A cloud workload protection platform (CWPP) shields cloud workloads from a range of threats like malware, ransomware, DDoS attacks, cloud misconfigurations, insider threats, and data breaches.
CWPP solutions offer uniform visibility and management for physical computers, virtual machines (VMs), containers, and serverless applications, helping to protect resources optimized to run in a cloud-based application or service.
In addition to boosting visibility and control over cloud workloads, utilizing a CWPP enables enterprises to strengthen their security posture and lower the risk of data breaches and other security events. We’ll take an in-depth look at the top CWPP solutions, followed by buying considerations for those in the market for a cloud workload protection platform.
- AWS GuardDuty: Best for AWS users
- Check Point CloudGuard: Best for unified cloud workload protection
- Illumio Core: Best for advanced micro-segmentation capabilities
- Microsoft Defender for Cloud: Best for Azure integrations
- Orca Security: Best for advanced cloud configuration capabilities
- Palo Alto Prisma Cloud: Best for DevOps integration and container security
- SentinelOne Singularity Cloud: Best for advanced automation capabilities
- Sophos Cloud Workload Protection: Best for ease of use
- Trend Micro Deep Security: Best for hybrid cloud environments
- VMware Carbon Workload: Best for virtualized environments
- Key features of CWPP software
- How do I choose the best CWPP software for my business?
- Bottom Line: Top CWPP Solutions
Top Cloud Workload Protection Platforms (CWPP) comparison
Here’s an overview of CWPP solutions, including their supported platforms, key features, alert generation, machine learning, free trial availability, and pricing.
| CWPP | Supported Platforms | Key Features | Alert Generation | Machine learning | Free Trial | Pricing |
|---|---|---|---|---|---|---|
| AWS GuardDuty | AWS | Account- level threat detection security features, AWS services integration | Yes | Yes | Yes | $1 per gigabyte per month |
| CloudGuard Workload Protection | AWS, Azure, GCP, VMware | Vulnerability management, network security, compliance management, threat intelligence, multi-cloud environments | Yes | Yes | Yes | Check Point has not provided pricing information for this product. |
| Illumio Core | AWS, Azure, GCP, VMware | Micro-segmentation, workload visibility, policy enforcement, threat detection | Yes | Yes | Yes | $7,080 per unit subscription per year. |
| Microsoft Defender for Cloud | Azure, AWS, Google Cloud Platform | Unified CWPP and CSPM security features across all platforms, advanced threat detection, Azure integration, compliance monitoring, vulnerability assessment | Yes | Yes | Yes | Starts at $14.60 per server per month. |
| Orca Security | AWS, Azure, GCP | Cloud configuration capabilities, vulnerability scanning, malware detection, data leak prevention | Yes | Yes | Yes | Orca has not provided pricing information for this product. |
| Prisma Cloud by Palo Alto | AWS, Azure, GCP | DevOps integration, Compliance monitoring, network security, container security, data loss prevention | Yes | Yes | Yes | Starts at $9,000 annually per 100 Business Edition credits. |
| SentinelOne Singularity Cloud | AWS, Azure, GCP | Advanced automation capabilities, Asset discovery, vulnerability management, runtime protection, threat intelligence | Yes | Yes | Yes | Starts at $36 per vm/kubernetes worker node, per month. |
| Sophos Cloud Workload Protection | AWS, Azure, GCP | User-friendly interface, Malware protection, web security, data loss prevention, behavior analytics | Yes | Yes | Yes | Sophos Cloud Workload Protection has not provided pricing information for this product. |
| Trend Micro Deep Security | AWS, Azure, GCP, VMware | Intrusion prevention, anti-malware, file integrity monitoring, log inspection, hybrid cloud environments | Yes | Yes | Yes | $0.01 per host per hour |
| VMware Carbon Black Workload | AWS, VMware | Application control, change management, device control, threat intelligence, virtualized environments security | Yes | Yes | Yes | VMware has not provided pricing information for this product. |

AWS GuardDuty
Best for AWS service users
Amazon GuardDuty is a cloud security solution that detects threats to your AWS services using machine learning. It continuously monitors your Amazon Web Services accounts and workloads and provides comprehensive security findings for visibility and mitigation.
GuardDuty combines machine learning, anomaly detection, network monitoring, and malicious file identification with AWS and third-party sources to help safeguard workloads and data on AWS. GuardDuty collects data from a variety of sources, including AWS CloudTrail logs, VPC Flow Logs, DNS Logs, Amazon S3 Logs, Amazon EC2 Logs, and AWS Config. Data is collected in near real time, which allows GuardDuty to detect threats quickly. It then uses machine learning to analyze the data that it collects. GuardDuty generates alerts for any potential threats that it identifies. These alerts are sent to the user so that they can investigate and take action to remediate any security issues if there is a legitimate threat.

Pricing
- The default level of service coverage starts at $1.00 per gigabyte per month.
- Pricing varies by data source, region, and changes in your workload-related AWS activity.
- AWS offers different pricing options calculated here.
Features
- Offers a fully managed service that saves you time and resources, with no need to install or manage any hardware or software
- Provides a wide range of threat detection
- Uses machine learning to analyze data
- Generates alerts for any potential threats it identifies
- Allows users to remediate issues by updating security policies, changing passwords, or disabling an account
Pros
- Works best with other AWS resources
- Can detect a wide range of threats, including malware, ransomware, data breaches, denial-of-service attacks, insider threats, and cloud misconfigurations
- Easy to use, as it allows the user to create and manage GuardDuty policies using the AWS Management Console or the AWS Command-Line Interface
- Cost-effective; customers can only pay for the resources that they use
Cons
- Not capable of detecting all threats; AWS GuardDuty should be used with other security detection systems
- It can generate false positives
- Only supports AWS-native environment
- Patching and mapping are not done automatically after alerts are sent to email

Check Point CloudGuard Workload Protection
Best for unified cloud workload protection
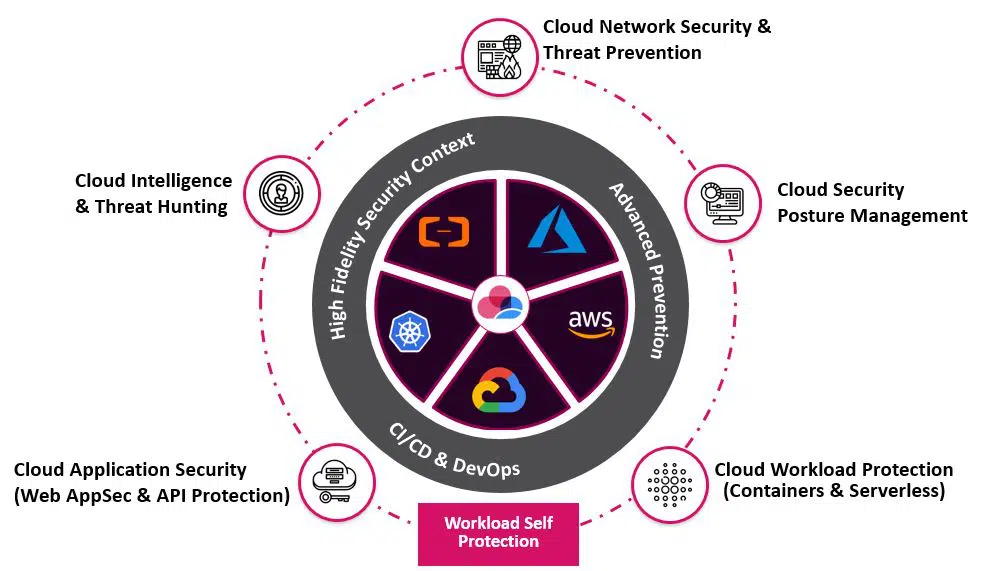
CloudGuard is a fully automated, and comprehensive cloud-native workload security solution offered by Check Point. From development to runtime, it enables unified visibility, compliance, and threat prevention across apps, APIs, and microservices including K8s containers and serverless operations.
CloudGuard Workload Protection also includes a comprehensive range of capabilities such as vulnerability monitoring, network security, compliance management, and advanced threat intelligence. Its compatibility with many cloud platforms, as well as its robust security features, make it an excellent solution for enterprises looking for full cloud workload protection.
Pricing
- Check Point has not provided pricing information for this product but you may contact Check Point sales for custom quotation.
Features
- Continuously scans and assesses cloud workloads to identify vulnerabilities and misconfigurations, allowing for proactive correction.
- By using built-in compliance templates and automated inspections, it helps maintain regulatory compliance by monitoring and fixing security weaknesses.
- Protects your cloud workloads from sophisticated assaults by detecting and blocking known and undiscovered threats.
- Supports auto-scaling.
- Regulates traffic flows and applies security regulations at the workload level through network segmentation and micro-segmentation.
Pros
- Supports several cloud platforms, including AWS, Azure, Google Cloud Platform, and VMware
- Employs advanced real-time threat intelligence and machine learning to detect and mitigate threats, as well as to block complex attacks such as malware, botnets, and zero-day threats, ensuring a quick response to new hazards
- Allows enterprises to monitor and analyze network activity for security and compliance needs by providing deep visibility into network traffic and communication patterns
- Integrates optimally with other Check Point security solutions, resulting in a comprehensive security posture throughout the organization’s network infrastructure
- Offers automation of security checks, streamlining of audit processes, and provision of compliance reports simplify compliance management
Cons
- Implementation may require training or specialized resources, as well as knowledge and understanding of network security concepts and a learning curve to effectively leverage its capabilities
- Pricing increases annually and could get expensive for enterprises
- Some users have reported experiencing a slow interface
See the Top Cloud Access Security Broker (CASB) Solutions

Illumio Core
Best for advanced micro-segmentation capabilities
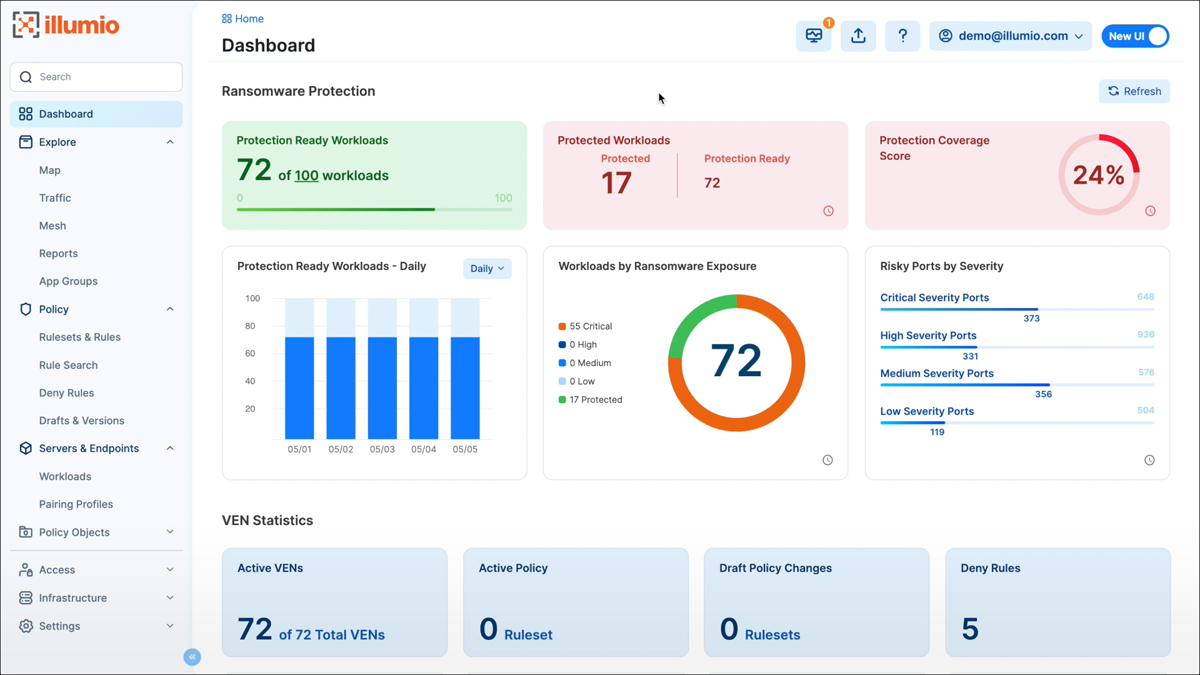
Illumio Core stands out as a strong CWPP solution, with extensive micro-segmentation capabilities, workload visibility, and real-time threat detection. It is an ideal option for enterprises wanting enhanced cloud workload protection because of its ability to provide granular security management, adapt to dynamic workloads, and simplify visibility. While there is a learning curve and some integration issues to consider, the benefits of greater security and streamlined management make Illumio Core a valuable solution for safeguarding cloud workloads in dynamic contexts.
Pricing
- Pricing of Illumio Core units starts at $7,080 per 50 protected workloads and 25 ports annually.
- Amazon marketplace also offers some pricing information.
Features
- Enables granular security control over network traffic by implementing micro-segmentation
- Provides workload visibility.
- Designs and implements security policies based on workload characteristics, decreasing the attack surface and minimizing lateral threat movement.
- Real time threat detection.
- Guarantees consistent protection as your infrastructure evolves through seamless scalability with cloud environments.
Pros
- Gives users a comprehensive perspective of cloud workloads, making visibility easier and supporting effective security management
- Adjusts security policies automatically as workloads change or migrate, ensuring continuous protection without human reconfiguration
- The micro-segmentation capabilities of Illumio Core enable fine-grained control over network traffic
Cons
- To fully utilize Illumio Core’s sophisticated features, advanced resources and training may be required, particularly when designing complicated micro-segmentation implementations
- To achieve a seamless installation, integration with existing network infrastructure may require additional configuration and coordination
Microsoft Defender for Cloud
Best for Azure integrations
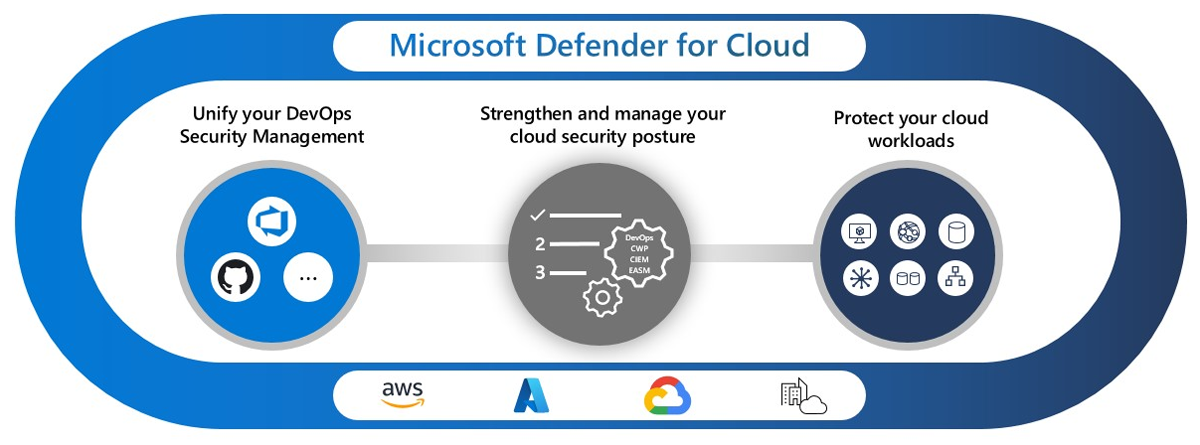
Microsoft Defender for Cloud combines advanced threat detection, vulnerability assessment, and adaptive security measures designed specifically for Azure workloads. Its native Azure integration, real-time threat intelligence, and adaptive security rules make it an excellent solution for enterprises looking for powerful cloud workload protection within the Azure ecosystem. While Microsoft Defender for Cloud’s concentration on Azure and deployment complexity may necessitate additional considerations, the benefits of leveraging Microsoft’s experience and integrated security capabilities make it an appealing alternative for securing cloud workloads.
Pricing
- Starts at $14.60 per server per month. Explore Microsoft Azure’s different pricing plans here.
Features
- Advanced threat detection
- Azure integration
- Compliance monitoring
- Vulnerability assessment
- Dynamic security controls
Pros
- Dynamically adjusts security policies based on workload behavior, reducing false positives and enabling accurate threat response
- Collects and analyzes logs from various sources, allowing for in-depth investigations, threat hunting, and actionable insights into security events
- Maintains compliance with industry regulations and standards by providing compliance assessments, audit trails, and reporting capabilities
- Employs advanced machine learning and behavioral analytics to identify and block malicious activities
- Performs continuous vulnerability scans on cloud workloads, highlighting potential security weaknesses and providing recommendations for remediation
- Seamlessly integrates with Azure
Cons
- While Defender for Cloud is well-suited for Azure workloads, organizations with multi-cloud environments may require additional security solutions to cover non-Azure platforms
- Implementing and configuring Defender for Cloud may require careful planning and coordination, particularly for organizations with complex cloud architectures

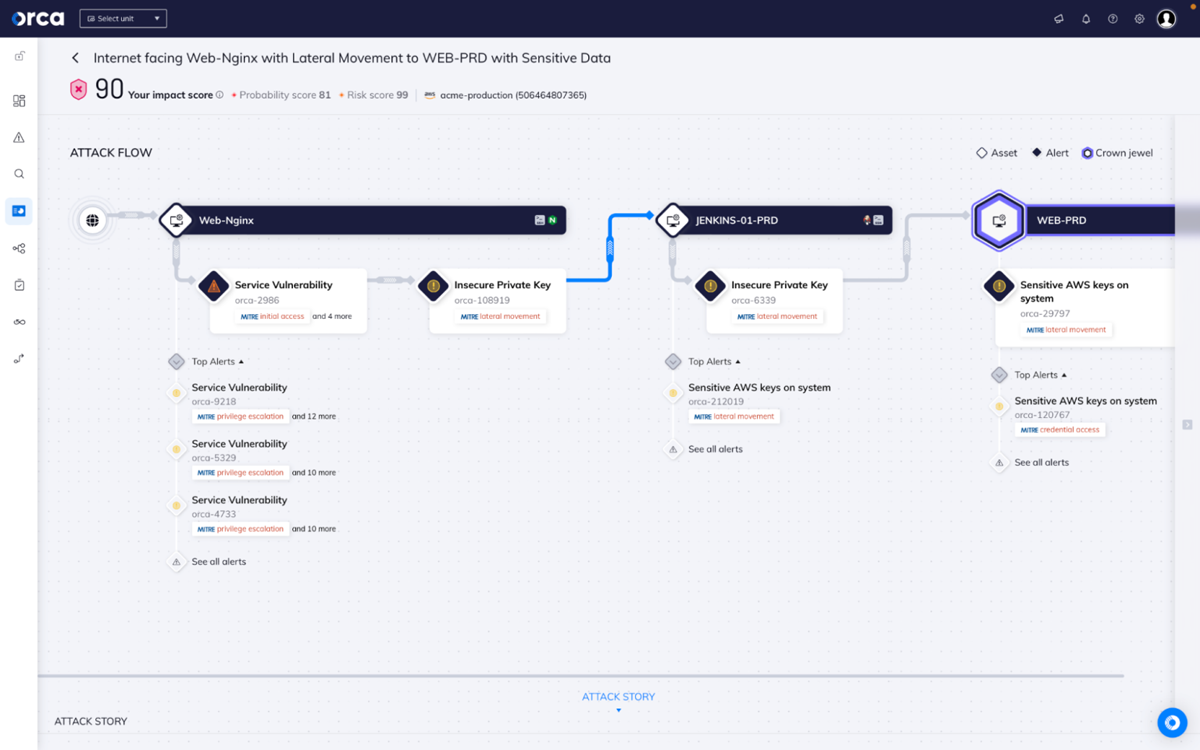
Orca Security
Best for advanced cloud configuration capabilities
Orca Security provides superior cloud configuration security, vulnerability management, and complete visibility across many cloud platforms. Its deep cloud visibility, agentless methodology, and continuous monitoring capabilities make it an appealing option for enterprises looking for comprehensive cloud workload protection. While there is a learning curve and limited network layer visibility, the advantages of better security, vulnerability management, and compliance monitoring make Orca Security an appealing solution for efficiently securing your cloud workloads.
Pricing
- Orca Security has not provided pricing information for this service but you may contact Orca Security sales for custom quotes.
Features
- Constantly checks cloud setups for misconfigurations, access control issues, and other security gaps that attackers could exploit.
- Provides thorough vulnerability scans on cloud workloads, finding potential flaws and offering actionable insights for remediation.
- Offers advanced malware detection techniques to identify known and unknown malware threats within cloud workloads, ensuring proactive detection and prevention.
- Detects sensitive data exposure and aids in the prevention of data leaks by monitoring and warning on potential data breaches in real time.
- Continuously monitors configurations and gives compliance reports.
Pros
- Delivers comprehensive insight into cloud workloads, including assets, configurations, and vulnerabilities, allowing for more effective security management
- Functions without the use of agents, which reduces deployment difficulties and resource overhead while ensuring smooth connection with cloud environments
- Allows real-time identification and reaction to security threats, minimizing possible harm and downtime through continuous monitoring
Cons
- Since Orca Security is an agentless solution, it concentrates on workload-level visibility and may offer limited network layer insights when compared to network-based security technologies
- To fully utilize Orca Security, advanced resources and training may be required, particularly when configuring complex security policies
Also read: 13 Cloud Security Best Practices for 2023

Prisma Cloud by Palo Alto
Best for DevOps integration and container security
Palo Alto Networks’ Prisma Cloud offers full cloud security, container security, compliance monitoring, and data loss prevention. Its strong DevOps integration, container security capabilities, and all-encompassing cloud protection make it a strong solution for enterprises looking for superior cloud workload security. While it may be more complex in smaller environments, the benefits of full cloud security and container protection make Prisma Cloud an appealing solution for safeguarding both cloud workloads and containerized environments.

Pricing
- Starts at $9,000 annually per 100 Business Edition credits.
- Explore Prisma Cloud by Palo Alto’s pricing guide here or visit AWS marketplace for more pricing information.
Features
- Real time compliance reporting and monitoring
- Network and container security
- Vulnerability management
- Data security and data loss prevention
- DevOps pipeline integration
Pros
- Integrates with DevOps pipelines to provide security, threat detection, and compliance checks across the software development lifecycle, allowing enterprises to create secure and compliant apps
- Provides strong cloud workload protection by including network security, container security, vulnerability management, compliance monitoring, and data loss prevention
- Provides security features that allow enterprises to detect and mitigate attacks across cloud networks and containerized environments
- Delivers real-time compliance evaluations and reports to maintain compliance with industry standards and laws
- Continuously scans cloud workloads and containers for vulnerabilities, identifying potential security flaws and delivering actionable insights for remediation
- Monitors sensitive data within cloud workloads, containers, and storage repositories to help avoid data leaks and enforce data protection regulations
- Delivers comprehensive security for containerized environments, including runtime protection, vulnerability scanning, and containerized workload configuration management
Cons
- Its extensive features may be ideal for larger or more intricate environments, whereas smaller organizations with simpler infrastructures may find it more challenging to deploy and run.
See the Best Cloud, Container and Data Lake Vulnerability Scanning Tools

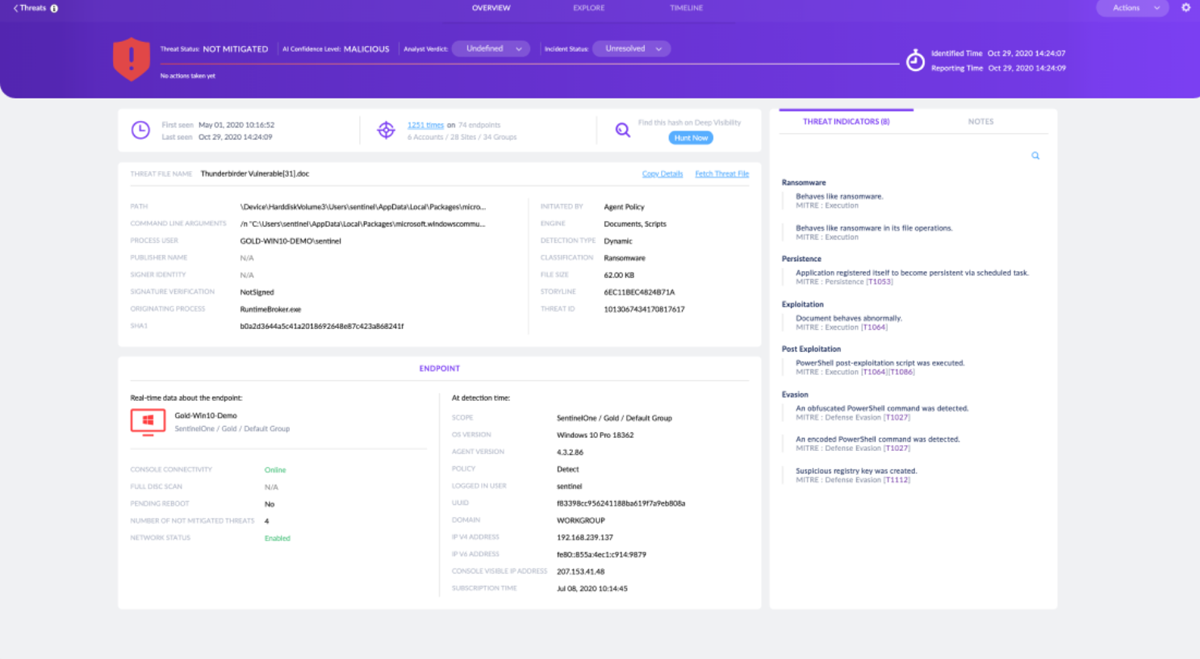
SentinelOne Singularity Cloud
Best for advanced automation capabilities
Singularity Cloud by SentinelOne focuses on simplifying runtime detection and response of cloud VMs, containers, and Kubernetes clusters for maximum visibility, security, and agility. Singularity Cloud protects against emerging cyber threats with its AI-driven strategy, scalability, and intelligent automation. The benefits of powerful threat detection, adaptive security controls, and comprehensive visibility make Singularity Cloud an appealing solution for properly safeguarding your cloud workloads, especially for organizations looking for an AI-powered CWPP solution with enhanced threat detection, adaptive security controls, and full visibility across cloud environments.
Pricing
- Starts at $36 per VM/kubernetes worker node, per month.
- Contact SentinelOne sales for custom plans and pricing.
Features
- Advanced threat detection using AI
- Provides complete insight into cloud workloads, allowing users to monitor activity, network connections, and resource use while also offering granular security controls
- Automates policy enforcement, monitors configuration changes, and generates compliance reports for various regulatory requirements
- Includes extensive automation capabilities that allow for faster security workflows, proactive threat response, and effective resource allocation
- Integrates effortlessly with common cloud platforms and third-party security products, allowing for simple deployment and expansion as needed
Pros
- Detects and responds to advanced threats using AI-driven algorithms and behavioral analytics, delivering real-time protection for your cloud workloads
- Dynamically adapts to security policies to ensure optimal security while without interfering with regulatory requirements
- Delivers efficient and dependable performance as the infrastructure expands and is built to scale with different cloud environments
Cons
- To fully utilize Singularity Cloud, advanced resources and training may be required, particularly when configuring complex security policies
- Integrating with existing cloud infrastructure and workflows may require careful planning and coordination, particularly for organizations with complex cloud architectures

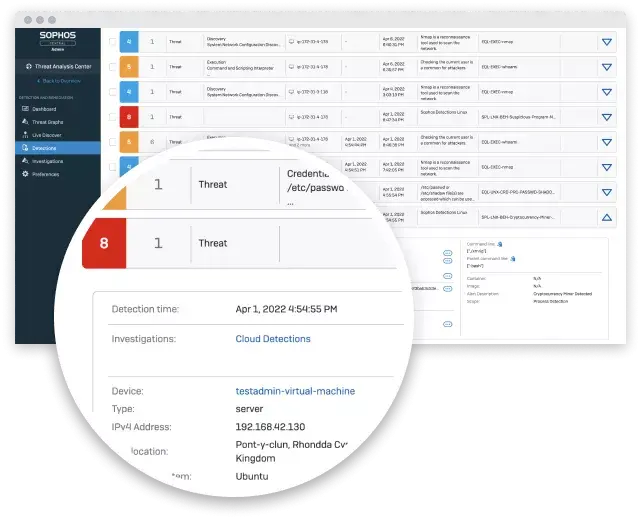
Sophos Cloud Workload Protection
Best for its user-friendly interface
Sophos Cloud Workload Protection offers efficient cloud workload protection for enterprises of all sizes through its user-friendly interface, comprehensive security features, and integration capabilities. While advanced customization possibilities are restricted and integration issues exist, Sophos Cloud Workload Protection is a tempting alternative for efficiently securing your cloud workloads due to the benefits of streamlined management, strong security capabilities, and timely threat intelligence.
Pricing
- Sophos has not provided pricing information for this product but you may visit Sophos Cloud Workload Protection for custom quotation.
Features
- Enables total visibility across hosts, containers, endpoints, networks, and cloud services with its extended detection and response (XDR) capabilities.
- Detects threats such as container escapes, kernel exploits, and privilege-escalation attempts using its cloud-native behavioral and exploit runtime detections.
- Streamlines threat investigation procedures prioritize high-risk incident detections and aggregate associated events.
- Connects hosts to a secure command line interface for cleanup through its Integrated Live Response.
Pros
- Provides a comprehensive platform for cloud workload security, including anti-malware, firewall, intrusion prevention, and web filtering
- Utilizes SophosLabs’ global threat intelligence to provide proactive detection and response to emerging attacks
- Provides a user-friendly interface and centralized administrative panel to make cloud workload deployment, monitoring, and policy enforcement easier
- Assists in adhering to industry regulations by offering compliance evaluations, reporting tools, and automated policy enforcement
- Integrates with DevOps workflows, allowing better automation, faster security operations, and improved insight into cloud workloads
Cons
- The level of customization available with Sophos Cloud Workload Protection may be limited when compared to more specialist CWPP solutions for enterprises with highly specific security requirements
- While Sophos Cloud Workload Protection provides numerous security capabilities, integration with third-party security systems may necessitate additional configuration and coordination

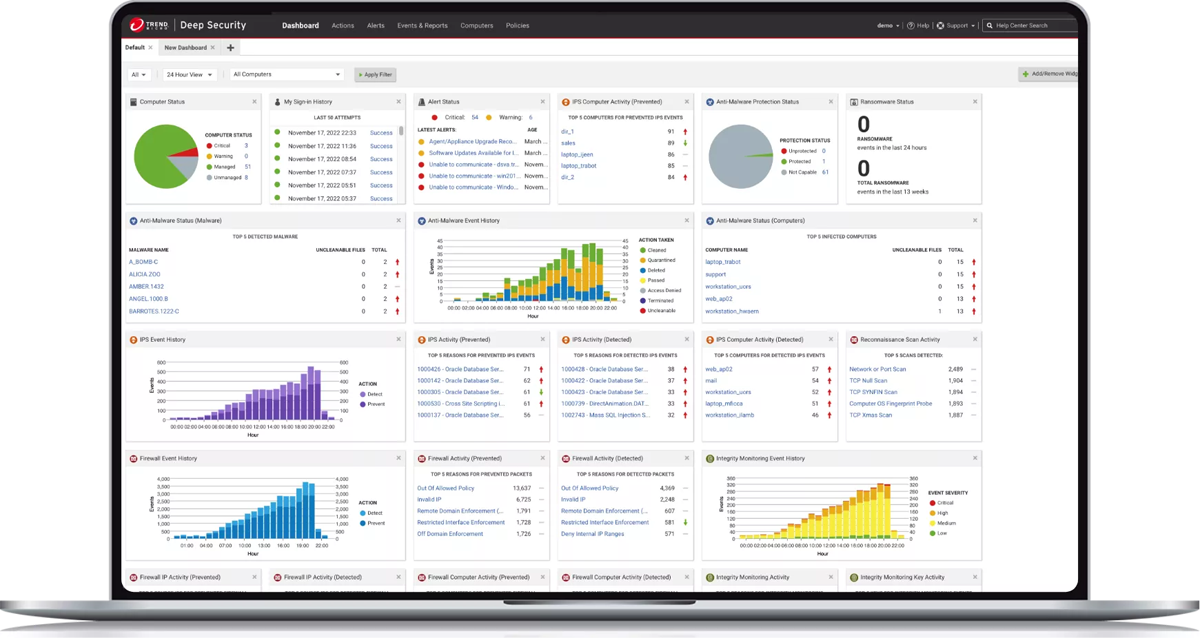
Trend Micro Deep Security
Best for hybrid cloud environments
Trend Micro Deep Security protects cloud workloads through its expanded security features, deep visibility, and automated compliance processes. While it may be more difficult to implement in smaller environments, the benefits of its robust security, real-time threat intelligence, and automated compliance management make Trend Micro Deep Security a compelling choice for those seeking enhanced cloud security.
Trend Micro Deep Security provides complete workload security across hybrid cloud environments such as private and public clouds. The platform’s advanced security capabilities, such as host-based intrusion prevention, firewall, anti-malware, and vulnerability management, can be systematically integrated across numerous cloud environments, ensuring consistent protection and compliance. Trend Micro Deep Security also offers centralized visibility and administration, allowing businesses to safeguard and monitor their hybrid cloud workloads from a single interface. Its adaptability and support for hybrid cloud architectures make it a good choice for businesses that utilize a mix of deployment methodologies.
Pricing
- Trend Micro has not provided pricing information for this service, but you may contact their sales team for custom quotation.
- Alternatively, AWS Marketplace provides some pricing information, which starts at $0.01 per host per hour for any micro, small, or medium unit type.
Features
- Advanced security features
- Integrations with different cloud environments
- Virtual patching
- Real time threat detection and response
- Automated compliance monitoring
- Continuous vulnerability scans
- Granular cloud workloads visibility
Pros
- Trend Micro Deep Security comes with a comprehensive set of security capabilities that offer complete protection against a wide range of threats
- The platform offers speedy upgrades and proactive defense against emerging threats by leveraging Trend Micro’s massive threat intelligence network
- The software automates compliance management procedures, saving time and assuring compliance
- Well-suited for hybrid cloud environments
Cons
- Advanced resources and training may be required to fully utilize it, particularly when implementing more complex security policies
- Integrating with existing cloud infrastructure and operations may require more resources and skills, especially for enterprises with complicated cloud environments

VMware Carbon Black Workload
Best for virtualized environments
VMware Carbon Black Workload provides comprehensive protection for enterprises looking to protect their workloads thanks to its granular application control, real-time threat prevention capabilities, and seamless integration with the VMware ecosystem. The scalability and flexibility of VMware Carbon Black Workload make it well-suited for virtualized environments that frequently demand dynamic resource allocation and administration. It can adapt to changing virtualized workload demands and integrates simply into existing virtualization infrastructure.
Carbon Black Workload’s key features, such as application management, real-time attack protection, and file integrity monitoring, make it an excellent choice for organizations looking for strong security and application control in their virtualized environments, as it provides comprehensive protection for virtual machines while also assisting in the security and integrity of the entire virtualized infrastructure.
Pricing
- VMware has not provided pricing information for this product but you may contact their sales team for custom quotes.
Features
- Secures virtualized workloads, containers, and cloud instances, shielding critical assets from threats and vulnerabilities.
- Employs sophisticated behavioral analysis and machine learning to detect and prevent malicious activities in real time, resulting in proactive threat mitigation.
- Detects and prioritizes vulnerabilities within workloads, allowing companies to implement patches and remediation steps more effectively.
- Assists organizations in complying with industry laws by providing continuous monitoring, policy enforcement, and reporting capabilities.
- Has a single management panel that enables businesses to streamline security operations and better manage their virtualized and cloud environments.
Pros
- VMware Carbon Black Workload is designed to be resource-efficient, with minimal impact on virtualized environment performance
- Optimizes security operations and provides scalable protection by leveraging the underlying virtualization technology
- VMware Carbon Black Workload includes comprehensive security protections intended specifically for virtualized and cloud workloads, providing greater protection against modern attacks
- Uses advanced analytics and behavioral analysis to detect and prevent attacks in real time, enabling proactive response and mitigation
- Carbon Black Workload, as part of the VMware ecosystem, works seamlessly with other VMware products, delivering a streamlined and efficient security management experience
Cons
- To fully utilize the advanced features of VMware Carbon Black Workload, it may require some initial familiarization and training
- User interface differs from other CWPP vendors and thus may require training for users familiar with other platforms
Key features of CWPP tools
Cloud workload protection platforms typically include a number of features for protecting cloud workloads, assets and data. These include:
Cloud Platform Integration
To enable seamless security management and protection across cloud workloads, CWPP products integrate with multiple cloud platforms and services such as AWS, Azure, and Google Cloud. This connection improves visibility, administration, and security control over cloud-deployed workloads. It enables businesses to use native cloud security services and APIs to ensure complete security and streamline security operations.
Incident Response and Management
This feature lets security teams detect and mitigate security breaches, conduct forensic analysis, and collect evidence for investigations. Among these capabilities are: real-time alerting, threat intelligence integration, and incident management workflows.
Data Security
Data security is a crucial component of any CWP platform. To protect data from unwanted access, exfiltration, or data leakage, a good CWP platform should include features such as encryption, data loss prevention (DLP), and access controls. These safeguarding measures ensure that data is secure at all times, both at rest and in transit, reducing the risk of data breaches and unauthorized access.
Workload Visibility
Workload visibility is essential for effective security management. CWPP tools should offer comprehensive visibility into workloads running in the cloud. Insights about workload configuration, software inventory, network connections, and user access permissions are all part of this. This visibility enables security teams to monitor and detect anomalies, illegal activity, and potential security threats, boosting their capacity to respond to and mitigate risks as soon as possible.
Automation
Automation is a significant element of CWP platforms, allowing security teams to reduce time by automating repetitive processes such as vulnerability scanning and incident response procedures, as well as providing unified security policy administration. Automation reduces manual labor, accelerates security operations, and maintains consistent security across workloads. It also enables enterprises to respond quickly to security problems and maintain a solid security posture.
Compliance
Compliance with industry standards and regulatory requirements is critical for organizations. This includes capabilities like security configuration assessments, auditing, and reporting to guarantee that security and compliance regulations are followed. This aids in the monitoring and enforcement of security measures, the generation of compliance reports, and the facilitation of audits.
Learn more about Cloud Workload Protection
How Do I Choose the Best CWPP Software for My Business?
Choosing the best cloud workload protection platform software for your business requires careful consideration of a number of factors. By carefully examining these components and conducting rigorous assessments, you will choose the CWPP product that aligns with your business needs and best meets your company’s cloud workload protection requirements.
- Determine your business’ specific needs. Examine your company’s demands and determine the unique requirements for safeguarding cloud workloads. Consider workload kinds, cloud platforms used, regulatory needs, and security challenges. Check if these key features and capabilities align with your requirements:
- Check the compatibility with your cloud infrastructure. Ensure that the CWPP software works with your current or future cloud platforms and services. Check to see if it supports the workloads you have, such as virtual machines, containers, or serverless functions.
- Examine each CWPP solution’s security features and capabilities. Consider capabilities such as workload visibility, vulnerability management, intrusion detection and prevention, data security, compliance management, and incident response. Based on your security requirements, prioritize features.
- Consider the CWPP software’s scalability and performance. Make sure it can handle your task volume and can scale as your firm grows. To minimize disturbance, assess its influence on workload performance.
- Examine the CWPP software’s user interface and ease of use. Look for user-friendly dashboards, detailed reporting, and centralized administration capabilities. Consider the amount of expertise required to manage the software and make sure it matches the abilities and resources of your team.
- Examine how well the CWPP software integrates with your existing security architecture and technologies. Look for integration options with other solutions, such as SIEM systems, threat intelligence feeds, or identity and access management platforms.
- Investigate and assess available CWPP solutions. Conduct extensive research on CWPP software suppliers and analyze the available options. Look for trusted providers who have a track record of providing efficient cloud security solutions and have favorable client evaluations.
- Shortlist a few CWPP solutions and run a trial. This allows you to test the software’s operation and evaluate its efficacy in meeting your specific security requirements in a controlled environment.
- Consider the pricing and license structure of the CWPP software. Check to determine if it fits your budget and if the pricing is reasonable in comparison to the features and value provided. Determine any additional costs, such as support and maintenance fees.
- Research the vendor’s reputation and customer service. Choose a vendor who provides timely technical support, regular updates, and a strong commitment to customer success; user reviews and your peer network can help here. Consider the vendor’s financial health and long-term viability.
- Consider broader cloud security solutions. Cloud native application protection platforms (CNAPP) have emerged as a new generation of cloud security tools and combine a range of cloud security tools and functions such as cloud workload protection platforms (CWPP), cloud security posture management (CSPM), cloud infrastructure entitlement management (CIEM), Infrastructure-as-Code (IAC) scanning and more, for organizations with needs that go beyond cloud workload protection.
Frequently Asked Questions (FAQs)
What Is a Cloud Workload Protection Platform (CWPP)?
A CWPP (cloud workload protection platform) is a security system designed specifically to protect cloud workloads. It provides comprehensive security controls and capabilities to protect cloud workloads from a wide range of attacks, vulnerabilities, and unauthorized access.
Why Should You Use a Cloud Workload Protection Platform?
A CWPP tool provides capabilities like workload visibility, vulnerability management, intrusion detection, and data security to help protect cloud workloads from threats, vulnerabilities, and unauthorized access. Using a CWPP solution can help you improve your overall security posture and ensure consistent security across cloud platforms and hybrid environments.
Do I Still Need a CWPP Tool if My Cloud Provider Offers Built-in Security Services?
The short answer is yes. While cloud providers offer native security services, a CWPP solution can add an extra layer of security, customization, and management tailored to your specific workload security needs. It ensures a comprehensive and integrated approach to securing cloud workloads, mitigating risks, and protecting critical assets thus providing you a holistic security management. Cloud security issues often involve misconfigurations and vulnerabilities in the way users connect to the cloud – controlling these risks is the essence of cloud security.
Also read: Zero Trust: Can It Be Implemented Outside the Cloud?
How We Selected the Top CWPP Solutions
We looked for top CWPPs that provide the best possible combination of security features, scalability, ease of use, integration and support, automation, and compliance, as well as price, reputation, and client feedback. We analyzed CWPP vendors using multiple data points and product features, including sources such as vendor documentation, analyst reports, security data and user reviews.
Bottom Line: Top CWPP Solutions
The cloud security shared responsibility model means users have more responsibility for security than they may realize. While cloud services providers have a strong record when it comes to cybersecurity, misconfigurations and mistakes by users are typically the source of cloud data breaches. Hardening workload protections and connections is the fastest way to improved cloud security.
Read next: 10 Top Cloud Security Companies




