Ransomware has become a potent tool for cybercriminals looking to exploit companies’ sensitive data for profit. Ransomware attacks have affected businesses across all sizes, locations, and industries, from banking and financial services to utilities to education.
When trying to keep your business safe from potential attacks, just as important as any kind of ransomware protection solution is to understand some of the factors and signs a ransomware hacker looks for when picking their next target. These factors can include data value, geographic locations, or a company’s use of remote workers.
What Industries Are the Most Likely Ransomware Targets?
A unifying factor of most of the industries popular with ransomware attackers is their access to incredible amounts of sensitive data that an organization might want or even need to keep private, thus making them more likely to pay the ransom. Here are the most targeted industries.
Banking and Financial Services
The reasons for targeting banking and financial services companies are fairly clear. On top of having access to the capital needed to pay large ransom amounts, they often have access to extremely sensitive client information — and assets.
The world of banking and financial services is especially vulnerable to cyber attacks, and companies in this industry were the most likely to be targeted by ransomware attackers according to cybersecurity firm Trellix’s report for 2021.
Education
Education shares similar vulnerabilities to local government institutions, often lacking the resources necessary to install anti-ransomware strategies. Their access to private information from faculty and students alike also makes them appealing targets.
In recent years, education has become a popular target for ransomware attackers. 2022 research conducted by antimalware vendor Emsisoft revealed that 88 ransomware incidents were reported by institutions in the US in 2021. This led to the disruption of day-to-day operations for over 1,000 schools across the nation. In half of these incidents, personal data from both teachers and students was leaked online.
The total financial impact of these attacks can’t be known with any certainty, but, like any other industry hit by ransomware, the costs are likely severe. A Sophos report on the state of ransomware in education found that lower education institutions spent $1.58 million on ransomware in 2021. Higher education institutions spent $1.42 million.
Want to Find Out More About How to Backup Your Data in the Event of a Ransomware Attack? Take a Look at Best Backup Solutions for Ransomware Protection
Energy and Utilities
Utilities are a popular target both for attackers looking to cause damage to infrastructure and for cybercriminals looking to get paid. In a 2022 report, cybersecurity firm CyberSaint reported that 43% of energy, oil, and utilities companies hit by ransomware ended up paying the ransom.
Because they provide such critical infrastructure, energy, and utility firms are more pressured than other ransomware targets to resolve the matter as quickly as possible, which sometimes means paying the ransom, Colonial Pipeline being the most notable example in recent memory.
Government
Much like utilities, government organizations are a popular target for attackers looking to cause damage to the day-to-day infrastructure needed to keep society running. Government entities also often have some of the most sensitive data ransomware users can get their hands on.
Additionally, government organizations on the local level, such as city or county administrations, often lack the time and resources necessary to implement robust cybersecurity measures and tend to use outdated technology. In some cases, this can lead to them being especially easy targets for ransomware and result in the theft of incredibly personal data, such as land deeds and social security numbers, with less effort on the attackers’ part.
Manufacturing
Of popular ransomware targets, manufacturing companies are also the most likely to have their stolen data leaked online, with cyber criminals posting the data of 45 manufacturing companies in 2020 alone, according to Palo Alto Networks’ Unit 42. IBM reported that it resolved more cyber attacks for the manufacturing industry in 2021 than any other.
There is some good news for industrial companies, however. A 2021 survey of the industry by Sophos found that 36% of respondents were hit by ransomware attacks, and nearly half of those had their data encrypted. However, that same survey also found that only 19% of companies affected paid the ransom. This can potentially be chalked up to the fact that companies in the manufacturing industry are more prepared than other industries to restore data from backups, as decrypting stolen files rarely works.
Need to Know More About Ransomware Attackers and How They Operate? Read The Link Between Ransomware and Cryptocurrency
Key Signs and Vulnerabilities Ransomware Attackers Look For
Like any planned assault, ransomware attackers have certain vulnerabilities and factors they watch for when evaluating targets. Companies with the funds and resources to pay large sums, companies with access to sensitive data, and companies without the security infrastructure to resist a ransomware attack are favorite prey for a hacker. Understanding the key signs and vulnerabilities ransomware attackers look for is a vital part of protecting yourself against future attacks.
Valuable Data
The most important factor to ransomware attackers is the value of an organization’s data. If threat actors can steal or encrypt highly sensitive information, their victims may be more willing to pay a higher ransom. Even if they don’t receive a ransom, more sensitive data will fetch a higher price from Dark Web buyers.
You can see this preference in the types of organizations ransomware attacks have targeted recently. Professional services, financial services, and manufacturing were the most popular targets for ransomware in 2021, with energy, retail, and healthcare not far behind, according to IBM. These industries all deal with sensitive data, like financial information or personal identifiers, making them ideal targets.
Lack of Security Infrastructure
Unsurprisingly, ransomware attackers also prefer targets that lack sufficient cybersecurity measures. Small and medium-sized businesses account for half or more of ransomware attacks. These companies are less likely to have as extensive security as larger corporations, making them easier targets. There are also more businesses of that size than large corporations.
This trend may grow as ransomware-as-a-service (RaaS) expands its popularity. A growing number of ransomware groups have started franchising their tools, letting virtually anyone perform ransomware attacks for a fee. Growing RaaS use means more novice cybercriminals could engage in these attacks, and these newer attackers will likely prefer easier targets.
Companies in industries that are new to cybersecurity, like manufacturing or logistics, may fall victim to this trend. Ransomware attackers may prefer these organizations, as they’re less likely to have sufficient infrastructure to stop them.
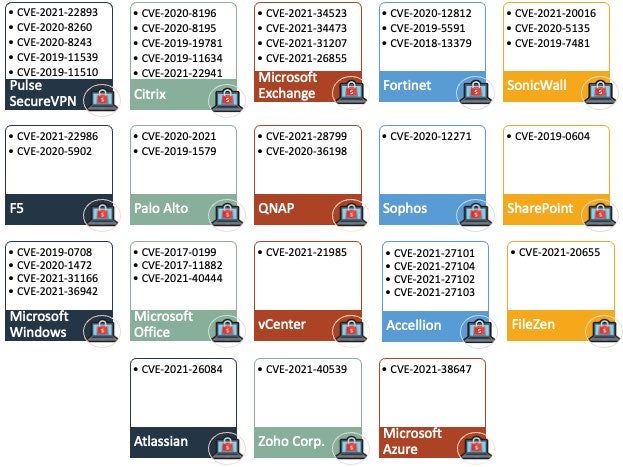
A 2021 Twitter thread looked at the most common vulnerabilities exploited by ransomware groups – and found that vulnerabilities in 18 products were the most targeted (image below). As many of these are well-known vulnerabilities, the issue of patching remains a major concern.
Money for a Ransom
Cybercriminals also typically look for targets that can pay a larger ransom. That’s why the entertainment industry, which frequently deals in multi-million-dollar projects, experienced the second-highest number of cyberattacks in 2019, according to Verizon’s 2019 Data Breach and Investigation Report. A successful ransomware attack on wealthier companies may result in a more substantial payday for the attackers, drawing their attention.
At first, this figure may seem to counter the trend of attackers targeting small and medium businesses. However, even a medium-sized business can offer a significant amount of money to an individual or small group. It’s also important to note that while SMBs are the most common targets, that doesn’t necessarily mean new businesses are.
If your business brings in at least a few million dollars in annual revenue, you could be a target. Generally speaking, the more profitable your business is, the more enticing a target you are.
Need Some Good News About Ransomware? Learn About How One Company Survived a Ransomware Attack Without Paying the Ransom
Potential for Damage
Financial motivations are not the only driving force behind ransomware attacks. Some cybercriminals seek to cause as much destruction as possible, especially in state-sponsored cyberattacks. Whether it’s to make a statement or for a feeling of power, some ransomware attackers look for targets with the highest potential for damage.
Software supply chain companies are some of the most at-risk organizations. Take the SolarWinds attack, for example, which affected scores of customers by targeting a single system, or the Kaseya attack, which put thousands of the company’s clients at risk. If you have information belonging to multiple clients or connect to many other businesses’ software, you may be an ideal target.
Software-as-a-service (SaaS) vendors are thus in some ways ideal targets. If you offer IT services to multiple other companies, a ransomware attack on your business could cause widespread damage. That potential could attract attackers.
And critical infrastructure will remain an enticing attack for those seeking to do damage. Colonial Pipeline showed just how effective such attacks can be.
Remote Workers
Amid the COVID-19 pandemic, many businesses embraced remote work. Data shows that these same companies may be at increased risk of a ransomware attack. The software you use to collaborate with remote employees may have vulnerabilities that ransomware attackers seek to take advantage of. And remote employees tend to be less protected by ransomware essentials such as immutable data backups.
Remote desktop protocol (RDP), which remote workers may use more heavily than others, is a favorite of ransomware groups. Cybercriminals leveraged RDP vulnerabilities in 47% of all ransomware attacks in one study, more than any other category.
Virtual private networks (VPNs) are another common target. While these tools can protect you by encrypting your internet traffic, unpatched vulnerabilities or outdated versions can turn them into entry points for cybercriminals. If your business uses these or similar remote collaboration tools, you could be at risk.
Zero trust is one way to secure home-based and remote workers. And enterprise firewall vendors Fortinet and Palo Alto Networks unveiled secure routers aimed at home and small office workers in 2021.
Ransomware Isn’t the Only Type of Malware You Need to Watch Out For. Read What is Malware? Definition, Purpose & Common Protections
Geographic Locations
Interestingly, recent research shows that ransomware attacks are often concentrated in specific geographic areas. In active Dark Web ransomware threads in July 2021, KELA researchers found that more than 40% of threat actors mentioned the U.S. as their desired location of victims. Canada and Australia followed, both around 37%.
This geographic concentration is likely due to the concentration of wealthier or more prominent companies. Political motivations could also play a role. Specific locations like states or cities may follow similar lines, with the largest and wealthiest areas seeing more attacks.
If your company is based in these areas, you may be at higher risk of ransomware than others. This factor is likely less influential than data value and security infrastructure, but it’s worth noting regardless.
How to Prevent Ransomware
Cybercriminals don’t act randomly. Ransomware attacks follow specific motivations, and when you understand these drivers, you can know what level of risk you face.
Regardless of how at-risk you are, protecting against ransomware is critical. However, if you fall into any of these categories, you may want to consider more extensive anti-ransomware measures.
- Data Backups: One of the best protections against ransomware is maintaining immutable backups of your data whenever possible. Decryption isn’t as consistent as it needs to be, but if you have any way to recover and restore your stolen data, you’ve removed a lot of the power ransomware attackers can have over you. However, this isn’t foolproof, as attackers might know of those backups and seek to damage them as well. Also, depending on how long it takes to deploy those backups, it might not be a feasible solution to the havoc ransomware can wreak on an organization’s day-to-day operations.
- Stop Suspicious Network Traffic: Security solutions like Intrusion Detection and Prevention (IDPS) or next-generation firewalls (NGFW) can help block potentially-malicious traffic from your network. Email gateways also have the chance of removing one of the most common vectors of ransomware infection: phishing, spoofing, and the like. EDR and SIEM systems are also core security defenses.
- Think Creatively: Deception technology could give you an early warning of ransomware or another cyberattack. Encrypting data — even in use — can take away the threat of having sensitive data leaked to the public.
- Stay Alert: Ultimately, however, these tools are only as effective as the individuals using them. As such, personal vigilance remains a key factor in preventing any malware attack. Whether it’s not opening suspicious email attachments or keeping your passwords secure, your good cybersecurity hygiene will be an effective deterrent against ransomware. This is why one of the simplest defenses against ransomware is to administer solid employee awareness training.
Need help protecting your organization from ransomware? Rapid7 offers managed detection and response (MDR) and extended detection and response (XDR) to help keep your endpoints free from ransomware. Chat with an MDR expert today.
Bottom Line
Ransomware is one of the most potent threats facing businesses today. Fortunately, knowing what ransomware hackers look for when picking their targets can help companies better prepare for an attack.
Factors such as geographic location, access to sensitive data, or lacking security infrastructure can all increase the likelihood of ransomware attacks, as well as an organization’s presence in certain industries like banking, healthcare, or manufacturing.
While there are ways to defend yourself against ransomware, none of them are foolproof, and even solid defenses are under constant threat of circumvention by enterprising hackers. Still, keeping in mind what ransomware attackers might be looking for in their targets can help you stay one step ahead of ransomware and keep your and your customers’ data safe.
Looking to Learn More About How to Defend Yourself from Ransomware? Check Out Ransomware Prevention: How to Protect Against Ransomware
NOTE: This article was originally written by Devin Partida on September 22, 2021. It was updated by Zephin Livingston on December 1, 2022.




