Wireless network security is a subset of network security that involves designing, implementing, and ensuring security on wireless computer networks to protect them from unauthorized access and breaches. It involves strategies designed to preserve the confidentiality, integrity, and availability of wireless networks and their resources. Effectively implementing proper security strategies prevents threats like interception, data theft, and denial-of-service attacks from occurring.
To improve the security of your wireless network, explore the several types of network security protocols, the ways you can strengthen Wi-Fi networks, and the security measures targeted for particular settings. Also, examine the tools and solutions available for increasing your network resilience.
How Does Wireless Security Work?
Wireless security creates layers of defense by combining encryption, authentication, access control, device security, and intrusion detection to defend against illegal access and ensure network security. The process begins with the wireless network’s encryption methods like WPA2 or WPA3 being activated to scramble data transfers. With this step, the data is unreadable to unauthorized parties, even if intercepted.
Users or devices wanting to connect to the network would be prompted to verify their identities to confirm the legitimacy of the connection request, usually via a password. Access control rules then specify the users or devices permitted to access the network and the level of access based on user roles, device kinds, and explicit access rights.
The process continues by securing network devices via maintaining antivirus software, updating operating systems, and restricting the usage of administrator credentials to prevent unwanted access. The integrated intrusion detection and prevention systems (IDPS) and other tools monitor the network for any unusual activity or security breaches. These systems detect and respond to unauthorized access attempts, malware infections, and other threats in real time.
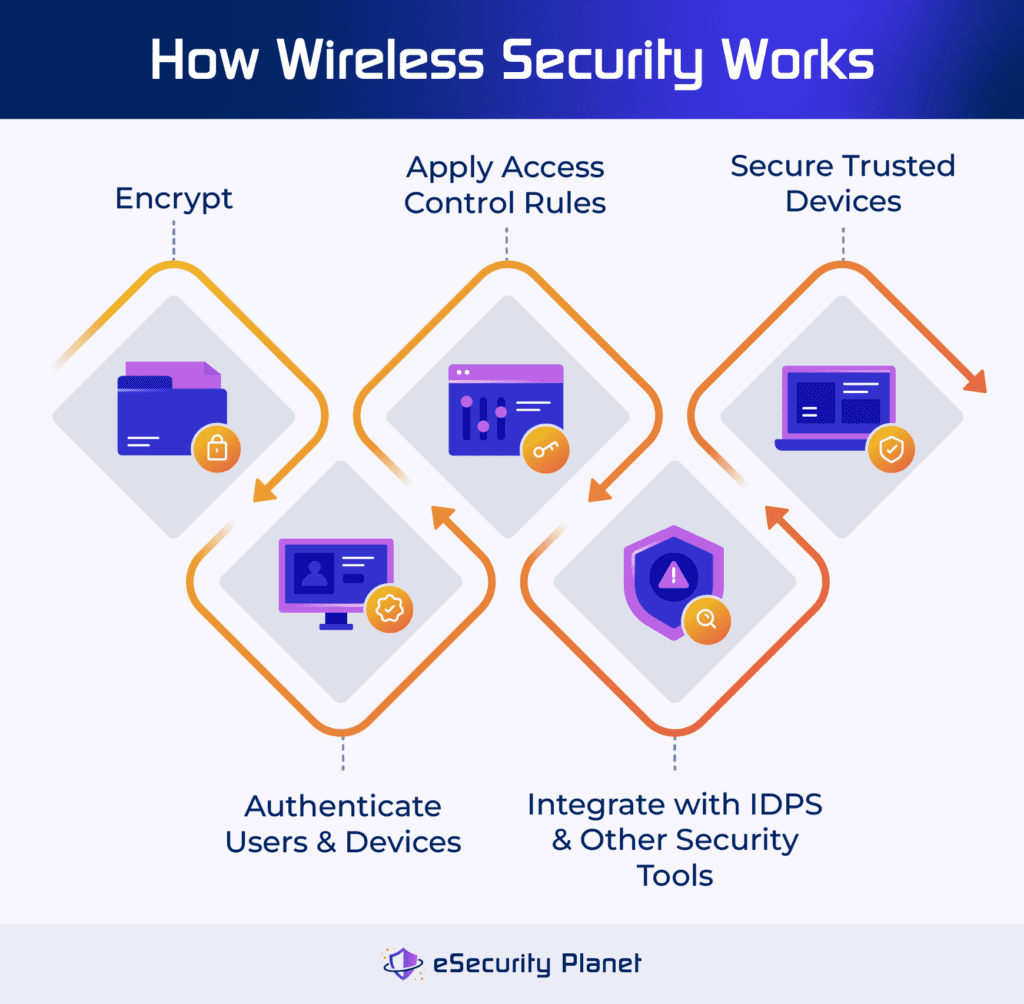
Specifically, wireless security involves the following:
- Conduct encryption: Converts data into a code that can be read only by authorized users with the appropriate key.
- Authenticate users and devices: Processes validated identities of individuals and devices that attempt to connect to the network.
- Apply access control rules: Define which users or devices can connect to the network and what degree or level of access they have.
- Secure devices: Includes identifying trusted devices connecting to any network and sets any policies in other integrated security tools.
- Integrate with IDPS and other tools: Catch and block suspicious activities and security breaches in the network.
Wireless security addresses the vulnerabilities brought by wireless network data being transferred by radio waves, guarantees that data isn’t intercepted, and protects the network’s security and availability. To gain a deeper understanding of how wireless security works, explore the different encryption protocols used in wireless networks.
4 Types of Wireless Network Security Protocols
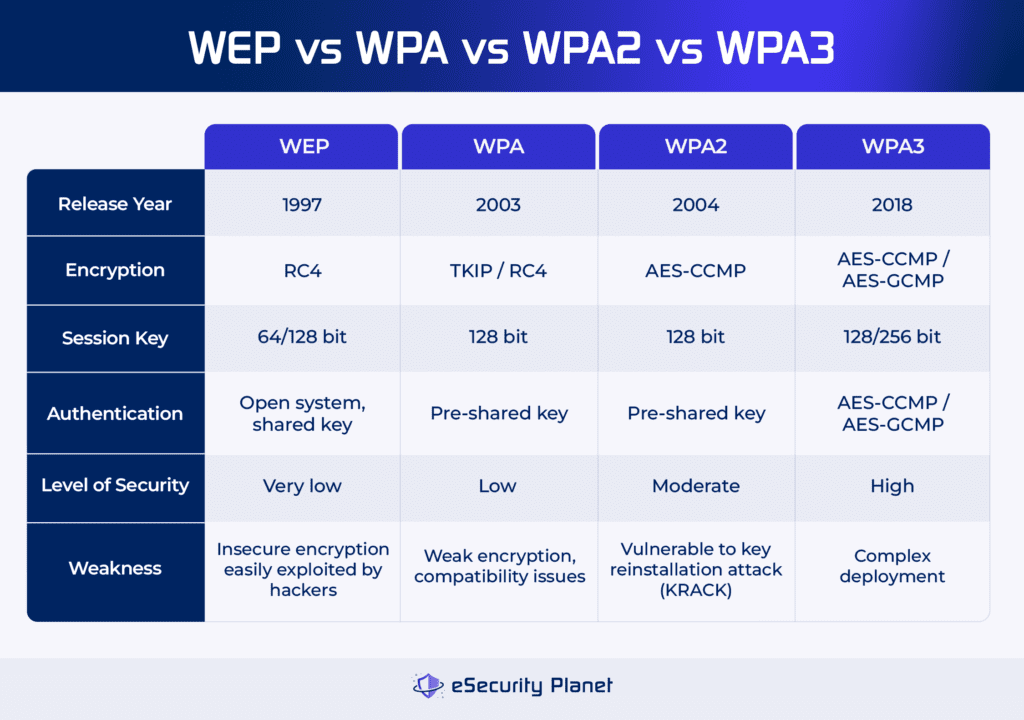
WEP, WPA, WPA2, and the latest WPA3 are the four types of wireless network security protocols, each with increasing levels of security. While WPA2, which uses AES encryption, is commonly used, WPA3 provides additional security features such as stronger encryption and attack defense. These protocols determine the users and device’s access level. Regardless of the protocol used, you need a strong security to protect wireless networks and sensitive data.
Wired Equivalent Privacy (WEP)
WEP developed in 1997, was designed to secure wireless networks using encryption and access restriction. However, its reliance on the insecure RC4 encryption and shared key authentication made networks vulnerable to attack. While WEP initially provided encryption similar to wired networks, its flaws were widely exploited by hackers, making it obsolete.
The protocol’s discontinuation created more robust alternatives, such as WPA (Wi-Fi Protected Access). Despite its flaws, WEP’s simplicity and widespread adoption originally drew attention, but its inherent vulnerabilities eventually overshadowed its benefits, emphasizing the significance of constantly updating wireless security standards.
Wi-Fi Protected Access (WPA)
WPA, launched in 2003, emerged as an effective successor to WEP, addressing its flaws. WPA uses the temporal key integrity protocol (TKIP) encryption to improve key management and integrity checks. It has two modes: WPA-Personal for home networks and WPA-Enterprise for enterprises that use RADIUS servers.
WPA’s 128-bit encryption provides enhanced protection over WEP’s weaker encryption standards; however, it’s still comparably weaker than WPA2 resulting in potential flaws and compatibility difficulties. Furthermore, adopting WPA may necessitate hardware modifications, providing a problem for users with older equipment.
Wi-Fi Protected Access II (WPA2)
WPA2, released in 2004, is the most popular wireless security standard that uses the AES encryption technique to provide strong security. Its advantages over WPA include better administration and lower vulnerability to assaults. WPA2 is widely adopted as the industry standard, ensuring device interoperability.
However, vulnerabilities such as the key reinstallation attack (KRACK) constitute a security risk. While appropriate for most home networks, difficulties arise in enterprise settings where sophisticated attacks are more widespread. Furthermore, older gear without WPA2 compatibility may require upgrades. Despite these issues, WPA2 remains critical to wireless network security, but with ongoing attempts to address growing threats and weaknesses.
Wi-Fi Protected Access III (WPA3)
WPA3, launched in 2018, provides greater encryption, protection against dictionary brute force attacks, and simpler device configuration via Wi-Fi Easy Connect. Despite these improvements, widespread acceptance is sluggish. WPA3 comes in three types: WPA3-Personal for home use, WPA3-Enterprise for organizational settings, and Wi-Fi Enhanced Open for non-password-protected networks.
While it enhances overall network security, drawbacks include deployment complexity, low user adoption, and compatibility issues with older devices and equipment. Despite its benefits, full-scale deployment of WPA3 has yet to occur, signaling a slow shift from older security protocols to this more modern standard.
5 Ways to Secure Wi-Fi Networks
Protect your Wi-Fi network from unauthorized access by using encryption methods, firewall tools, secured SSID software, VPN software, and wireless security software. These measures reduce the likelihood of security breaches, enhancing the safety and integrity of your network and critical data.
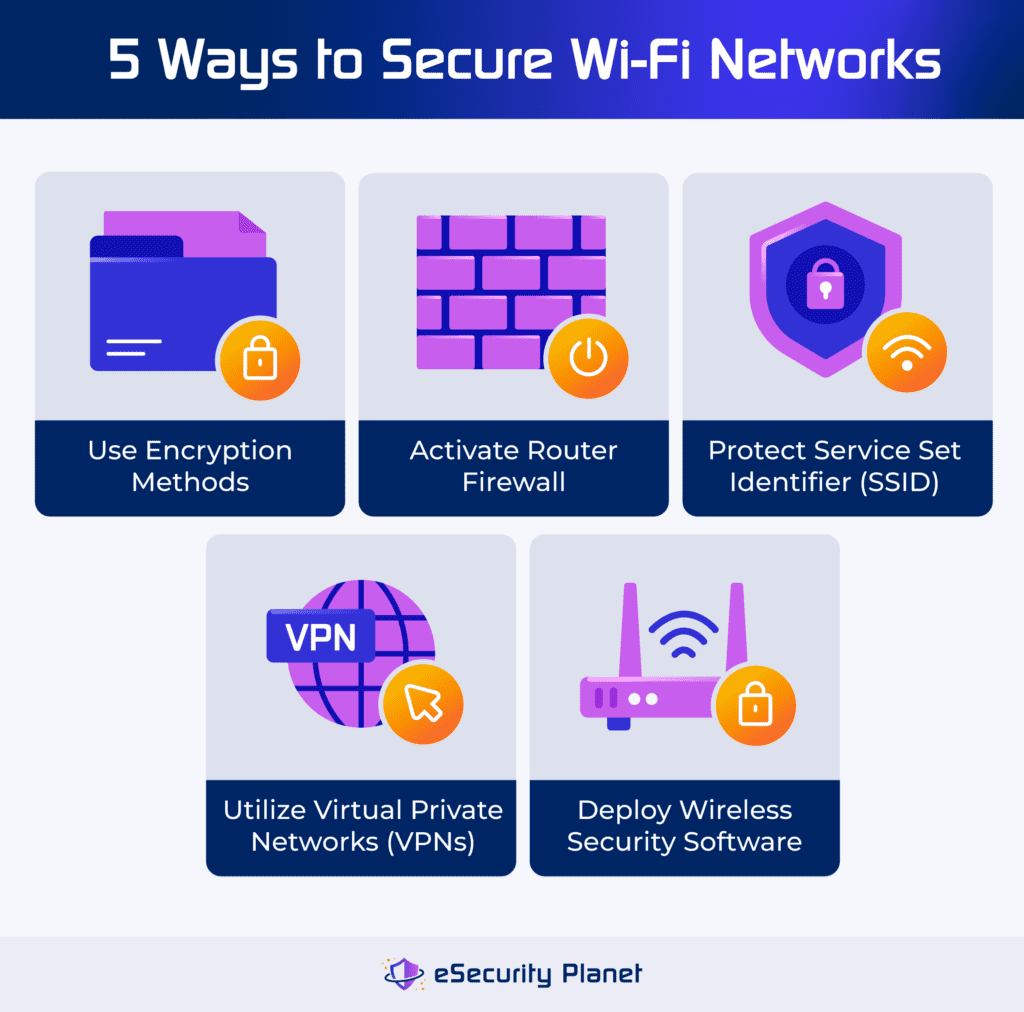
Use Encryption Methods
Encryption scrambles network data, making it harder for unauthorized users to gain access to important information. Encrypt your Wi-Fi network using WPA2 or WPA3 standards to protect your data. Update to the most recent encryption protocols for maximum network security and defense against potential threats and data breaches.
Activate the Router Firewall
Activate your router’s firewall to provide further protection against viruses, malware, and hackers. Check its status in your router settings to boost your network’s defenses. Segment sensitive areas of your network for increased security, and consider installing firewalls on all linked devices for complete protection.
Protect Your Service Set Identifier (SSID)
To secure wireless networks, keep personal information like your last name out of your SSID. Use unusual information to make it more difficult for hackers to target your network by employing techniques such as Evil Twin attacks. Obscuring your SSID also lessens the danger of falling victim to malicious access points and unauthorized access, hence improving the overall security of your wireless network.
Utilize Virtual Private Networks (VPNs)
A VPN protects your Wi-Fi network by encrypting your data, making it unreadable to prospective eavesdroppers on public Wi-Fi networks. Look for VPNs that use industry-standard AES-256 encryption and double the security by employing dependable open-source protocols for further protection. Many VPN apps have additional privacy features like ad blocking, split tunneling, and double VPN capability, which improve total network security and privacy.
Deploy a Wireless Security Software
Wireless security software improves Wi-Fi network security by incorporating capabilities such as performance analysis, network scanning, site surveys, spectrum analysis, heat mapping, audits, traffic analysis, packet sniffing, penetration testing, monitoring, and management. Using these features, users can identify vulnerabilities, detect unwanted access, and adopt effective security measures to protect their Wi-Fi networks from potential threats and breaches.
Wireless Security in Specific Environments
Wireless security varies between different settings, including home Wi-Fi networks, business wireless networks, and public networks. To protect against threats, each location requires tailored precautionary measures.
Securing Home Wi-Fi
Securing Wi-Fi networks at home not only protects your personal information, but also assures a stable and reliable network connection. Here are some tips to strengthen your home Wi-Fi network and reduce potential security risks:
- Secure passwords: Create a strong Wi-Fi password and update it on a regular basis to avoid unauthorized access.
- Verify devices: Check linked devices on a regular basis for any unusual activity or unauthorized access.
- Check the router’s credentials: Access the router’s web interface, choose administrative settings, and change the default login and password.
- Update devices: Keep router firmware and associated devices up to date to prevent vulnerabilities and ensure optimal security.
- Position the router in the best place: Place the router strategically for maximum coverage and least signal interference.
Securing Business Wireless Networks
Implementing effective wireless network security measures guards against cyber attacks while also ensuring regulatory compliance and customer trust. Below are some key ways for strengthening business networks and mitigating potential security threats:
- Restrict password sharing: Only share passwords with relevant personnel, and change them on a regular basis to ensure security.
- Upgrade encryption protocols: To improve network security, replace obsolete WEP encryption with more modern protocols like WPA2/WPA3.
- Segment business and guest networks: To protect your business’ sensitive data, direct guest and non-business activity to separate networks.
- Install firewalls: Employ firewalls to discover and prevent potentially hazardous programs.
- Limit DHCP connections: Regularly validate and delete illegal devices and consider working with a network security vendor for comprehensive network safety solutions.
Securing Public Networks
With the increased availability of public Wi-Fi hotspots in cafés, airports, and other public places, users must take proactive steps to safeguard their digital privacy and security. Here are five basic tips for safe and secure browsing on public networks.
- Use an antivirus software: Install and update antivirus software to detect and warn you of malware risks on public Wi-Fi networks.
- Avoid accessing sensitive information: Don’t access any confidential information or apps on unprotected public networks, even if you are using a VPN.
- Utilize VPNs: Turn on your VPN to encrypt data transmission over public Wi-Fi, preserving privacy and security by establishing a secure tunnel for data transfer.
- Be wary of phishing emails: Exercise caution while reviewing email content, validating suspicious links, and confirming sender identity.
- Disable file-sharing or auto-connect: Turn off automatic connectivity settings and file-sharing functions on devices to avoid unauthorized access on public Wi-Fi networks.
4 Authentication Mechanisms for Securing Wireless Networks
Authentication mechanisms strengthen security by requiring users to validate their identity through various methods, including multi-factor authentication (MFA), single sign-on (SSO), password-based authentication, and passwordless authentication.
Multi-Factor Authentication (MFA)
MFA is a security measure that requires two or more proofs of identity, such as a password plus a physical token or biometric data. It improves security by providing additional stages of verification beyond passwords, lowering the risk of unauthorized access and fighting against cyber threats such as phishing and credential theft. MFA alternatives also include authenticator apps, emails, and SMS.
Single Sign-On (SSO)
SSO allows users to log into one application instantly and get access to other applications across many platforms and domains. This reduces the need for multiple logins, improving the user experience and efficiency. A central domain handles authentication and shares the session with other domains, yet specific protocols may differ in how they handle session sharing.
Password-Based Authentication
Password-based authentication validates a user’s identity by asking them to provide both their username and password. These credentials are compared to stored data in the system’s database, and if they match, access is granted. While authentication is simple for users, it requires additional technical steps to maintain security and access control.
Passwordless Authentication
Passwordless authentication substitutes traditional password entry with newer, more secure ways. Biometrics, for example, examine unique qualities such as facial features. Others use possession factors such as one-time passcodes. Passwordless authentication improves security by eliminating the need for passwords and instead depending on biometrics, possession factors, and magic links delivered by email.
What Is Wi-Fi Security Software?
Wi-Fi security products are tools that defend wireless networks and devices from cyber dangers such as hackers, data interception, and unauthorized access. They work by encrypting data transmissions, enforcing access controls, and detecting and stopping harmful activity. Users install and configure these items on their Wi-Fi routers or other network devices. Newer solutions integrated into the cloud platforms provide advanced protection against breaches.
Wi-Fi security software covers Wi-Fi security and performance testing tools. These tools use tests and analysis to evaluate the status of a Wi-Fi network. They can locate vulnerabilities, monitor network speed and stability, detect unwanted access points, and evaluate overall network health. Below are some of the top Wi-Fi security platforms on the market:
- Wireshark: Best open-source network protocol analyzer (free download)
- AccessAgility WiFi Scanner: Best for tools integration ($100+ starting price)
- TamoGraph Site Survey: Best wireless site survey software tool ($500+ starting price)
4 Types of Wi-Fi Network Security Devices
There are four categories of Wi-Fi network security devices: active, passive, preventive, and UTM. Active devices manage traffic, passive devices detect threats, preventive devices scan for weaknesses, and UTM systems combine multiple security activities to provide full protection.
Active Device
While functioning similarly to their wired counterparts, active devices are designed for wireless environments. These include firewalls, antivirus, and content filtering devices. Firewalls filter incoming and outgoing wireless traffic, prevent unwanted access, and detect malicious packets. Antivirus scanners continuously scan wireless connections for malware threats. Content filtering devices limit access to specified websites or content while enforcing security regulations.
Passive Device
Passive devices, such as intrusion detection appliances, improve wireless network security by monitoring network traffic for suspicious activity. They examine data trends and abnormalities to detect potential dangers such as unauthorized access attempts or malware transmissions. By identifying and reporting on such instances, these devices give vital insights that allow network managers to take immediate action to reduce security risks and secure the network.
Preventive Device
Preventive devices, such as penetration testing tools and vulnerability assessment appliances, improve wireless network security by actively searching for potential security flaws. These devices do complete examinations of network infrastructure, discovering flaws that attackers could exploit. Preventive devices reinforce the network against cyber threats by detecting and fixing security defects before they’re exploited, reducing the likelihood of security breaches.
Unified Threat Management (UTM) System
UTM systems protect wireless networks by combining many security functions into a single hardware device. These devices, located at the network perimeter, act as gateways, providing comprehensive protection against malware, illegal infiltration, and other security threats. UTM appliances integrate many security services, such as firewall, anti-malware, and intrusion detection, to simplify maintenance and improve overall protection.
5 Common Wi-Fi Security Threats
DNS-cache poisoning, evil twin attacks, IP spoofing, piggybacking, and shoulder surfing all pose significant risks to Wi-Fi security. Recognizing and mitigating these Wi-Fi security threats is critical to protecting networks and sensitive data.
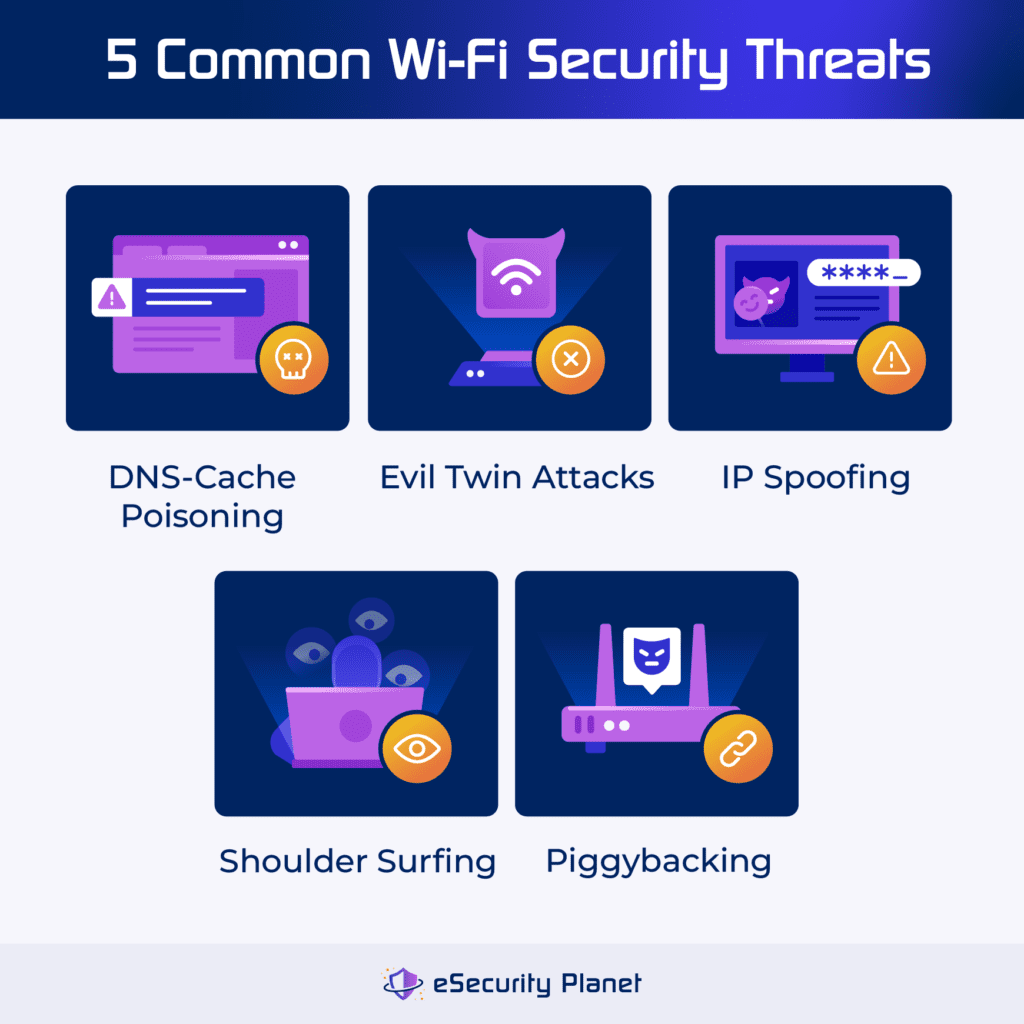
DNS-Cache Poisoning
DNS cache poisoning happens when a hacker replaces a legitimate website address with an imposter, causing visitors to unknowingly interact with the malicious site. This can lead to data theft or denial of service. Hackers use vulnerabilities to impersonate servers or flood caching servers with bogus replies.
Defense strategies: Controlling DNS servers, limiting queries over open ports, and adopting DNS software with built-in security all help to lessen the risk of DNS poisoning attacks.
Evil Twin Attacks
Evil Twin Attacks exploit public Wi-Fi flaws by impersonating legitimate networks. Hackers create bogus Wi-Fi access points, tempting people to connect unintentionally. Victims may then provide personal information, which hackers take.
Defense strategies: To protect yourself, avoid unsecured Wi-Fi and instead use password-protected personal hotspots, monitor for warning notifications, disable auto-connect features, avoid logging into private accounts on public Wi-Fi, use multi-factor authentication, visit HTTPS websites, and use a VPN for encrypted data transmission.
IP Spoofing
IP spoofing happens when a hacker replaces a packet’s original IP address with a fake one, frequently impersonating a legitimate source. This deceptive method can be used for criminal purposes, like identity theft. During the attack, the hacker intercepts the TCP handshake and sends a bogus confirmation with their device address and a falsified IP.
Defense strategies: Some methods include monitoring networks for strange activity, using stronger identity verification methods, firewall protection, transitioning to IPv6, implementing ingress and egress filtering, and utilizing Deep Packet Inspection (DPI).
Piggybacking
Piggybacking on Wi-Fi networks involves getting unwanted access to the internet by exploiting unencrypted signals. This activity, also known as Wi-Fi squatting, jeopardizes network security and can slow down internet connections.
Defense strategies: To avoid being a victim of piggybacking, protect Wi-Fi networks with strong passwords, keep an eye out for unusual activity, and think about utilizing a virtual private network (VPN) for encryption on public Wi-Fi networks. Use strong, unique passwords, and be vigilant against strange individuals near Wi-Fi access points.
Shoulder Surfing
Shoulder surfing occurs when someone steals critical information while you are using electronic gadgets in public locations. Attackers seek to acquire sensitive information, such as credit card numbers and passwords, in order to commit identity theft or financial crime.
Defense strategies: To prevent shoulder surfing, use difficult, unique passwords, avoid repeating passwords across accounts, use two-factor authentication, and use a virtual private network (VPN) while connecting to public Wi-Fi networks. These safeguards help prevent unauthorized access and personal information from being compromised.
Explore the top Wi-Fi security threats to stay informed about the common vulnerabilities and their potential impact.
Wireless Network Monitoring & Management Tools
Network monitoring and management include a number of tools, such as network discovery, performance, security, and compliance. You may determine the most suitable tool by evaluating your network size, budget, desired functionality, and IT team expertise.
Network Discovery Tools
Network discovery tools help secure wireless networks by scanning and mapping the network topology and devices. They use protocols such as SNMP, ICMP, ARP, and LLDP to identify wireless nodes. These tools display network topology and detect changes or abnormalities, resulting in thorough data for effective network administration and monitoring.
Recommended tool: LogicMonitor is a cloud-based infrastructure monitoring platform that focuses on basic network monitoring services. It provides automatic device discovery, machine learning warnings, hardware health monitoring, network mapping, integrations, and traffic analysis. Users can take advantage of a 14-day free trial to explore its potential.
Network Performance & Availability Software
Network performance and availability tools assess network quality, speed, dependability, and capacity while identifying bottlenecks, failures, and outages. They assess measures such as bandwidth, latency, packet loss, jitter, throughput, and signal strength to notify administrators of any anomalies. These tools maintain a stable and efficient network infrastructure as they handle issues quickly, ensuring optimal performance and availability.
Recommended tool: ManageEngine is a network monitoring tool that excels at analyzing traffic, tracking network performance, and managing firewalls, IP addresses, and switch ports. OpManager Plus provides extensive network analysis, whereas Site24x7 focuses on application performance and website monitoring. Users can start with a free edition of OpManager or get a 30-day free trial.
Wireless Network Security & Compliance Tools
Wireless network security and compliance tools protect networks against unauthorized access, harmful assaults, data breaches, and legal infractions. They look for vulnerabilities, track network traffic and behavior, identify and prevent intrusions, and encrypt and authenticate data. They also audit and prepare reports to verify compliance with regulatory standards and industry rules for a comprehensive protection.
Recommended tool: Datadog is known for its strong network security capabilities and regulatory compliance, especially in highly regulated industries. To secure data privacy and regulatory compliance, it uses strong encryption, role-based access controls, and comprehensive audit trails. It offers a 14-day free trial period.
Looking for more network security tool alternatives? Check out our review of the top network monitoring tools.
Bottom Line: Improve Your Wireless Networks Security Now
Wireless security protocols have evolved greatly over the years, and networks using WPA2 or WPA3 are off to a good start toward better security. By using the latest protocols, tools and practices, you can significantly improve the security of your wireless network. Ensure that you have strong authentication, encryption, and access control procedures in place. Keep up with the newest tools and strategies to protect your network from malicious attacks.
While no single tool can guarantee 100% security, it’s recommended that you begin your network security strategy by learning about and implementing network security solutions.




