Cyber reconnaissance is a process that threat actors use to find vulnerabilities and attack paths. During reconnaissance, attackers collect data about their victims and try to avoid being detected by their target’s security team or software. It’s important for your business to understand this initial step so you can detect attacks early. Secured computer systems can also use advanced detection tools to spot and block suspicious activity and even catch adversaries.
How Reconnaissance Works
To perform reconnaissance before carrying out an attack, hackers must determine how far the target network extends and collect data like open network ports, services running on the ports, and an overall map of the network. At the same time, the hackers also try to stay unnoticed during the entire reconnaissance process.
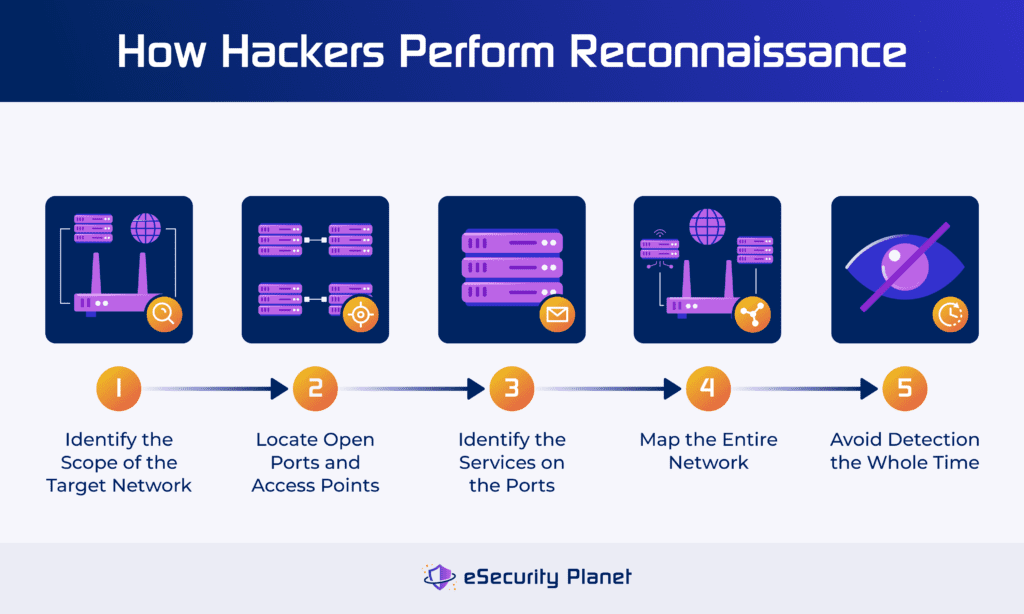
Determine the Scope of the Target Network
The individual attacking your business likely knows the scale of your network because they’ve done the research. Also, an attacker needs to determine how much ground the attack will cover. Do they plan to target the entire network, infiltrating it gradually, or do they just want to target a particular subnet? The reconnaissance process requires an attacker to get very specific about their goals so they’re more effective when they actually launch the attack.
Locate Open Ports & Access Points
When a threat actor is examining a target network, they’ll look for open ports — where network traffic isn’t being evaluated thoroughly or dropped — and catalog them. They’ll also make note of any other access points, like endpoints that aren’t properly configured or secured. Internet of Things devices often don’t support security updates, so they’re one of the weakest parts of an enterprise network’s security. Threat actors may use IoT devices as an access point.
Identify Services on the Ports
Threat actors will also want to know which services correspond with which port. This gives them a better sense of direction when developing an attack strategy. If they perform port scanning techniques and learn which service resides on a particular network port, they don’t have to waste time figuring that out during an active attack. If their initial reconnaissance is successful, this also decreases the chance of being discovered during the attack.
Map the Network
Network mapping is a useful tool for both security professionals and hackers to view the entire IT infrastructure holistically, viewing the connections between all subnets, services, and endpoints. But for a hacker, network mapping includes knowing where routers and ports reside and where they’ll need to slip past a firewall.
Read more about threats to network security, including malware, outdated products, and unsecured public networks.
Avoid Detection
Avoiding preliminary detection is one of the most critical steps of a reconnaissance strategy. Some of the longest-running cyberattacks take weeks, months, or even years of infiltrating a computer system or network, and this requires a threat actor to be stealthy that entire time.
While most hackers won’t take years to execute a reconnaissance operation, they will work to avoid being noticed by the target’s security team or any other employees. They’ll often take their time as they gather everything they need to attack a victim’s network or computer systems.
4 Types of Reconnaissance Techniques
To successfully launch an attack, threat actors need plenty of information beforehand so they don’t go in blind and avoid detection as long as possible. Popular reconnaissance techniques include collecting data, performing social engineering experiments, scanning network ports, and fingerprinting operating system activities.
Data Aggregation
Data aggregation is a broad term that encompasses all the methods a hacker gathers information about businesses, networks, computers, users, and physical premises. Common methods of aggregating data include:
- Studying the company website: One of the easiest methods of gathering data is exploring a company’s main web page and even public-facing documentation.
- Conducting employee research: LinkedIn profiles reveal data about business operations and org charts, including employee contact information.
- Exploring physical premises: Sometimes hackers will snoop around office buildings or data centers to find weak spots or observe traffic.
- Studying open-source intelligence: Open-source feeds are useful for security, but they’re also a tool for attackers to study existing vulnerabilities.
Hackers might take a few hours to gather data, or they might take years. Some compromises have occurred because an attacker stayed undetected for an extensive period of time while moving through a system before executing the final stages of an attack.
Social Engineering
Often, the process of social engineering is a form of reconnaissance because it involves gathering information like email addresses to target and learning details about an organization’s operations. Examples of social engineering include:
- Phishing: Victims receive emails or phone calls with requests for money or login credentials or receive malicious links that they’re urged to click.
- Smishing: A form of phishing sent through SMS or text, smishing is designed to trick users into making rapid decisions on their phones.
- Spear phishing: This method is typically more specific than some phishing attacks, focusing on a couple of specific individuals rather than contacting many people.
Even sending emails with malicious links can also be reconnaissance, since the attacker is exploring whether the victim will take the bait. If the victim does, the attacker then attempts to access business resources using their information. This is one key way hackers can steal your business data. If the hacker executes the attack well, the victim may not realize they’ve been phished.
Port Scanning
When hackers explore a network to gauge its security controls, they’ll often scan the network ports by sending data packets to the port and seeing what happens. Sometimes, they’ll find that the packet makes it through to the destination, but sometimes the preconfigured firewall rules will block the traffic. By performing a port scan, hackers can observe:
- Any existing firewalls: This tells them whether they’ll have to bypass an initial firewall.
- Potential network users: Attackers might be able to determine which users are in charge of a particular network service.
- Current port statuses: They’ll want to know whether each port is open or closed to traffic or if it’s filtering and blocking traffic.
Additionally, sometimes security products can pick up port scanning when the suspicious activity triggers an alert, so hackers have to be careful to remain undetected.
OS Fingerprinting
Hackers use operating system fingerprinting by reading packets that come from the computer system and trying to determine the OS’s security policies and vulnerabilities from that. While not always a reliable method of determining the system’s current status, it can be useful for observing:
- Any system weaknesses: In some cases, data packets can reveal places where an attacker could stage a successful breach.
- Potential network security policies: If attackers observe certain packets being permitted but don’t see others, they might guess that certain policies are in effect.
- Typical traffic patterns: Hackers may be able to tell when the computer system receives more traffic and when it’s more dormant.
OS fingerprinting is most effective when the hacker has already accessed the network and can observe traffic without being detected.
Active vs Passive Reconnaissance
The two major approaches to reconnaissance — active and passive — have different strategies and can both be useful for threat actors. Also, pentesters often combine these two approaches to assess vulnerabilities and prevent harmful exploitation.
Active Reconnaissance
In active reconnaissance strategies, the attackers directly interact with the targeted machines to enumerate exploitable data. Ping probes, port scanning, or traceroute are a few examples of actively hunting for routes to access sensitive resources and systems. Because active reconnaissance involves touching a system directly, it’s easier for users to figure out what you’re doing. Active reconnaissance is riskier than passive.
Passive Reconnaissance
Passive reconnaissance is the opposite: attackers don’t engage but instead collect data indirectly. This involves techniques including, but not limited to, Google dorks, open source intelligence (OSINT), advanced Shodan searches, WHOIS data, and packet sniffing. Passive reconnaissance can also include non-digital forms of snooping, such as monitoring buildings for weaknesses, eavesdropping on conversations, and stealing written credentials.
8 Ways to Protect Your Organization Against Reconnaissance
To prevent hackers from performing reconnaissance on your network, you’ll need to identify all the places where they could collect data, create network segments, and monitor and assess the network regularly. Additionally, keep your employees in the loop, use security tools that restrict network access, and tighten your security so it’s harder for hackers to perform reconnaissance techniques.
While you can follow these practices in a different order or pick and choose from the list below, we recommend performing all of them in the order given to best prepare your teams to detect and prevent reconnaissance.
Perform Some Initial Reconnaissance
One of the most important ways to protect your business from reconnaissance is by conducting it on your own network yourself. Examining traffic patterns, security policies, backdoors, unpatched vulnerabilities, IP addresses, and other data will reveal what attackers can also see and exploit.
Take a look at your website, too. Is it revealing any information that doesn’t explicitly need to be external-facing, and could that data give hackers a leg up? Examine your physical premises as well — digital backdoors aren’t the only ways a threat actor finds sensitive data. Observe the ways an individual could access your network or computers in person.
Configure Your Firewall Carefully
Make your business firewall work for you. If you’re concerned about reconnaissance, configure rules specifically designed to detect activity that could indicate packet sniffing, port scanning, and OS fingerprinting. Ensure that rules don’t contradict each other or leave gaps, because a hacker could use those weaknesses to bypass the firewall and gather more information. Carefully audit your rules to find any contradictions or open doors before finishing configuration.
Implement Network Segmentation
Segmenting enterprise networks limits attackers’ reconnaissance opportunities because they can’t move through the network as easily as they’d be able to otherwise. Configure subnets to require verification at every entrance point or application. You can set up firewalls on every subnet and set security policies that require identity verification. This significantly decreases opportunities for lateral movement and limits the data threat actors can gather.
Monitor Network Traffic & Logs
Your business’s monitoring and log management solutions should catch odd signals from traffic and users on the network. You’ll need a method of successfully analyzing it, of course, but a good monitoring tool will identify more potential reconnaissance attempts than personnel can manually find. If you don’t have a monitoring or log management system, configure one as soon as possible so you don’t miss more red flags on your network.
Sometimes, reconnaissance does cause strange traffic patterns that security teams are able to observe, but threat actors also use techniques to hide their behavior. You shouldn’t rely solely on traffic patterns to tell you that someone’s snooping. But there’ll be times when network security monitoring tools flag suspicious activity like packet sniffing.
Consider Intrusion Detection & Prevention Systems
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are often combined into one product, an intrusion detection and prevention system (IDPS). Use detection and prevention together — they’re more effective for stopping threats when operating concurrently. IDPS solutions offer threat identification features like log analysis and system monitoring, as well as threat eradication features like blocking and quarantining malicious actions.
Check out our guide to the best intrusion detection and prevention systems if your business hasn’t implemented one yet.
Deploy Vulnerability Scanning Tools
Use vulnerability scanning software to constantly look for weaknesses in your business’s IT infrastructure, including networks, important applications, and endpoints. Vulnerability scanners eliminate some of the manual work that security personnel would otherwise need to do, and they also help catch things that humans don’t always notice.
Aside from security software products, your team should stay informed about the latest vulnerabilities outlined by MITRE ATT&CK, CISA, NIST, and other reliable sources. Prioritize fixes, patch them, and apply other recommended mitigations.
If your organization needs additional help scanning for vulnerabilities automatically, check out our picks for the best vulnerability scanners for businesses.
Conduct Regular Security Assessments
Frequently assessing your IT infrastructure’s security posture is one of the best ways to see what hackers will also see. Try to look through a threat actor’s eyes — what opportunities do they have to observe traffic or find backdoors? Then document every vulnerability you find and assign a team member to address each one, even if that just means taking some preliminary steps for now.
Network and firewall audits are two useful tools for assessing how effective your network security is. If you’re looking for a deep dive into vulnerabilities, consider hiring a penetration tester. Pentesters aim to uncover every possible weakness in your network and computer systems. They might also be able to identify risks from human error, which is one of the biggest causes of breaches.
Educate Employees About Security Risks
Once your business has determined the ways you need to grow, immediately loop your employees in. This includes everyone from the CEO to the interns. Basic cybersecurity training sessions are helpful, but do your best to make them fun and memorable — the more team members understand how important security is, the more motivated they’ll be to assist you.
Make sure you have regular conversations with employees, too, down to the micro-team level. Managers should be talking about reconnaissance techniques for which their teams should be on the lookout, like suspicious emails or people sneaking around the building. Frequent discussions also discourage insider threats; employees with bad motives will be more nervous to execute an attack if security is a regular conversation topic.
Top 4 Reconnaissance Prevention Tools
Detecting reconnaissance techniques is difficult, but it doesn’t have to be impossible. I recommend using a combination of threat intelligence and deception technologies so your business can identify complex threats and trap attackers concurrently. ThreatConnect and Rapid7 ThreatCommand offer threat intelligence features, and Cynet AutoXDR and Acalvio ShadowPlex offer deception technology like honeypots.
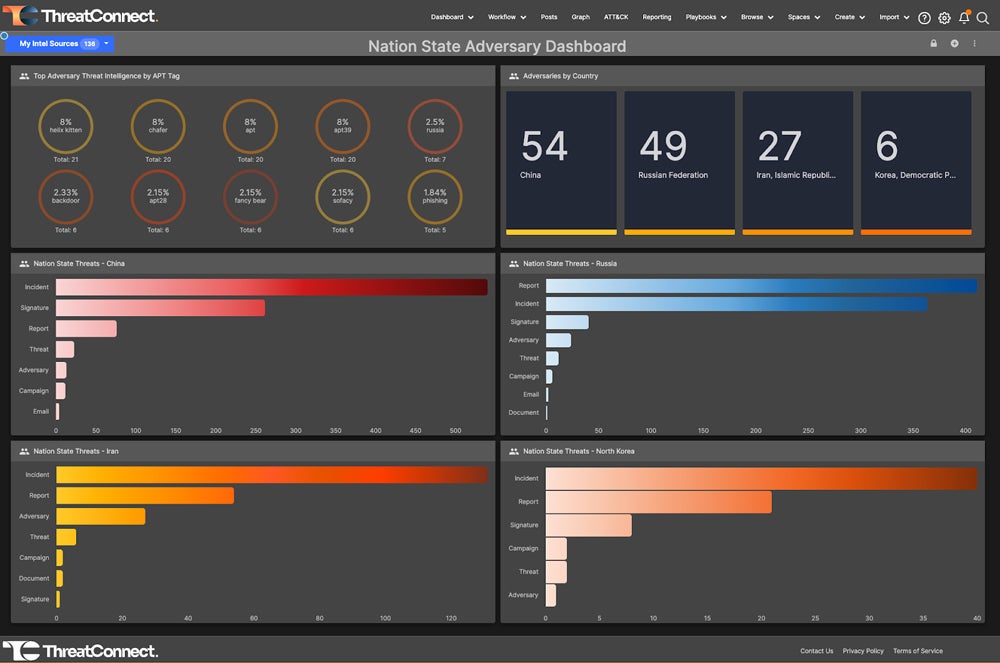
ThreatConnect (Threat Intelligence)
ThreatConnect is an enterprise-grade threat intelligence platform with multiple deployment options, including air-gapped installations. Standout features include automated alert triage and mapping discovered threats to the MITRE ATT&CK database. The platform offers integrations with Palo Alto, LogRhythm, and CrowdStrike, as well as other security providers.
ThreatConnect doesn’t make pricing publicly available, so you’ll need to contact the sales team for custom pricing. It doesn’t have a free trial, either, but you can schedule a free demo to see how the platform works.
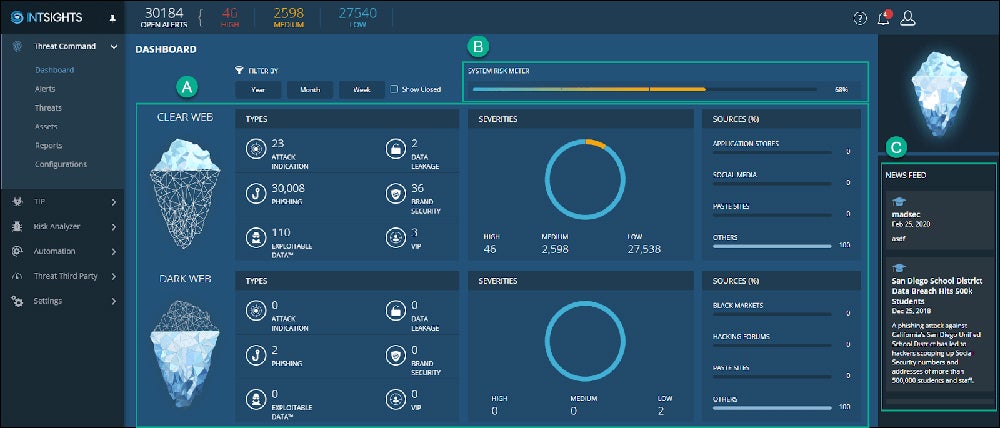
Rapid7 Threat Command (Threat Intelligence)
Rapid7 Threat Command is a threat intelligence solution for businesses that need 24/7 attention and advanced features like alert management and remediation. Its threat scoring capabilities automatically calculate a score for each indicator of compromise, based on multiple parameters. When combined with the company’s InsightIDR product — which includes EDR, SIEM, and incident response capabilities — it’s even more powerful.
Rapid7 doesn’t offer public pricing for Threat Command, but some limited pricing information is available from resellers. There’s no free trial, but you can schedule a demo with Rapid7’s sales team.
If neither of these sound like they’ll be a fit for your business, check out our full guide to the top threat intelligence platforms for more options.
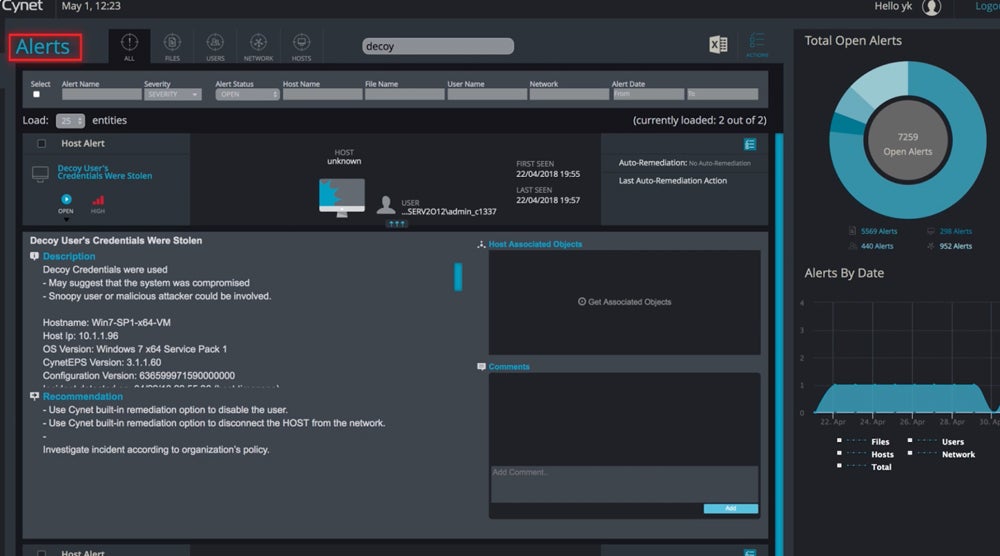
Cynet 360 AutoXDR (Deception)
Cynet’s deception technology is one component of its AutoXDR platform, an extended detection and response solution. Customers can create decoy files or use Cynet’s out-of-the-box options to trick threat actors. When a threat actor opens a file or attempts to use a decoy password, your security team receives an alert. This helps your team identify potential reconnaissance efforts before the threat actors get too far.
To get pricing details specific to your enterprise, contact Cynet’s sales team. Cynet offers a free trial for AutoXDR, but the length of the trial isn’t clear. You can also request a demo of AutoXDR.
Acalvio ShadowPlex (Deception)
Acalvio ShadowPlex is an advanced security product that offers deception for both enterprise IT environments and user identity management processes. Some of its key tools include Lures, which are misconfigured to purposely expose vulnerabilities, and Breadcrumbs, which customers deploy on already-existing business assets. ShadowPlex can be deployed on-premises or in the cloud.
Acalvio doesn’t offer its own pricing information for ShadowPlex, but some resellers provide data in their marketplaces. ShadowPlex doesn’t have a free trial; if you’re interested in seeing how it works, schedule a demo with Acalvio’s sales team.

If you’d like to look at more options, read our guide to the best deception tools in the security industry.
Bottom Line: Preventing Reconnaissance Takes Finesse
As hackers develop more sophisticated attack techniques, they go undetected more frequently. And some persistent threats go undetected for years, as the attacker gradually learns the ins and outs of the system and quietly compromises it. You’ll need equally sophisticated security solutions to stop attackers early in the reconnaissance stage, before they learn much information. Identifying reconnaissance techniques is one of your team’s best defenses.
Continue the process of protecting your business by learning how to secure your enterprise network.




