect computer systems from viruses and malware. Endpoint protection platforms prevent threats on devices like laptops, and EDR platforms combine preventative features with direct response.
Learn more about the differences between antivirus, endpoint protection platforms, and endpoint detection and response in our guide to the three.
Bottom Line: Choosing An Alternative to CrowdStrike
Whether you’re looking for your business’s first EDR platform or trying to replace an existing instance of CrowdStrike Falcon, consider the key features your team needs when evaluating competitors.
Falcon is renowned for its threat prevention capabilities, but other solutions can provide that, too. Look for strong independent testing scores that indicate actual ability, but consider administrative and support features that affect usability, too.
Is your business specifically looking for a managed endpoint security solution? Check out our guide to the best managed detection and response solutions, including Alert Logic and SentinelOne.