A sophisticated cybercrime service known as “Lucid” is exploiting vulnerabilities in Apple’s iMessage and Android’s Rich Communication Services (RCS), allowing cyberthieves to conduct large-scale phishing attacks with alarming success.
Operated by Chinese-speaking threat actors, this Phishing-as-a-Service (PhaaS) platform enables scammers to bypass traditional SMS-based security filters, making it one of the most effective phishing operations in recent years.
How Lucid turns security features against users
Typically, SMS-based phishing (or smishing) is countered by telecom providers who scan and block suspicious messages before they reach potential victims.
However, iMessage and RCS, which rely on internet-based communication rather than traditional cellular networks, offer end-to-end encryption, making it nearly impossible for providers to filter out malicious content. Lucid uses this encryption to send phishing links directly to victims’ devices, avoiding detection and increasing the likelihood of success.
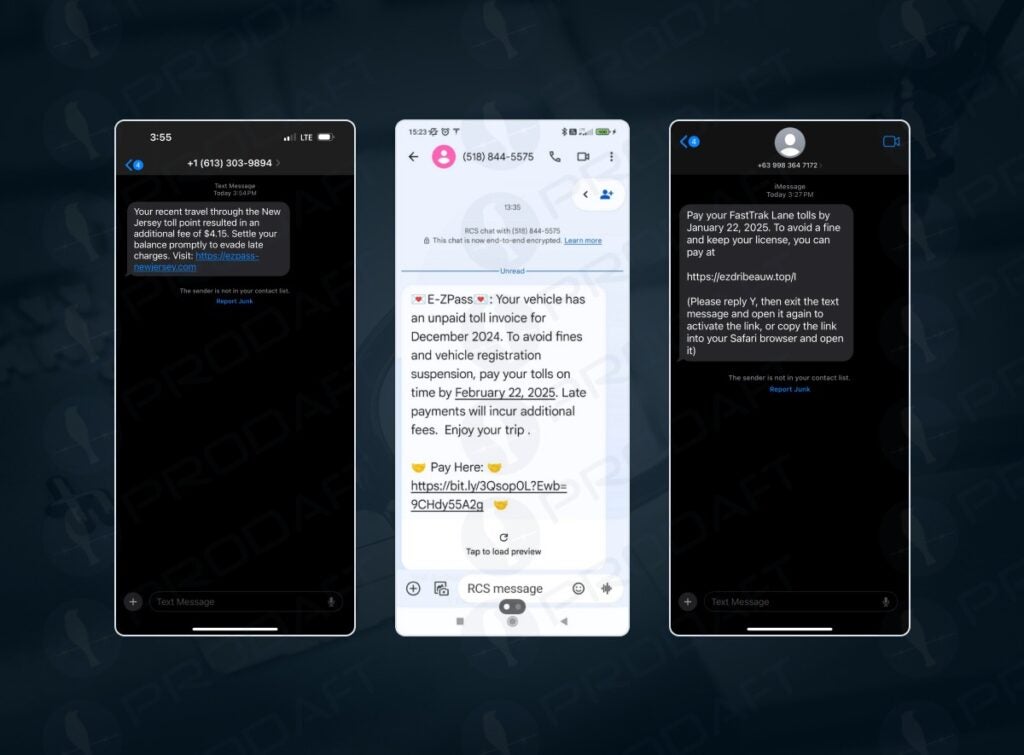
Once a victim receives a message — often disguised as an urgent notification from postal services, tax agencies, or financial institutions — they are lured into clicking a link that leads to a fake website mimicking a legitimate organization. Lucid’s operators employ several advanced techniques to make their campaigns more effective, including:
- Customizable phishing templates that replicate the branding of specific companies.
- Geo-targeting to tailor attacks based on the victim’s location.
- Time-limited, single-use URLs that prevent cybersecurity analysts from tracing phishing links after an attack is completed.
- Automated mobile farms that deploy phishing messages at scale.
A global cyber threat
Research from cybersecurity firm Prodaft indicates that Lucid has targeted victims in 88 countries, impersonating 169 organizations — including national postal services, courier companies, retailers, and government agencies. The success rate of these attacks is reportedly around 5%, far higher than the average phishing campaign, which typically struggles to achieve a 2% conversion rate.
The group behind Lucid, known as “XinXin” or “Black Technology,” is also linked to other PhaaS platforms like Darcula and Lighthouse. These services provide cybercriminals with ready-made tools to launch phishing attacks, highlighting a growing trend in the underground cybercrime economy where phishing is becoming increasingly automated and scalable.
Since early March 2024, the FBI’s Internet Crime Complaint Center (IC3) has received over 2,000 complaints about fraudulent toll payment messages. The scam has affected individuals across various states, and cybercriminals have registered more than 10,000 domains to facilitate these attacks.
Researchers found a single phishing site collected 30 credit card numbers after 550 page visits in one week. The group behind Lucid claims to harvest over 100,000 credit card numbers daily — a figure that, even if exaggerated, represents a significant threat to global cybersecurity.
Protecting yourself
Individuals and organizations must exercise caution with unexpected messages, even those appearing to come from trusted sources. As attackers refine their tactics, awareness and proactive behavior remain the first line of defense.
Effective best practices include:
- Stay alert: Question unexpected messages, even from familiar contacts.
- Avoid risky clicks: Do not click on links or download attachments from unknown or unsolicited sources.
- Verify independently: Use official websites or trusted phone numbers to confirm suspicious communication.
- Be wary of urgency: Scammers often create a false sense of pressure — take a moment to think before acting.
- Keep devices updated: Regularly install updates to operating systems and apps to patch security vulnerabilities.
These simple but effective steps can help protect personal information and prevent costly mistakes.




